
Cross-chain messaging protocols are the backbone of blockchain interoperability, enabling digital assets and data to flow seamlessly between disparate networks. However, their complexity and the high value at stake make them prime targets for sophisticated exploits. As the DeFi ecosystem matures, understanding and proactively addressing cross-chain messaging risks is no longer optional, it’s essential for protocol survival and user trust.

Why Cross-Chain Messaging Protocols Face Elevated Risks
Unlike single-chain DeFi protocols, cross-chain systems must coordinate consensus, message validation, and asset transfers across multiple blockchains. This introduces a broader attack surface and unique vectors for exploits, as seen in high-profile incidents like the Ronin Bridge and Mango Markets hacks. The most prevalent threats include:
- Smart contract flaws that enable forged transactions or unauthorized minting
- Validator compromise leading to asset theft
- Oracle manipulation affecting price feeds and transaction logic
- Replay attacks due to missing unique identifiers
- Centralization risks that create single points of failure
The resulting vulnerabilities can lead to catastrophic losses, with bridge exploits alone accounting for billions in stolen assets over the past two years. That’s why robust, layered risk mitigation is critical for any DeFi application operating in a cross-chain environment.
Comprehensive Cross-Chain Smart Contract Audits Using Specialized Tools
The first and most foundational defense is a rigorous audit process, tailored specifically to the intricacies of cross-chain messaging. Generalist smart contract audits are insufficient here. Instead, protocols should leverage advanced platforms such as ChainSecurity and Halborn, which specialize in both automated and manual analysis of cross-chain codebases.
These tools go beyond surface-level checks, scrutinizing:
- Signature replay vulnerabilities unique to cross-chain message handling
- Improper message validation that could enable forged or duplicate transactions
- Logic flaws in bridge contracts that could be exploited for unauthorized withdrawals or asset minting
By incorporating both static analysis and hands-on review by experienced security engineers, these audits uncover subtle bugs that automated scanners alone might miss. Regular re-auditing is also essential, especially after protocol upgrades or when integrating with new chains. For a deeper dive into the necessity of specialized audits for cross-chain security, see this Chainlink analysis.
Real-Time Risk Monitoring and Alerting Platforms
Even the most thorough audit cannot guarantee perpetual safety in the face of evolving threats. This is where real-time monitoring comes into play. Solutions like Forta and Chainlink CCIP Risk Scanner provide continuous, on-chain surveillance for anomalous cross-chain activity.
These platforms are designed to detect:
- Unusual transaction patterns that may signal an exploit in progress
- Unauthorized contract interactions or sudden changes in validator behavior
- The emergence of new threat vectors targeting cross-chain bridges or messaging layers
By issuing instant alerts to protocol teams and the wider community, these systems enable rapid response, often before attackers can fully realize their gains. Integrating such monitoring is now a best practice for any serious DeFi protocol, as highlighted in recent industry risk assessments.
Top Strategies & Tools for Cross-Chain Messaging Risk Mitigation
-

Comprehensive Cross-Chain Smart Contract Audits Using Specialized Tools (e.g., ChainSecurity, Halborn): Regularly conduct in-depth audits of cross-chain messaging contracts and bridge codebases with advanced automated and manual analysis platforms to identify logic flaws, signature replay vulnerabilities, and improper message validation. These audits help uncover hidden risks before deployment, leveraging the expertise of leading security firms and platforms recognized for their work in DeFi security.
-
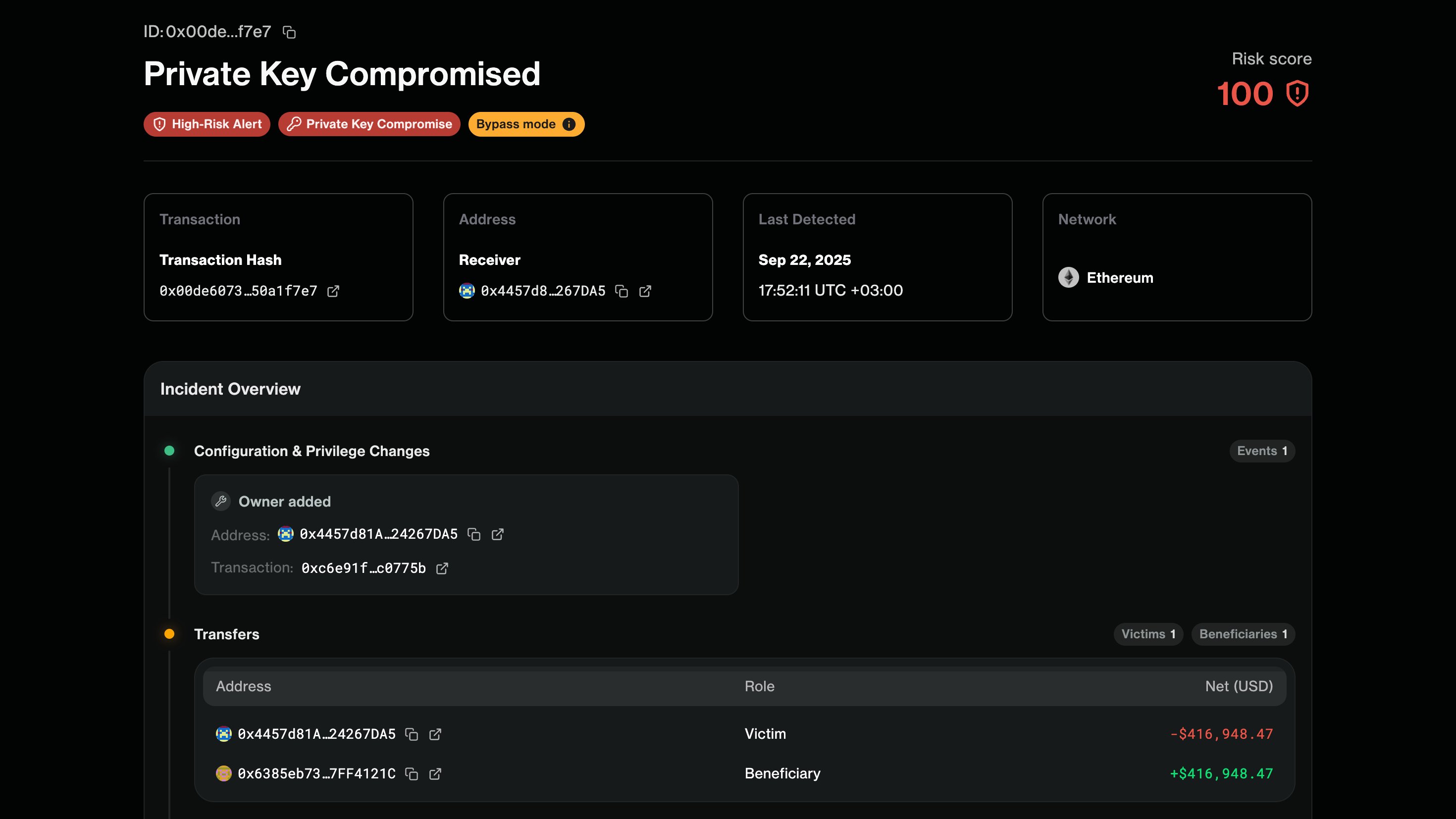
Real-Time Risk Monitoring and Alerting Platforms (e.g., Forta, Chainlink CCIP Risk Scanner): Deploy on-chain monitoring solutions that provide continuous surveillance for anomalous cross-chain activity, unauthorized contract interactions, and emerging threat patterns. These platforms enable rapid response to potential exploits in DeFi protocols by offering real-time alerts and actionable intelligence.
Beyond technical detection, real-time monitoring platforms also support transparency and user confidence. By making risk signals publicly accessible or integrating them with governance mechanisms, protocols can crowdsource vigilance and incentivize rapid patching. This community-driven approach is increasingly vital as the sophistication of cross-chain exploits accelerates.
Consider the recent trend of integrating automated alerting directly into protocol operations. For example, a sudden spike in cross-chain withdrawal attempts can trigger temporary rate-limiting or even halt bridge operations until human review confirms safety. This blend of automation and human oversight is proving to be the most resilient defense against fast-moving attacks.
Best Practices: Layered Security for Cross-Chain DeFi
To maximize defense-in-depth, leading DeFi teams combine both specialized audits and real-time monitoring in their security stack. Here’s how these strategies work together:
- Pre-deployment: Comprehensive audits using ChainSecurity or Halborn uncover latent vulnerabilities before code goes live.
- Ongoing operations: Forta and Chainlink CCIP Risk Scanner provide 24/7 surveillance, flagging suspicious activity and empowering teams to act quickly.
- Incident response: Automated alerts feed into protocol governance, enabling emergency measures like pausing contracts or updating validator sets.
This layered approach significantly reduces the window of opportunity for attackers, making it far harder for exploits to go undetected or unaddressed.
Empowering Developers and Users
Security is not just a backend concern. Developers should openly communicate their use of audit and monitoring solutions, while users should look for these signals as part of their due diligence. Transparency builds trust – protocols that publish audit results, disclose monitoring integrations, and foster open communication are better positioned to attract capital and community support.
For those building or interacting with cross-chain DeFi applications, here are two actionable takeaways:
Top Strategies & Tools to Mitigate Cross-Chain Messaging Risks
-

Comprehensive Cross-Chain Smart Contract Audits Using Specialized Tools (e.g., ChainSecurity, Halborn): Regularly conduct in-depth audits of cross-chain messaging contracts and bridge codebases with advanced automated and manual analysis platforms to identify logic flaws, signature replay vulnerabilities, and improper message validation. These leading security firms utilize both static and dynamic analysis to uncover hidden weaknesses before deployment, significantly reducing the risk of costly exploits.
-

Real-Time Risk Monitoring and Alerting Platforms (e.g., Forta, Chainlink CCIP Risk Scanner): Deploy on-chain monitoring solutions that provide continuous surveillance for anomalous cross-chain activity, unauthorized contract interactions, and emerging threat patterns. These platforms enable rapid response to potential exploits in DeFi protocols, helping teams detect and mitigate attacks before significant damage occurs.
As cross-chain interoperability becomes the norm, only those protocols that prioritize specialized audits and real-time monitoring will earn lasting credibility. In DeFi, resilience is not static – it’s a continuous process of learning, adapting, and investing in the right tools. With billions at stake, nothing less will do.






