Cross-chain bridges have become the backbone of blockchain interoperability, allowing assets and data to move seamlessly across disparate networks. However, this critical functionality comes at a cost: these bridges are now among the most attractive targets for hackers, with billions lost in high-profile attacks. To understand why cross-chain bridge security is so difficult to achieve, we need to examine the seven most critical vulnerabilities that consistently put these systems at risk.

Why Are Cross-Chain Bridges Prime Targets?
Unlike single-chain protocols, cross-chain bridges aggregate value and permissions from multiple blockchains into one location. This concentration of assets and control makes them a lucrative target for attackers seeking maximum impact. In 2022 and 2023 alone, several major hacks exploited weaknesses unique to bridge architecture, resulting in losses that reverberated throughout the DeFi ecosystem.
The Seven Most Critical Cross-Chain Bridge Vulnerabilities
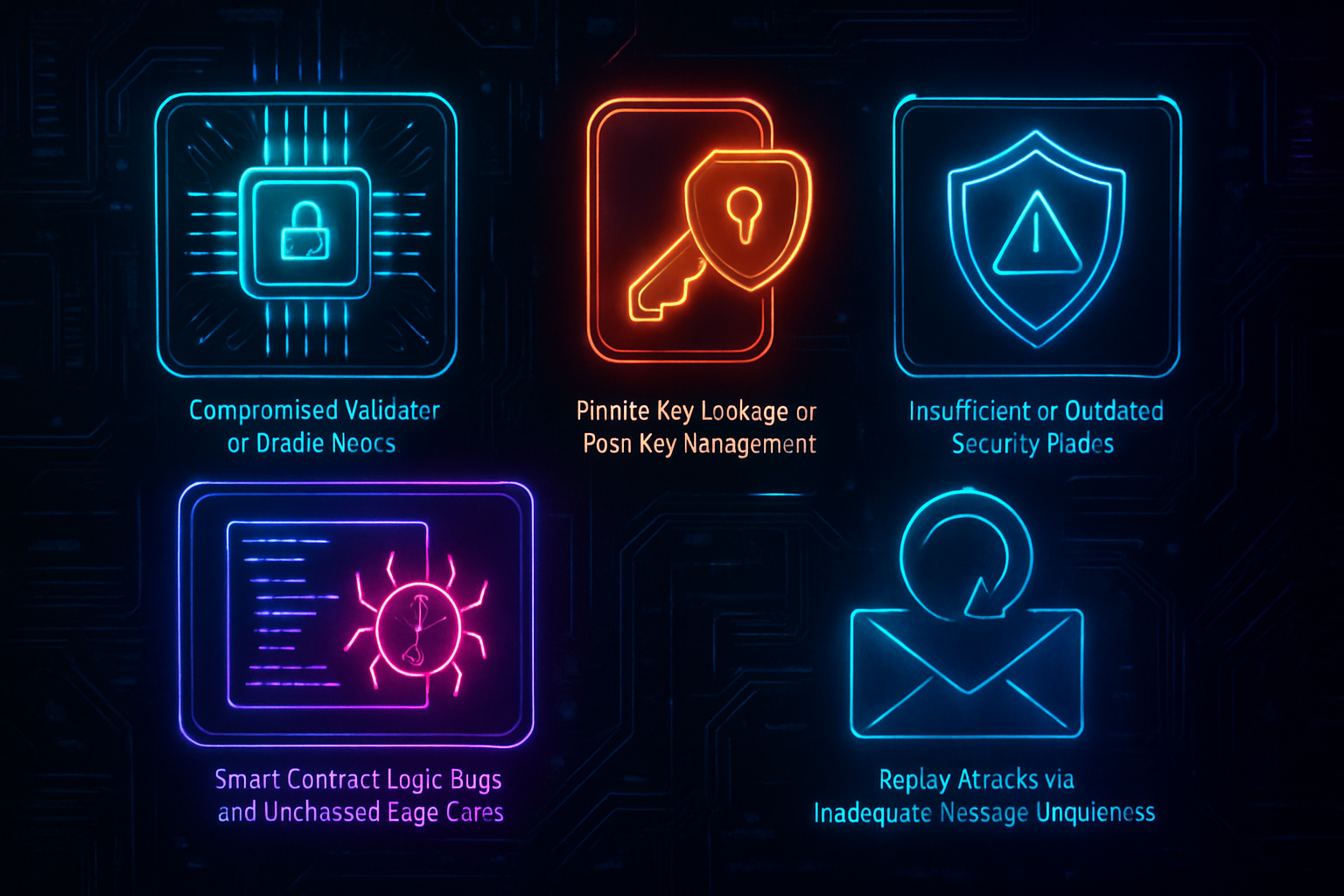
Seven Key Vulnerabilities in Cross-Chain Bridges
-

Compromised Validator or Oracle Nodes: Attackers can take control of validator or oracle nodes that authorize cross-chain transfers, enabling them to approve fraudulent transactions. This vulnerability was exploited in the Harmony Horizon Bridge hack, resulting in a $100 million loss.
-

Private Key Leakage or Poor Key Management: Weaknesses in managing or storing private keys can lead to catastrophic breaches. The infamous Ronin Bridge incident saw over $600 million stolen when attackers compromised a majority of validator keys.
-

Smart Contract Logic Bugs and Unchecked Edge Cases: Flaws in smart contract code or untested scenarios can be exploited by attackers. The Wormhole Bridge hack in 2022, which resulted in a $320 million loss, was due to a smart contract vulnerability.
-
Insufficient or Outdated Security Audits: Failing to conduct regular, comprehensive audits leaves bridges exposed to both known and emerging threats. Many high-profile breaches, including the Qubit Finance exploit, have been traced back to unaudited or outdated code.
-

Replay Attacks via Inadequate Message Uniqueness: Without unique identifiers in cross-chain messages, attackers can replay valid transactions to illicitly transfer assets multiple times. This vulnerability has been observed in several bridge exploits.
-
Centralized Bridge Control and Single Points of Failure: Bridges managed by a small group or single entity are vulnerable to targeted attacks or internal compromise. Decentralization is crucial to reduce these risks.
-

Insecure Cross-Chain Message Verification: Weak verification mechanisms can allow attackers to forge or manipulate messages, resulting in unauthorized asset movements across chains. Robust message validation is essential for bridge security.
Let’s break down each vulnerability and why it matters for anyone concerned about blockchain bridge hacks or DeFi bridge vulnerabilities:
1. Compromised Validator or Oracle Nodes
Many cross-chain bridges rely on a set of validators or oracle nodes to confirm transactions between chains. If an attacker can compromise enough of these nodes, either by gaining access to their private keys or exploiting weak governance, they can approve fraudulent transfers. The infamous Harmony Horizon Bridge hack is a case study in validator compromise, where attackers gained control over two out of five validator keys, resulting in a $100 million loss (source). Robust decentralization and active monitoring are essential countermeasures here.
2. Private Key Leakage or Poor Key Management
Bridge operations often depend on private keys for signing transactions or managing funds. Poor key management practices, such as storing keys in hot wallets or failing to use secure hardware modules, can lead to catastrophic breaches if those keys are leaked or phished. The Ronin Bridge hack demonstrated this risk dramatically when attackers stole over $600 million by compromising five out of nine validator keys (source). Multi-signature schemes and hardware security modules (HSMs) are now considered essential for mitigating this risk.
3. Smart Contract Logic Bugs and Unchecked Edge Cases
The complexity of cross-chain logic increases the attack surface for bugs, especially when contracts interact with external chains in non-standard ways. Vulnerabilities such as unchecked input validation, improper message parsing, or failure to account for edge cases can allow attackers to mint tokens without collateral (as seen in the Wormhole exploit) or drain funds via logic flaws. Comprehensive code reviews and formal verification are vital here; even minor oversights can have outsized consequences.
4. Insufficient or Outdated Security Audits
A one-time audit is not enough in the fast-evolving world of DeFi bridge vulnerabilities. Attackers often exploit outdated codebases that haven’t been re-audited after upgrades, changes in dependencies, or new threat discoveries (source). Regular audits by independent experts, and public disclosure of findings, are now industry best practices.
5. Replay Attacks via Inadequate Message Uniqueness
Replay attacks are a subtle but devastating threat to cross-chain bridge security. If a bridge does not enforce strict uniqueness in its cross-chain messages, using unique nonces, chain IDs, or contract addresses, an attacker can “replay” a valid message multiple times to illicitly extract assets. This vector is often overlooked during development, especially when protocols assume that message delivery is inherently atomic or idempotent across networks. The result? Funds can be drained, and trust in the bridge erodes rapidly. Implementing robust message formats with explicit uniqueness checks is non-negotiable for modern bridges.
6. Centralized Bridge Control and Single Points of Failure
Centralization remains an Achilles’ heel for many blockchain bridges. When control over critical operations, such as pausing transfers or upgrading contracts, is vested in a single entity or tightly coupled group, the entire system becomes vulnerable to insider threats, governance attacks, or regulatory pressure. Not only does this undermine the ethos of decentralization that underpins DeFi, but it also creates practical risk: a single compromised admin key can result in total loss of user funds. Moving toward decentralized governance and multi-party control mechanisms is essential for resilience.
7. Insecure Cross-Chain Message Verification
Finally, the process by which a bridge verifies that an event on one chain legitimately corresponds to an action on another is often fraught with risk. Weaknesses here can arise from reliance on unauthenticated data feeds, improper parsing of proof structures, or failure to validate event authenticity against canonical sources. Attackers may forge or manipulate messages to trigger unauthorized withdrawals or minting events, sometimes bypassing all other controls if this layer is weak. Secure off-chain relays and cryptographic proofs (such as SPV or zk-SNARKs) are increasingly used to mitigate these risks but require careful implementation and constant vigilance.
Practical Mitigations for Key Cross-Chain Bridge Vulnerabilities
-

Compromised Validator or Oracle Nodes: Mitigation: Decentralize validator sets using established protocols like Chainlink or Pocket Network, and implement robust slashing and monitoring mechanisms to reduce the risk of collusion or takeover.
-
Private Key Leakage or Poor Key Management: Mitigation: Store keys in Hardware Security Modules (HSMs) and use multi-signature wallets (e.g., Gnosis Safe). Regularly rotate keys and restrict access using strict operational controls.
-

Smart Contract Logic Bugs and Unchecked Edge Cases: Mitigation: Conduct comprehensive code audits with reputable firms such as Quantstamp or Trail of Bits, employ formal verification, and implement rigorous testing for all edge cases before deployment.
-
Insufficient or Outdated Security Audits: Mitigation: Schedule regular, independent security audits (at least annually or after major updates) and maintain bug bounty programs on platforms like Immunefi to incentivize ongoing vulnerability discovery.
-
Replay Attacks via Inadequate Message Uniqueness: Mitigation: Integrate unique identifiers (such as chain IDs, contract addresses, and nonces) into all cross-chain messages to ensure each transaction is processed only once. Reference: CEEX Global
-
Centralized Bridge Control and Single Points of Failure: Mitigation: Distribute control by adopting multi-party computation (MPC) or threshold signature schemes, and avoid architectures where a single entity can unilaterally approve transactions. Projects like Axelar and THORChain exemplify decentralized bridge models.
-
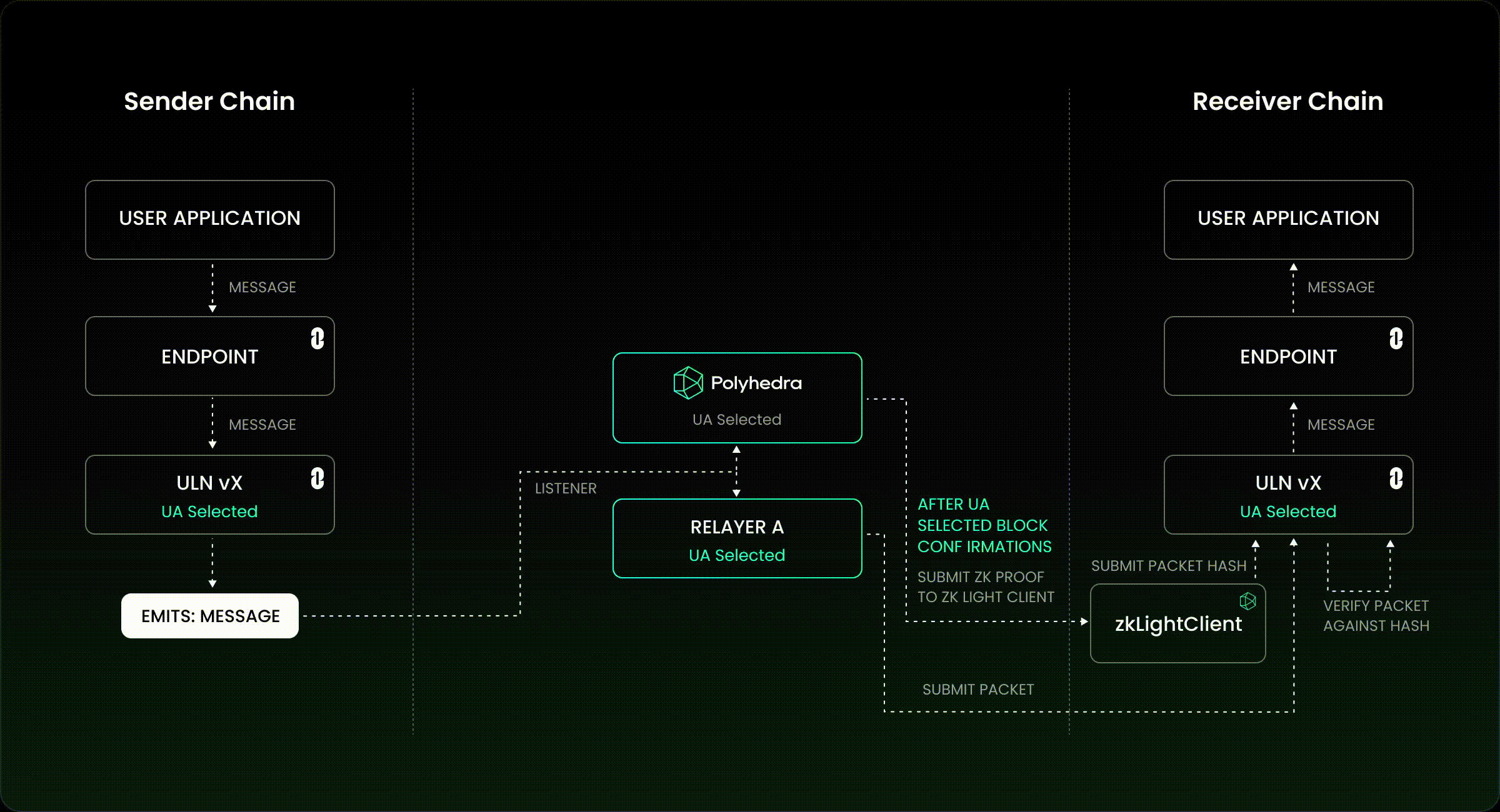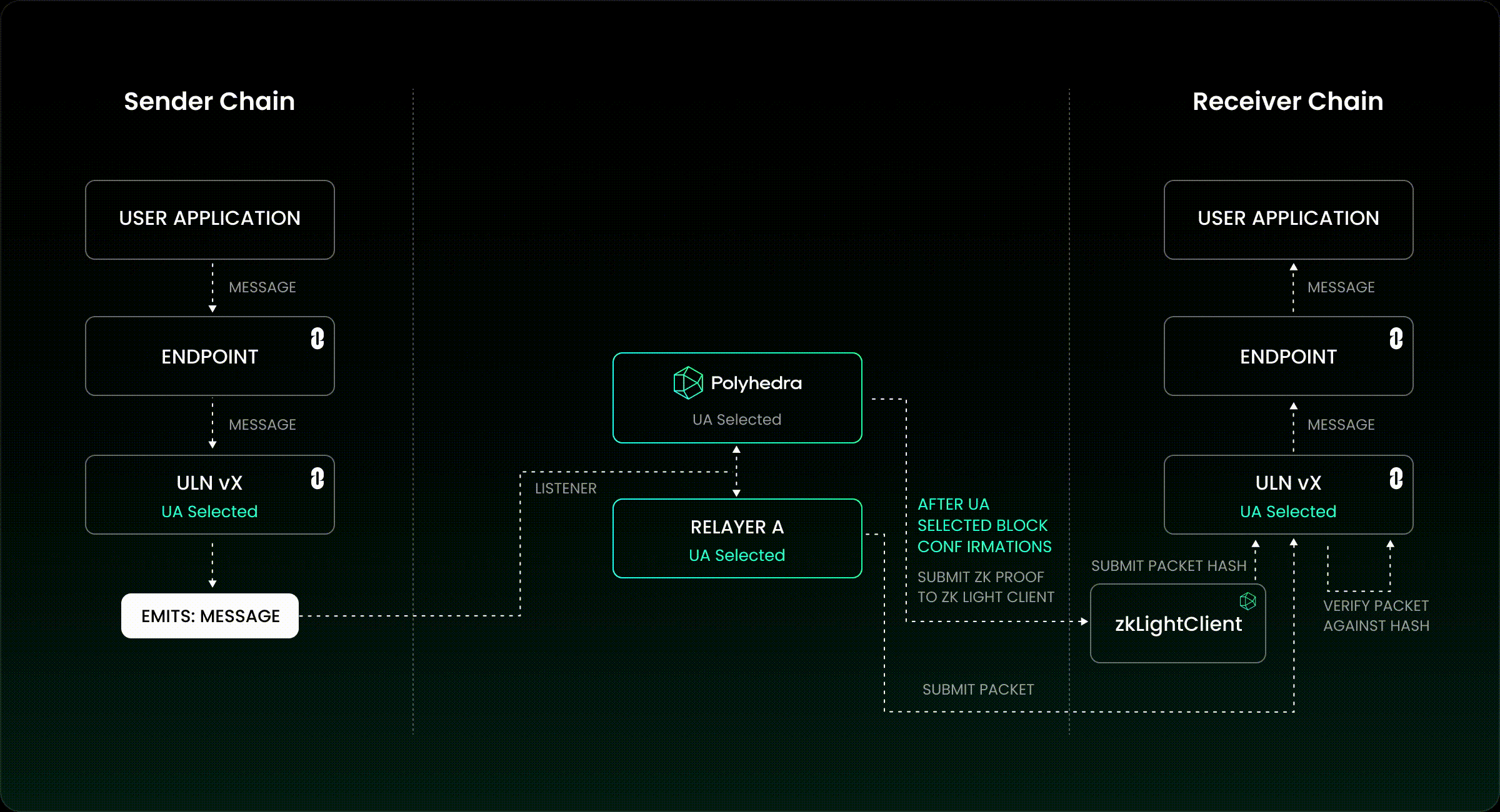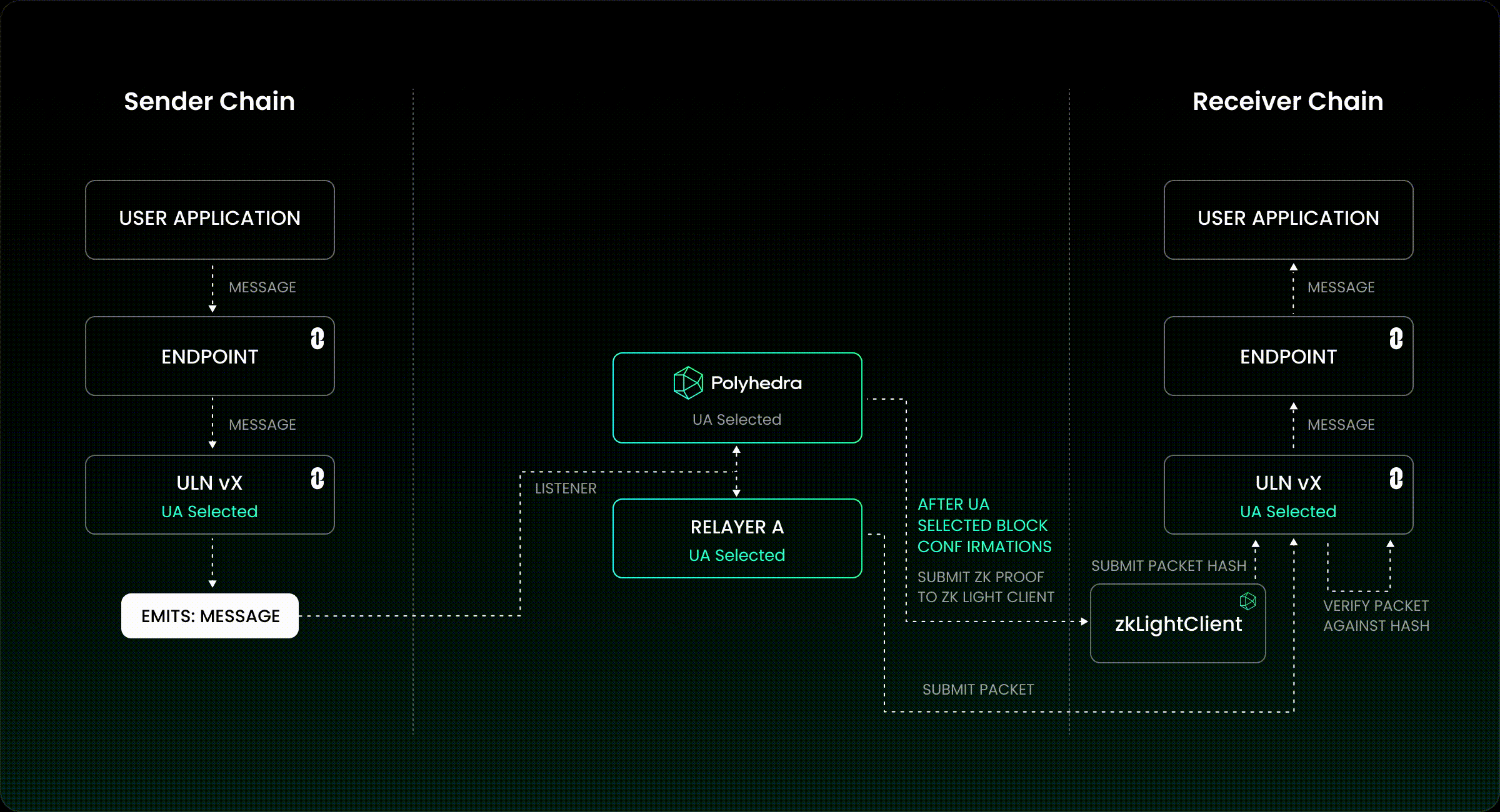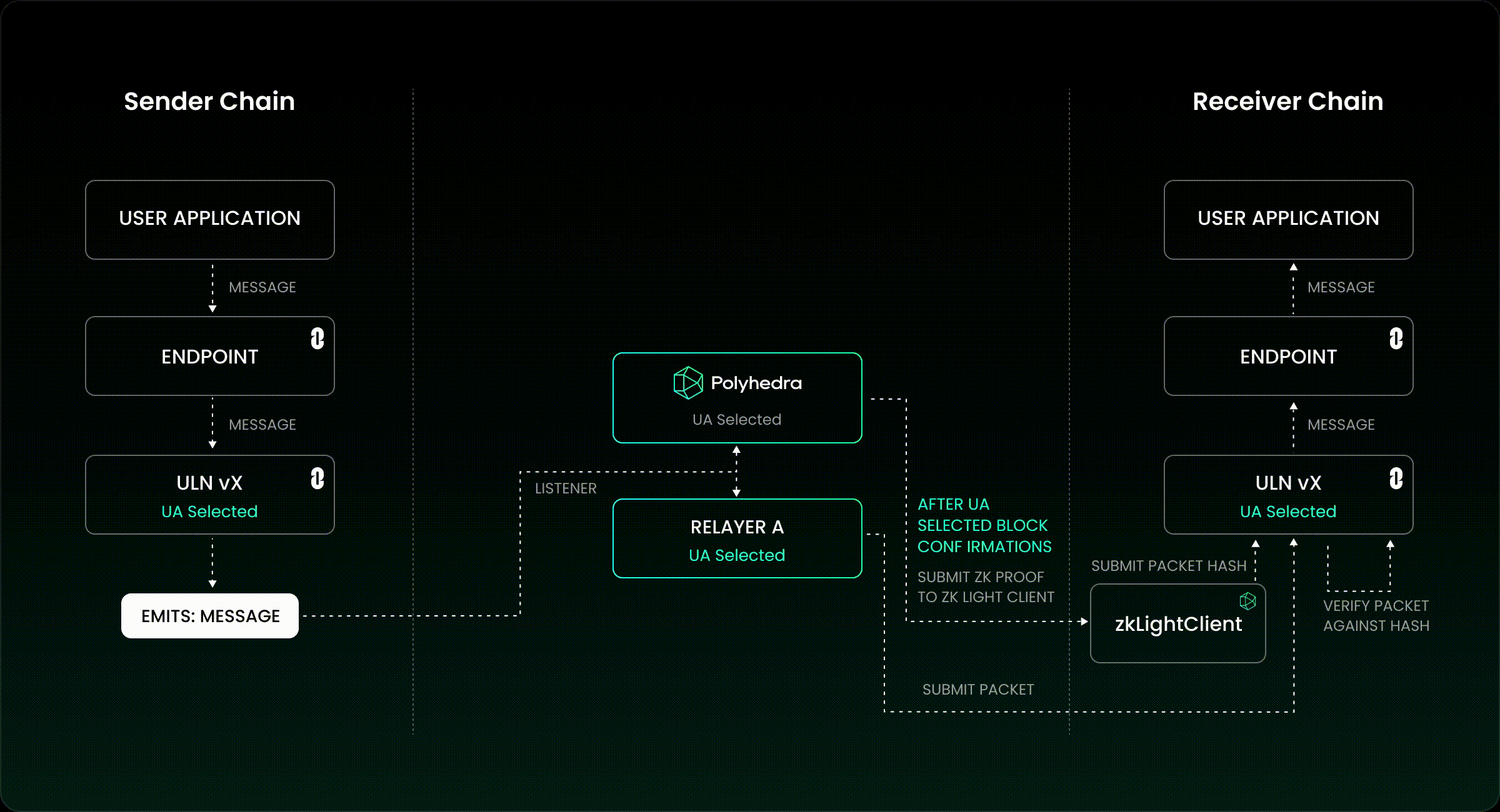
Insecure Cross-Chain Message Verification: Mitigation: Use cryptographically secure message validation protocols, such as Chainlink CCIP, and ensure all messages are authenticated and authorized before asset release.
Best Practices for Cross-Chain Risk Mitigation
Securing cross-chain bridges requires more than patching individual vulnerabilities; it demands a holistic approach rooted in both technical rigor and operational discipline:
- Decentralize validator sets and use threshold signatures to reduce the impact of node compromise.
- Enforce hardware-backed key management and rotate keys regularly.
- Mandate continuous security audits, especially after code changes or upgrades.
- Implement rate limits on asset transfers to cap maximum potential losses during attacks.
- Monitor transaction flows in real time, using automated alerting systems for anomalous behavior.
- Design message schemas with explicit uniqueness constraints, using nonces and chain-specific identifiers.
- Pursue open-source transparency, enabling community review and rapid bug discovery.
Diversity is the best hedge, even in protocol design. Relying on multiple layers of defense rather than any single control point will always serve you better over time.
The landscape of blockchain bridge hacks will continue to evolve as attackers probe for new weaknesses, but so too will defensive tools and practices. By understanding these seven vulnerabilities and proactively implementing layered defenses, developers and users alike can help foster a more secure, resilient future for blockchain interoperability.






