Cross-chain messaging protocols have become the backbone of blockchain interoperability, letting assets and data flow seamlessly between networks. Yet with this innovation comes a new set of cross-chain messaging risks that are both complex and evolving. If you’re building, investing in, or researching these protocols, understanding how to assess their security risks is essential for safeguarding value and trust across chains.
Why Cross-Chain Messaging Protocols Are High-Value Targets
The surge in cross-chain activity has made bridges and messaging layers prime targets for attackers. These systems often hold or route vast sums of digital assets, making any vulnerability a potential jackpot. According to recent research, exploits like the Ronin Bridge hack ($625 million) and Nomad Bridge incident ($190 million) were not isolated events but part of a broader pattern exploiting protocol weaknesses (source).
Why are these protocols especially risky?
- Complexity: Multiple chains, consensus models, and smart contract interactions create a wider attack surface.
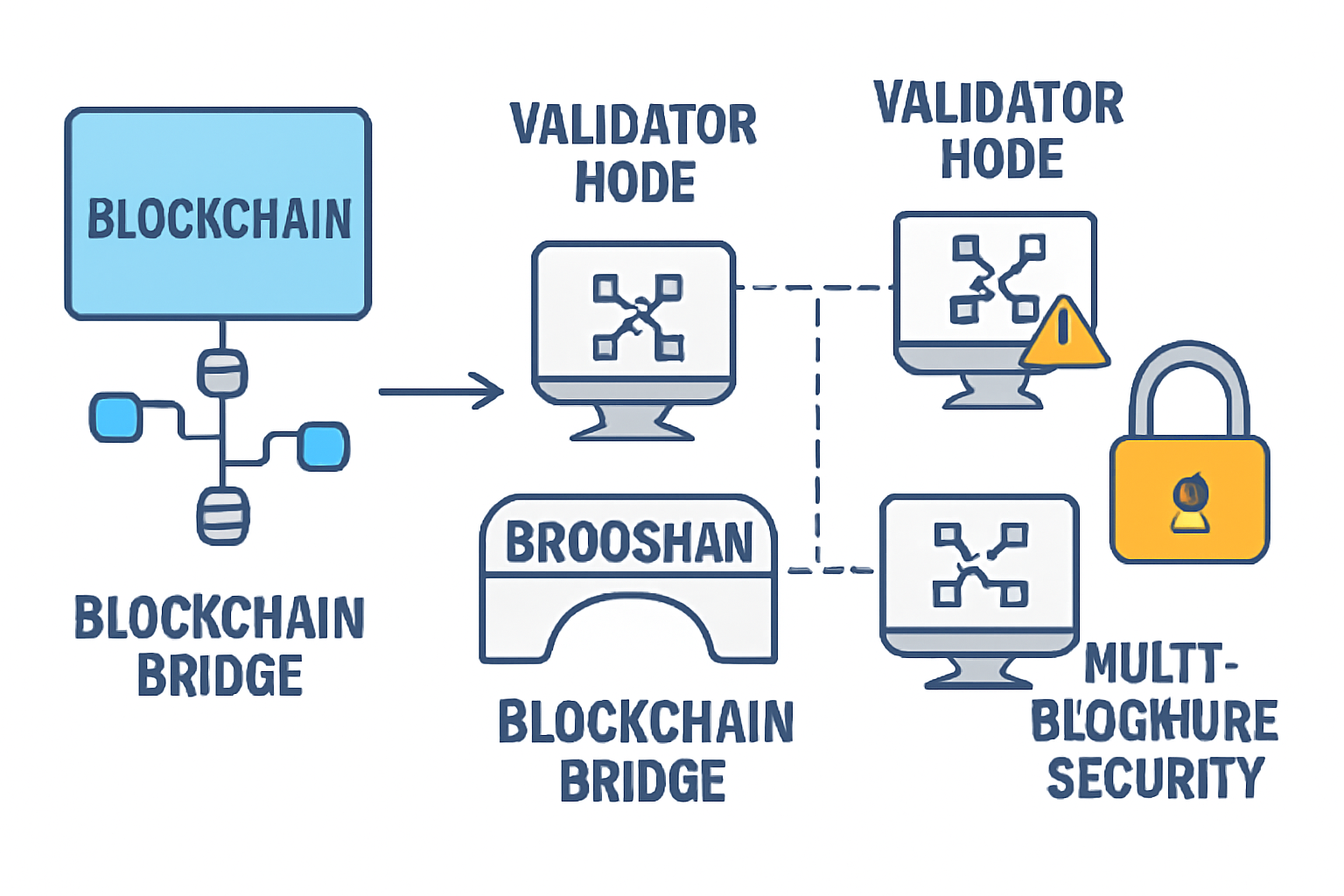
- Centralization: Many rely on a handful of validators or multisig schemes, a tempting single point of failure.
- Lack of Standardization: Ad-hoc solutions often lack rigorous security frameworks.
The Seven Most Critical Cross-Chain Vulnerabilities
Seven Most Critical Cross-Chain Bridge Vulnerabilities
| Vulnerability | Explanation | |
|---|---|---|
| Centralized Validators and Multisignature Risks | Reliance on a small set of validators creates single points of failure; if compromised, attackers can control the bridge. | 🔑 |
| Smart Contract Vulnerabilities | Bugs or oversights in complex bridge contracts can be exploited to drain funds or manipulate transactions. | 🐞 |
| Replay Attacks | A valid transaction on one chain can be duplicated on another, causing unintended asset transfers or double-spends. | 🔁 |
| Fake Asset Minting | Attackers mint fraudulent tokens on one chain and bridge them, undermining trust in the bridge’s assets. | 🪙 |
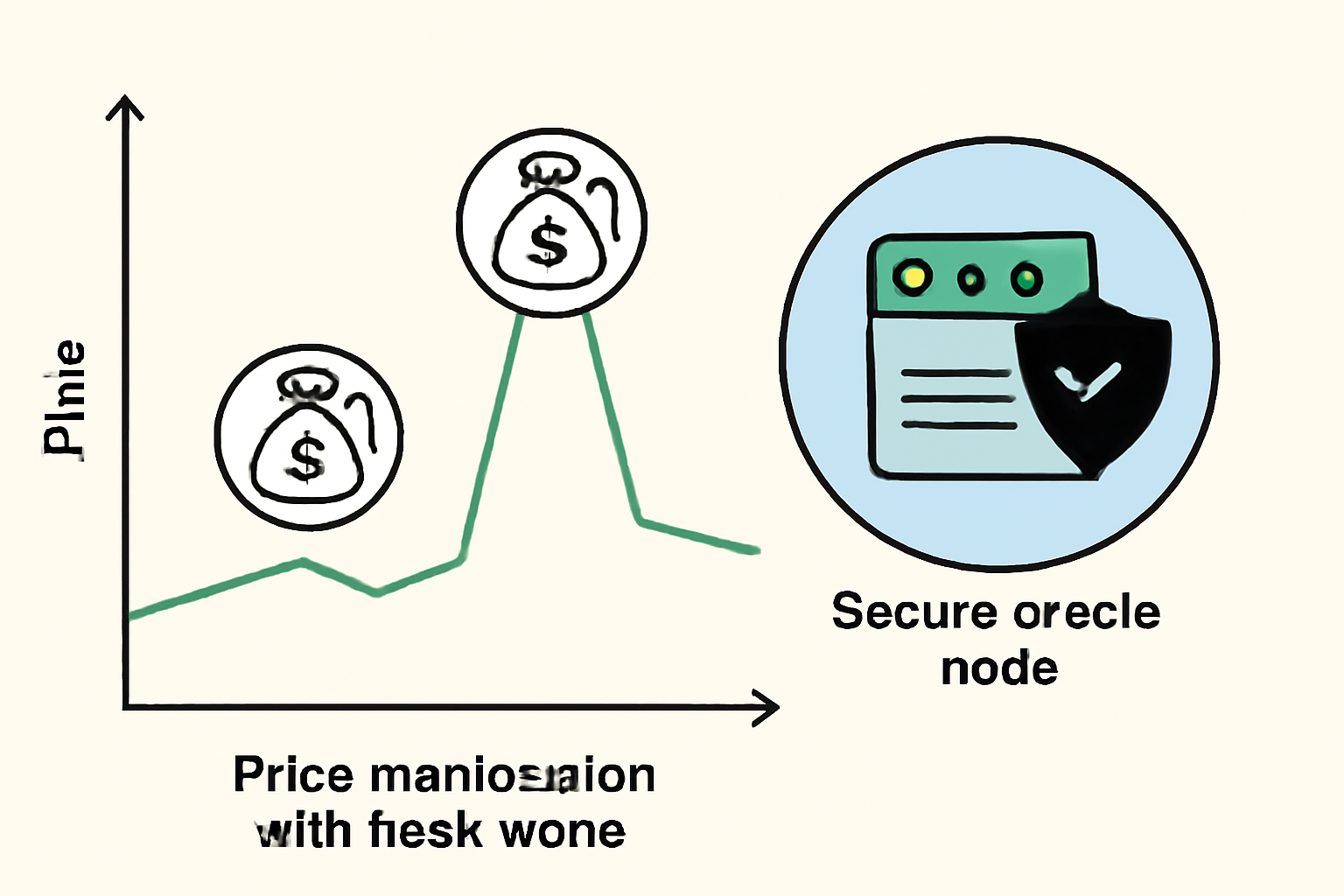
| Economic Attacks | Manipulation of price feeds or oracles (e.g., via flash loans) can destabilize protocols and trigger liquidations. | 📉 |
| Off-Chain Component Risks | Off-chain infrastructure (e.g., relayers, oracles) may be targeted, leading to message tampering or downtime. | 🌐 |
| Lack of Standardization | Inconsistent protocols between bridges can cause interoperability issues and make vulnerabilities harder to trace. | ⚠️ |
A recent Chainlink report highlights seven major vulnerabilities that plague cross-chain bridges (source). Here’s what you need to watch for:
- Centralized Validators and Multisig Risks: When control is concentrated among a few actors, attackers need only compromise a subset to take over the bridge. The Ronin hack is a textbook example.
- Smart Contract Bugs: Complex logic increases the chance of exploitable errors, Nomad’s faulty initialization allowed anyone to mimic valid transactions.
- Replay Attacks: Transactions replayed across chains can trigger unintended consequences if message uniqueness isn’t enforced.
- Fake Asset Minting: Weak validation lets attackers mint unbacked tokens on destination chains, undermining trust in the bridge’s integrity.
- Economic Attacks: Flash loans and oracle manipulation can destabilize price feeds and trigger cascading failures across interconnected DeFi protocols.
- Poor Payload Validation: Without strict type/format checks, malicious messages can slip through (see insights from Webisoft).
- Lack of Domain Separation: Failing to separate signing domains enables cross-protocol misuse, a subtle but dangerous flaw.
A Systematic Approach to Risk Assessment
No single tool or audit can guarantee safety. Instead, effective risk assessment combines multiple strategies tailored for the unique structure of each protocol. Here’s how leading teams approach it today:
- Diversify Validator Governance: Use multi-signature schemes and threshold cryptography to reduce centralization risk (source). This makes it harder for attackers to compromise enough keys at once.
- Aggressive Smart Contract Auditing: Regular audits by independent experts, and formal verification where possible, catch bugs before they’re exploited. For example, Nomad’s exploit could have been prevented with more rigorous contract checks.
- Pace Asset Transfers with Rate Limiting: Capping transfer volumes narrows an attacker’s window for large-scale theft if something goes wrong (source).
- Sustain Active Monitoring and Incident Response: Real-time analytics spot suspicious patterns early so teams can react before major losses occur (source).
The Role of Standardization and Interoperability Frameworks
Lack of industry-wide standards is itself a risk factor. Protocols that follow standardized communication methods are easier to audit, monitor, and secure. As highlighted in several research reports, fostering interoperability reduces hidden attack vectors while making it easier for ecosystem participants to collaborate on defense strategies.
Industry leaders are increasingly advocating for open security frameworks and transparent communication channels between bridge operators. This collaborative approach not only deters attackers but also accelerates post-incident recovery. When protocols share threat intelligence and standardized response playbooks, the entire cross-chain ecosystem becomes more resilient.
Practical Steps for Developers and Users
Whether you’re building a new cross-chain messaging protocol or simply using one, there are actionable steps you can take to reduce exposure to protocol vulnerability analysis risks:
For developers: Prioritize layered defense. Implement rigorous message validation, ensure unique transaction identifiers to prevent replay attacks, and keep off-chain components as minimal as possible. Regularly update dependencies and monitor for upstream vulnerabilities in libraries or third-party services.
For users: Stick with bridges that have undergone recent, independent audits and publish transparency reports. Limit the value transferred in a single transaction, rate limiting isn’t just for protocols; it’s a best practice for individuals too. Stay informed about the latest bridge incidents via trusted sources.
Emerging Tools for Automated Risk Assessment
The rise of automated scanners and risk dashboards is transforming how risk assessment in cross-chain protocols is conducted. These tools leverage on-chain analytics, anomaly detection, and even machine learning to flag suspicious activity in real time. While no scanner replaces human expertise, they offer an essential first line of defense, especially as attack vectors become more sophisticated.
Look for platforms that provide:
- Continuous monitoring of validator health and consensus integrity
- Automated payload validation with customizable rulesets
- Breach notification systems that alert users within minutes of anomalous activity
Frequently Asked Questions About Cross-Chain Messaging Risks
The rapid evolution of blockchain bridge security demands both vigilance and adaptability from all participants. By combining robust technical controls with community-driven intelligence sharing, we can mitigate the most severe risks while supporting the growth of interconnected DeFi ecosystems.