Cross-chain bridges are the backbone of blockchain interoperability, enabling seamless transfers of assets and data between otherwise siloed networks. But with this new connective tissue comes a growing attack surface. Since 2021, high-profile exploits have drained nearly $4.3 billion from cross-chain bridges, underscoring the urgent need for robust, proactive security measures.
Why Are Cross-Chain Bridges So Vulnerable?
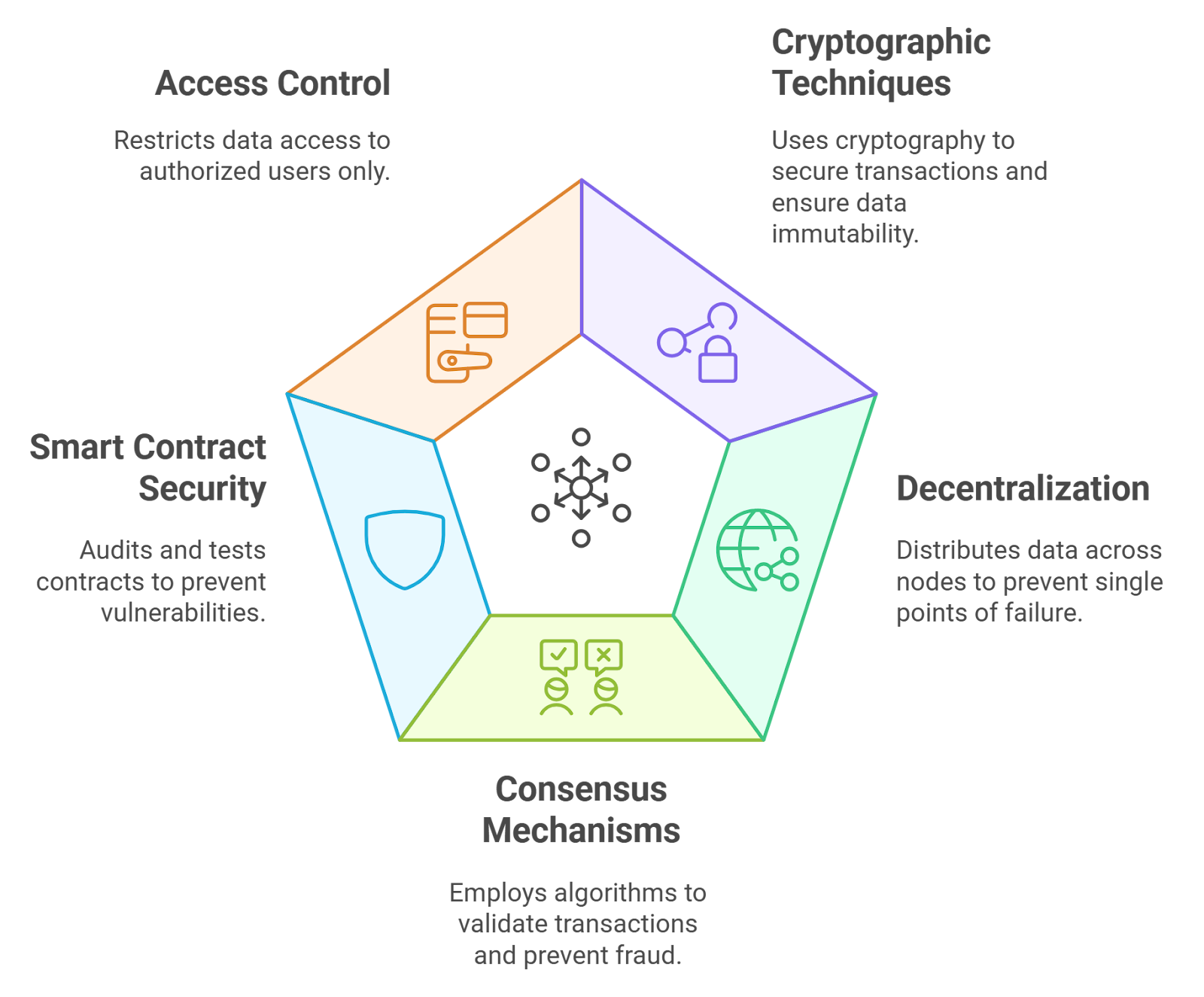
Cross-chain bridges combine the complexity of smart contracts with multi-network communication and off-chain components. This creates several unique risk vectors:
- Smart Contract Flaws: Bugs or logic errors in bridge contracts can let attackers mint tokens without authorization. The infamous Wormhole exploit in February 2022 saw $326 million lost on Solana due to such a flaw.
- Validator Node Compromise: Many bridges rely on validator nodes to approve transactions. If these nodes are hacked or collude, attackers can forge records or signatures, just like the $573 million Ronin Bridge hack in March 2022.
- Authorization and Replay Attacks: Overly permissive contract permissions and weak transaction verification can allow bad actors to drain assets using functions like TransferFrom.
- Backend and Message Handling Issues: Off-chain servers that fail to properly authenticate messages open the door for forged events and token theft.
The complexity is daunting, but awareness is only half the battle. What’s needed is continuous, real-time vigilance, something manual audits simply can’t provide alone.
The Rise of Real-Time Risk Scanners
This is where real-time risk scanners enter the scene as game-changers for blockchain bridge security monitoring. Unlike static audits or periodic reviews, these tools operate around the clock, watching every transaction and contract interaction for signs of trouble. Their mission: detect anomalous behavior before it becomes catastrophic loss.
Top Real-Time Cross-Chain Bridge Risk Scanners
-

HighGuard: An advanced scanner that detects transactions violating smart contract business logic across multiple chains. HighGuard operates without requiring code instrumentation or extra gas costs, making it efficient for real-time bridge monitoring.
-

XChainWatcher: This tool monitors cross-chain bridges in real time using a Datalog-powered engine. XChainWatcher has successfully identified major attacks, such as those on the Ronin and Nomad bridges, by uncovering unintended behaviors and vulnerabilities.
-

SmartAxe: A framework focused on identifying vulnerabilities in cross-chain bridge smart contracts through fine-grained static analysis. SmartAxe models access control and constructs cross-chain control-flow graphs to detect semantic inconsistencies.
-
Extractor by Hacken: A real-time security and compliance monitoring platform for cross-chain bridges. Extractor tracks smart contract interactions, transaction flows, and custodial wallet activities to detect threats and unauthorized access.
The market now features several advanced solutions tailored for DeFi bridge security tools and cross-chain protocol risk analysis:
- HighGuard: Monitors smart contract transactions across chains, flagging violations of business logic without code instrumentation or extra gas costs.
- XChainWatcher: Uses a Datalog engine to detect attacks in real time, successfully identifying threats during both the Ronin and Nomad bridge incidents.
- SmartAxe: Performs static analysis at a granular level, mapping access control and data flows to catch subtle vulnerabilities unique to heterogeneous cross-chain implementations.
- Extractor by Hacken: Provides live threat detection and compliance monitoring for bridges, scrutinizing smart contract calls and custodial wallet activity for suspicious patterns.
This shift toward automated surveillance means that teams are no longer flying blind between audits or hoping that users will spot problems before it’s too late. Instead, they’re equipped with continuously running sentinels capable of instant alerts when something looks off, a crucial upgrade given how fast exploits can unfold in DeFi environments.
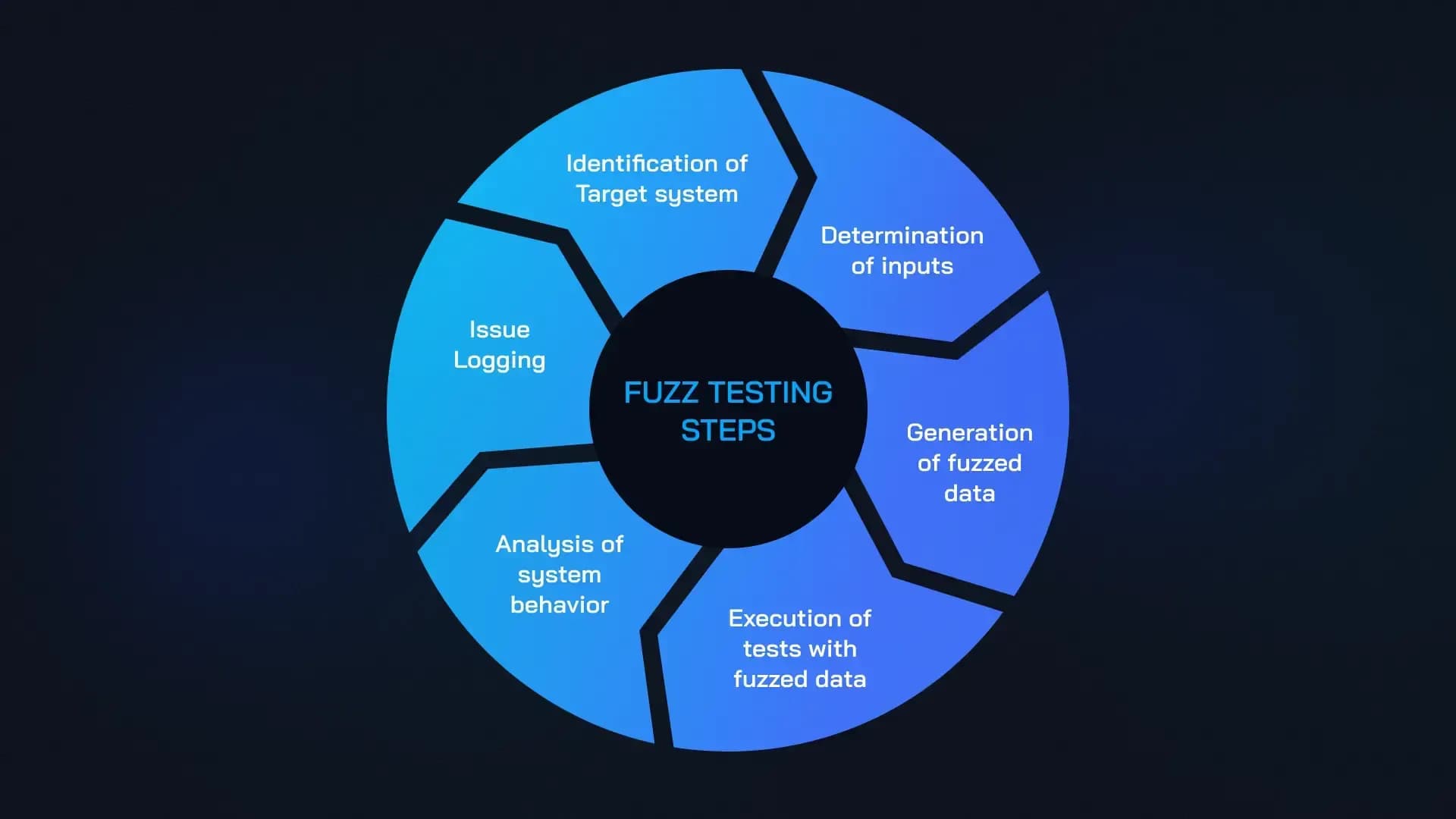
How Real-Time Detection Actually Works
The core value proposition behind real-time bridge vulnerability detection lies in its ability to spot both known attack patterns and new anomalies as they emerge. Here’s how leading scanners typically operate:
- Anomaly Detection Engines: These systems baseline “normal” behavior across contracts and wallets, then flag deviations, like sudden spikes in withdrawals or unexpected validator actions, for immediate review.
- Cross-Chain Correlation: By analyzing interlinked events across multiple blockchains (e. g. , Ethereum-Solana), scanners can catch inconsistencies that single-chain tools would miss entirely.
- No-Code Instrumentation: Modern platforms like HighGuard monitor activity without requiring invasive changes to deployed contracts or incurring extra transaction costs, a major win for usability.
- Sophisticated Alerting and Response: When an issue is detected, such as an unauthorized mint operation, teams receive instant notifications so they can freeze affected assets or block further damage within minutes instead of hours (or worse).
This approach has already proven its worth: XChainWatcher’s real-time detection mechanisms were instrumental in identifying suspicious behaviors during past hacks before losses escalated further. As more protocols adopt these tools, we’re seeing a marked improvement in incident response times, and ultimately, user confidence across the ecosystem grows stronger as well.
Integrating Risk Scanners Into Bridge Operations
For cross-chain bridge operators and DeFi teams, deploying real-time risk scanners is no longer optional, it’s a core requirement for operational resilience. The best platforms offer seamless integration with both on-chain and off-chain components, providing comprehensive visibility into every layer of bridge infrastructure. This means monitoring not just smart contract calls, but also validator communications, backend server events, and even custodial wallet movements in real time.
Leading solutions like Extractor by Hacken and HighGuard are designed for easy plug-and-play deployment, minimizing the friction of adoption. Teams can configure custom alert thresholds for different types of assets or transaction volumes, ensuring that only truly suspicious activity triggers an incident response. This targeted approach helps avoid alert fatigue while focusing attention where it matters most.
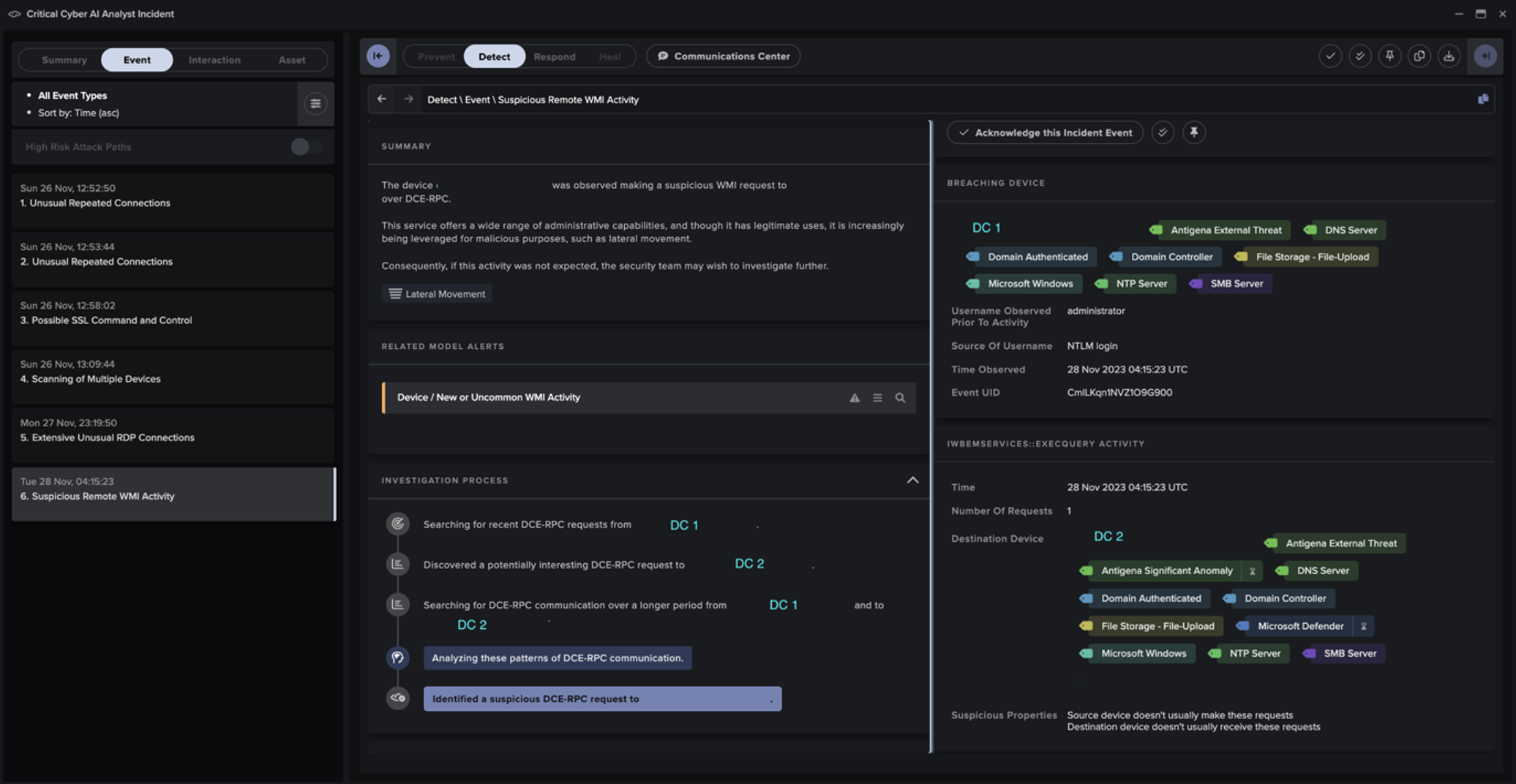
Proactive Defense: Moving Beyond Passive Monitoring
What sets modern cross-chain bridge risk scanners apart is their ability to shift security from reactive to proactive. Instead of waiting for a hack to be discovered after the fact, often when millions have already been lost, these tools empower teams to intervene before significant damage occurs. Automated incident response protocols can freeze compromised contracts or halt suspicious withdrawals in seconds.
- Case Study: During the Ronin Bridge exploit, tools like XChainWatcher flagged abnormal validator signatures almost immediately. Although losses were still significant, early detection enabled faster containment and forensic analysis.
- Continuous Improvement: Real-time scanners feed data back into threat intelligence systems, helping developers patch vulnerabilities and refine detection algorithms with each new incident.
- User Confidence: Public dashboards and transparent reporting foster trust among users and institutional partners who demand proof of robust risk management practices before engaging with a bridge protocol.
Looking Ahead: The Future of Cross-Chain Security
The rapid evolution of blockchain interoperability demands equally agile security strategies. As bridges become more complex, supporting not just token transfers but arbitrary message passing and multi-chain dApps, the need for advanced monitoring will only intensify. Expect future scanners to leverage AI-driven anomaly detection, integrate seamlessly with bug bounty programs, and provide even deeper analytics across heterogeneous blockchain environments.
If you’re building or using cross-chain infrastructure today, prioritize platforms that embed these advanced risk scanning capabilities at their core. The difference between catching an exploit in seconds versus hours isn’t just technical, it’s existential for your protocol’s reputation and user funds.
Essential Features in Cross-Chain Bridge Risk Scanners
-

Real-Time Transaction Monitoring: The scanner should provide continuous, real-time surveillance of cross-chain transactions to detect suspicious activities as they occur. This rapid detection is vital for preventing large-scale exploits, as demonstrated by tools like Extractor by Hacken and XChainWatcher.
-
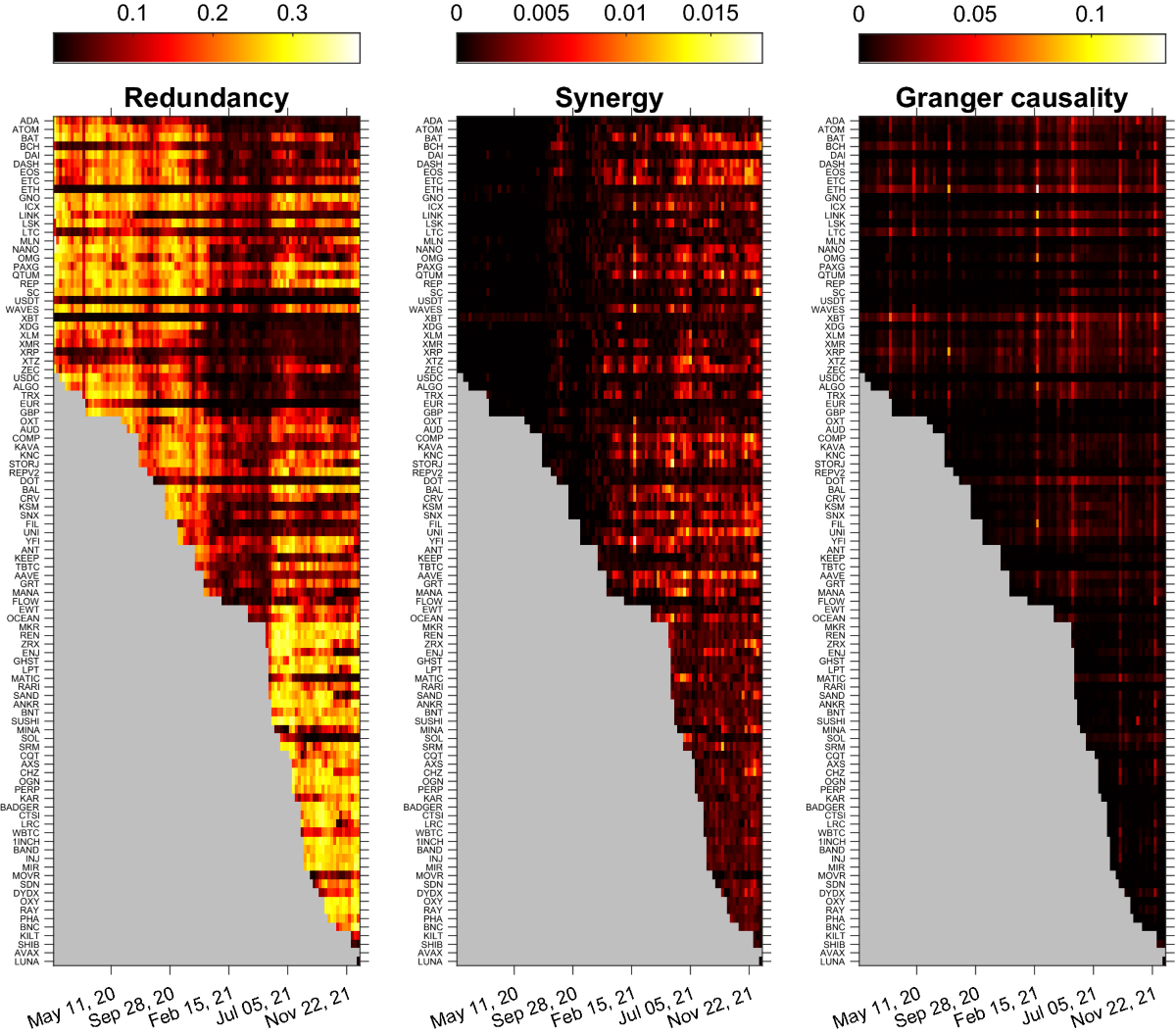
Cross-Chain Activity Correlation: Effective scanners should correlate activities across multiple blockchains, helping to spot patterns or anomalies that could indicate coordinated attacks. This holistic view is essential for bridges operating between diverse networks.
-
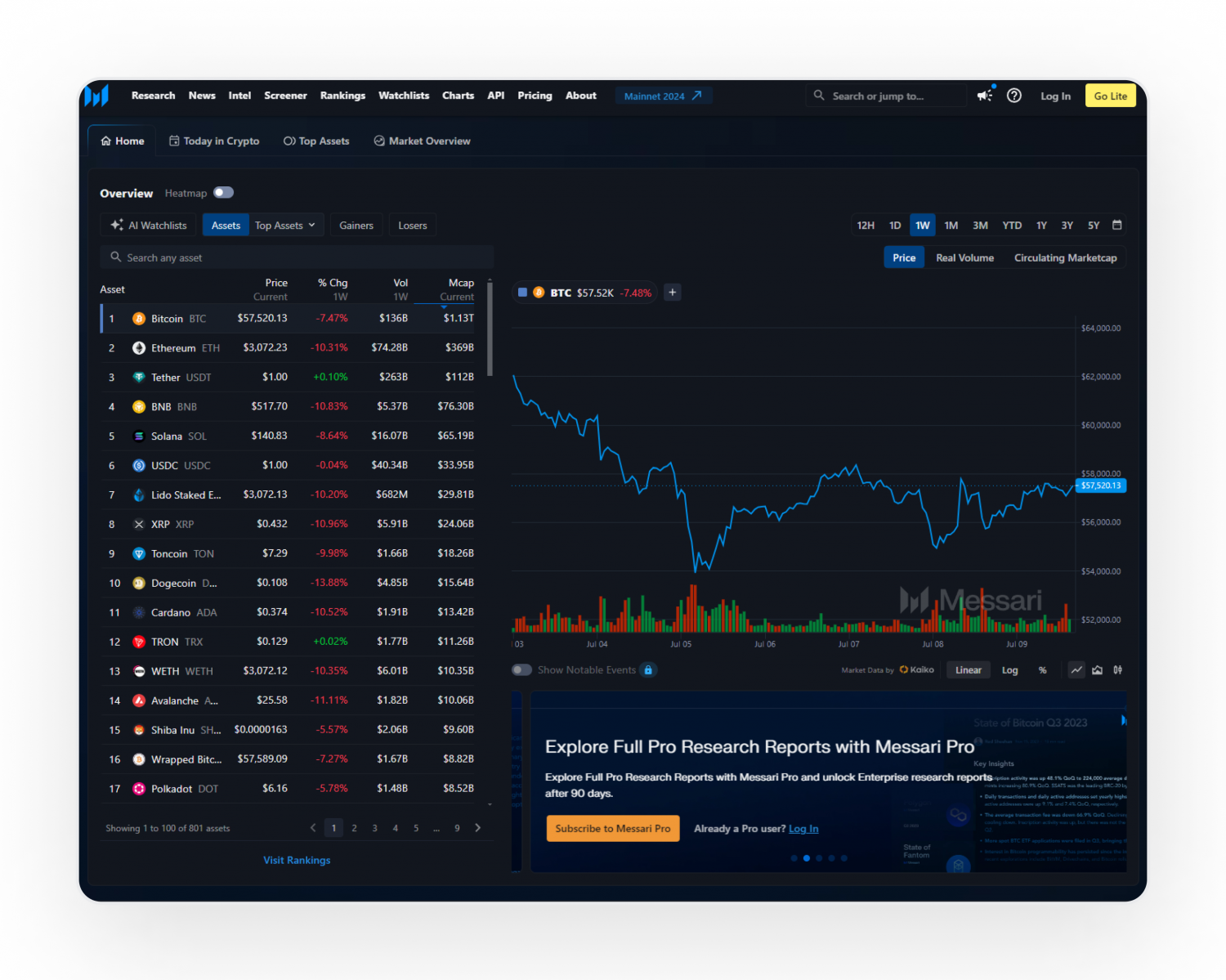
Automated Risk Scoring and Alerts: The ability to assign risk scores to transactions and trigger automated alerts enables faster response to threats. Platforms like Lukka Blockchain Analytics offer real-time risk scoring to prioritize urgent issues.
-

Compliance and Regulatory Monitoring: Ensure the scanner includes compliance checks to help bridges adhere to evolving regulatory standards. Real-time compliance monitoring, as provided by Extractor, is crucial for preventing illicit activity and maintaining trust.
-

Historical Audit Trails and Forensics: The scanner should maintain detailed logs and audit trails for post-incident analysis. This feature supports investigations and helps teams learn from past events to improve future defenses.
-
Customizable Detection Rules: Look for platforms that allow users to define and adjust detection parameters based on their bridge’s unique threat landscape. This flexibility ensures the scanner remains effective as attack methods evolve.
The bottom line? Real-time cross-chain bridge risk scanners are now the front line in defending against validator exploits, smart contract flaws, and sophisticated multi-network attacks. By combining automated surveillance with actionable alerts and continuous feedback loops, these tools give DeFi teams the fighting chance they need in an increasingly high-stakes landscape.
For a deeper dive into how these technologies are transforming protocol defense strategies, and practical steps you can take to strengthen your own operations, check out our comprehensive guide at How Real-Time Risk Scanning Improves Cross-Chain Bridge Security.