
Cross-chain bridges have become the backbone of blockchain interoperability, enabling seamless movement of assets and data between otherwise siloed networks. Yet, their explosive growth has painted a massive target on their backs for sophisticated attackers. In 2025, bridge exploits continue to dominate crypto headlines, with cumulative losses soaring into the billions. But why are these protocols so uniquely vulnerable? The answer lies in a triad of structural risks: centralized custodial points, opaque smart contract logic, and an exceptionally complex cross-chain attack surface.

Centralized Custodial Points: The Lucrative Single Point of Failure
Most cross-chain bridges rely on a centralized pool or multi-signature wallet to hold the assets backing their wrapped tokens. This design is inherently risky. When users send tokens across chains, the original assets are locked in a smart contract or controlled by a small set of validators, often just 3 to 9 signers. If attackers compromise these custodians (as seen in the $625 million Ronin Network breach), they gain access to the entire vault, enabling them to drain funds and render all corresponding wrapped tokens worthless.
This centralization risk is exacerbated by inadequate operational security and poor key management practices among validator operators. Social engineering, phishing, and insider threats become existential risks when so much capital is consolidated in one place. As a result, bridges present an irresistible honeypot for hackers seeking maximum payoff with minimal breach points.
Opaque Smart Contract Logic: Hidden Dangers Beneath the Surface
The second critical vulnerability is opacity, many bridges operate with smart contract code that is either closed-source or insufficiently audited. Even when code is public, documentation may be sparse and operational details undisclosed, making it difficult for independent researchers or users to assess real-time risks.
This lack of transparency allows subtle bugs or overlooked logic errors to persist undetected until exploited in the wild. For example, in the $325 million Wormhole hack, an unpatched vulnerability allowed attackers to mint unbacked assets by bypassing validation checks, an issue that could have been caught with more rigorous code review and open scrutiny.
The combination of complex logic and limited visibility means that security researchers must often reverse-engineer contracts or rely on incomplete information when evaluating bridge safety. This opacity not only delays detection but also hinders effective incident response when breaches occur.
Complex Cross-Chain Attack Surface: Exploits Beyond Standard Audits
The third, and perhaps most insidious, risk stems from the intricate logic required for cross-chain operations. Unlike single-chain protocols, bridges must coordinate state changes across multiple blockchains with varying consensus mechanisms and transaction finality guarantees. This complexity introduces novel vulnerabilities such as replay attacks (where messages are maliciously reused across chains), message validation failures, signature forgery exploits, and race conditions unique to asynchronous systems.
Standard audits often miss these edge cases because they focus on isolated contract logic rather than holistic system interactions spanning multiple networks. Attackers exploit this gap by crafting sophisticated multi-stage exploits that evade traditional defenses.
- Replay Attacks: Malicious reuse of valid messages across different chains.
- Message Validation Failures: Improper checks allow forged or altered messages to trigger asset transfers.
- Signature Forgery: Exploiting weaknesses in cryptographic verification schemes used by bridge validators.
This expanding attack surface ensures that even well-audited bridges remain at risk unless they adopt advanced cross-chain threat modeling and continuous monitoring strategies.
If you want a deeper technical breakdown, including real-world case studies, see our analysis at Why Cross-Chain Bridges Get Hacked: Common Attack Vectors and How To Mitigate Them.
These three vulnerabilities, centralized custodial points, opaque smart contract logic, and the complex cross-chain attack surface, are not theoretical risks. Each has been repeatedly exploited in high-profile bridge hacks, resulting in catastrophic losses for users and protocols alike. The persistent clustering of assets in centralized pools means that a single successful breach can undermine the entire economic integrity of a DeFi ecosystem, as attackers are able to drain hundreds of millions of dollars with one exploit.
Opacity compounds these dangers by obscuring both the existence and scope of vulnerabilities until it is too late. When bridge operators fail to disclose operational practices or keep codebases private, the broader security community cannot provide oversight or early warnings. This lack of transparency is antithetical to the open ethos of blockchain and creates fertile ground for zero-day exploits.
The multifaceted attack surface further complicates defense. Cross-chain bridges must process asynchronous events, validate messages from disparate consensus systems, and maintain atomicity across incompatible platforms. This confluence generates a labyrinthine threat model where traditional audit checklists fall short. As attackers grow more sophisticated, leveraging multi-chain replay vectors or exploiting signature aggregation bugs, protocols that do not invest in continuous monitoring, formal verification, and adversarial testing will remain vulnerable.
Mitigation: Can Bridge Security Ever Catch Up?
While no solution is bulletproof, several emerging approaches aim to address these core risks:
- Decentralized Validation Networks: Expanding validator sets and employing distributed key management (e. g. , threshold signatures) reduce single points of failure but introduce new coordination challenges.
- Transparent Codebases and Real-Time Audits: Open-sourcing smart contracts combined with ongoing bug bounty programs incentivize external review and rapid vulnerability disclosure.
- Advanced Cryptography: Techniques like zero-knowledge proofs can minimize trust assumptions by verifying cross-chain state transitions without exposing sensitive data or requiring centralized validators.
- Continuous Monitoring and Incident Response: Automated risk scanners and real-time alerting platforms help detect anomalous activity before funds are irreversibly lost.
The industry’s response to recent bridge hacks has been swift but uneven. Some protocols have migrated toward decentralized architectures or implemented layered security models; others remain dangerously exposed due to inertia or resource constraints. For developers building new bridges, or users evaluating which protocols to trust, the key is rigorous due diligence on custodial design, code transparency, and incident history.
Core Risks of Cross-Chain Bridges Illustrated
-

Centralized Custodial Points: Most cross-chain bridges rely on centralized pools or multi-signature wallets to hold large amounts of locked assets, making them lucrative single points of failure for attackers. The Ronin Network hack (March 2022) exemplifies this risk, with over $625 million stolen after attackers compromised validator keys.
-
Opaque Smart Contract Logic: Many bridges lack transparent, well-audited code and clear operational disclosures, obscuring potential vulnerabilities and making it difficult for users and researchers to assess real-time risks. The Wormhole bridge exploit (February 2022) is a prime example, where an undetected flaw led to a $325 million loss.
-
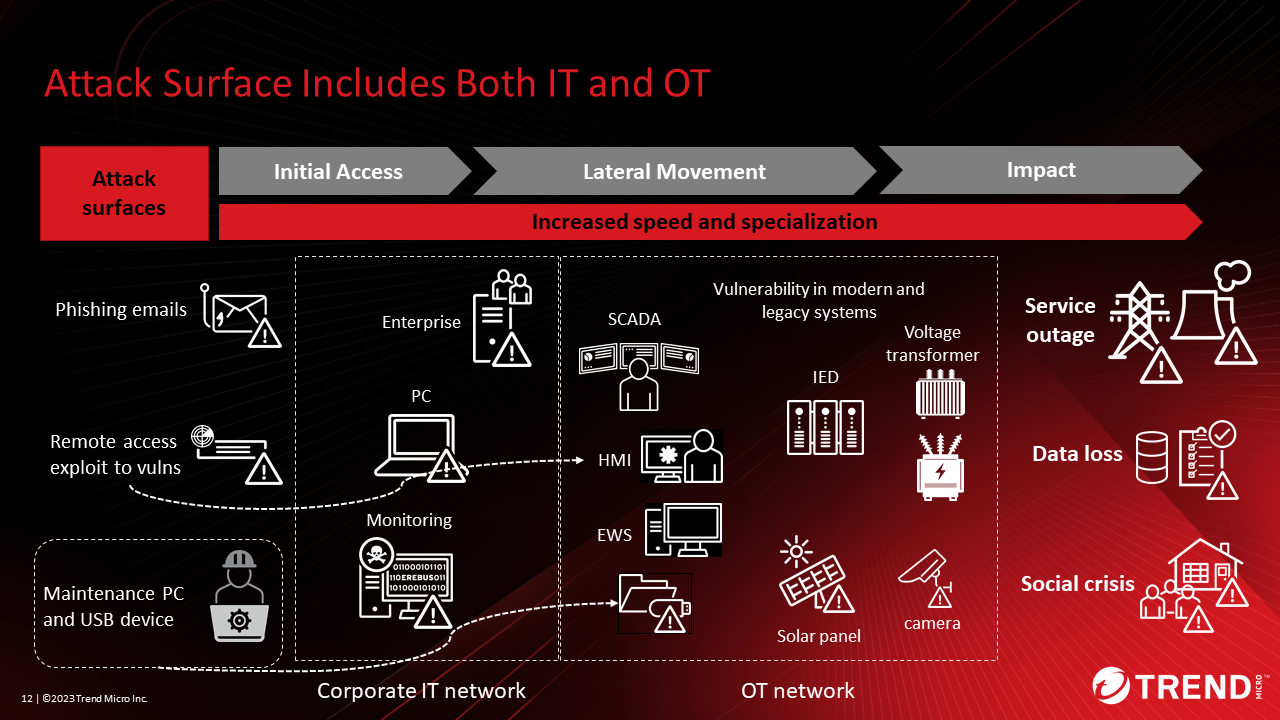
Complex Cross-Chain Attack Surface: The intricate logic required for interoperability introduces novel security flaws—such as replay attacks, message validation failures, and signature forgery—that are often missed in standard audits and have been exploited in recent high-profile hacks. This complexity increases the likelihood of undetected vulnerabilities across connected chains.
The future of blockchain interoperability depends on addressing these foundational weaknesses. As long as bridges aggregate massive value into fragile trust models while hiding their inner workings behind closed doors, they will remain irresistible honeypots for hackers. Only through radical transparency, robust decentralization, and relentless adversarial testing can the sector hope to mitigate these existential threats.
If you’re interested in a detailed breakdown of how trust assumptions in cross-chain bridges create hidden risks, including real-world examples, see our deep dive at How Trust Assumptions in Cross-Chain Bridges Create Security Risks.






