Cross-chain messaging is transforming the blockchain landscape, enabling smart contracts and decentralized apps (dApps) to interact seamlessly across multiple networks. Yet, as interoperability increases, so do the security risks. For blockchain developers, integrating advanced risk scanners into cross-chain messaging systems is not just a best practice – it’s rapidly becoming essential for safeguarding user assets and maintaining trust in decentralized ecosystems.
![]()
Why Cross-Chain Messaging Needs Dedicated Risk Scanners
Bridges and cross-chain protocols are prime targets for hackers, as they often serve as the critical infrastructure connecting siloed networks. According to recent research from the XChainWatcher project, vulnerabilities in cross-chain bridges have led to high-profile exploits like those on Ronin and Nomad. Attackers exploit weaknesses in message validation, delayed confirmations, or flawed business logic. The result? Millions of dollars lost and shaken community confidence.
This is where specialized blockchain risk scanner integration comes into play. Modern scanners do more than just monitor transactions – they leverage real-time analytics, pattern recognition, and even AI-driven graph mining to detect suspicious behaviors before damage can be done. Tools like BridgeShield employ heterogeneous graph attention networks to model complex attack vectors unique to cross-chain environments (see details). By adopting these solutions early in the development process, teams can proactively address vulnerabilities instead of reacting after an incident.
Key Tools for Securing Cross-Chain Messaging Protocols
The current generation of cross-chain messaging risk tools offers developers a suite of options tailored for different threat models:
Top Risk Scanners for Cross-Chain Messaging
-

Chainlink Cross-Chain Interoperability Protocol (CCIP): CCIP is a robust protocol for secure cross-chain communication, offering built-in security features and universal standards for dApp developers. It enables seamless and safe messaging across multiple blockchains. Learn more.
-

Wormhole: Wormhole is a leading cross-chain message-passing protocol supporting secure data transfers between blockchains. It is actively working on integrating zero-knowledge proofs to further enhance trustless verification and security. Learn more.
-
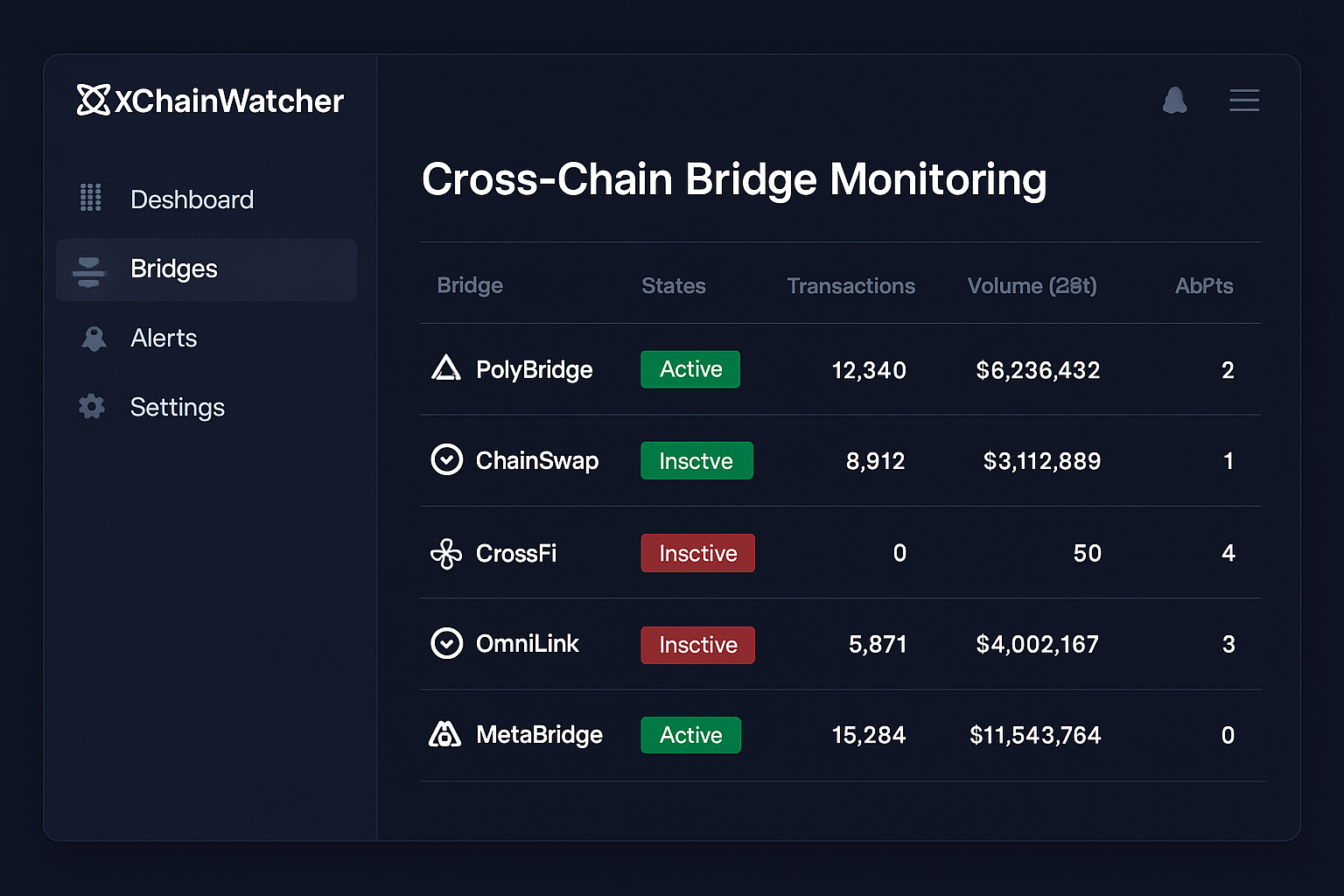
XChainWatcher: This real-time monitoring tool detects attacks on cross-chain bridges using a Datalog engine. XChainWatcher has successfully identified major exploits like the Ronin and Nomad bridge attacks, making it a trusted solution for live threat detection. Learn more.
-

BridgeShield: BridgeShield leverages heterogeneous graph attention networks to model and detect complex cross-chain attack patterns. Its advanced analytics deliver high accuracy in identifying real-world threats across blockchain bridges. Learn more.
-
Cross-Chain Security Analyzer: This analyzer provides comprehensive vulnerability scanning, smart contract analysis, and real-time monitoring tailored for cross-chain environments. It helps spot and mitigate risks before they escalate. Learn more.
-

HighGuard: HighGuard specializes in monitoring business logic violations in cross-chain smart contracts, operating without code instrumentation or extra gas costs. It effectively detects deviations from expected contract behaviors. Learn more.
- XChainWatcher: Real-time attack detection using Datalog engine models; proven effective against major bridge hacks.
- BridgeShield: Utilizes advanced graph mining to identify subtle attack patterns across heterogeneous chains.
- Cross-Chain Security Analyzer: Offers smart contract analysis, bridge vulnerability scanning, and replay attack detection (see full feature set).
- HighGuard: Business logic monitoring without code instrumentation or gas overhead – ideal for enforcing custom rules across chains.
A Developer-Focused Approach: Integration Strategies That Work
The path to robust bridge security starts with choosing protocols that prioritize built-in safety. For example, Chainlink’s Cross-Chain Interoperability Protocol (CCIP) offers a standardized framework with security at its core (learn more here). But even when using established protocols, developers must layer on real-time monitoring and continuous scanning tools throughout their deployment pipeline.
A successful integration typically follows these steps:
This multi-layered defense ensures that both known vulnerabilities (like replay attacks or invalid proofs) and novel threats (such as business logic violations) are caught early – ideally before any funds are at risk.