
Cross-chain bridges are the connective tissue of the blockchain ecosystem, enabling assets and data to flow seamlessly across disparate networks. Yet, this essential interoperability comes at a steep price: since May 2021, over $3.2 billion has been lost to bridge attacks, cementing these protocols as the highest-value targets in crypto security. As attackers become more sophisticated and bridge architectures grow in complexity, traditional post-incident audits are no longer enough. The industry is shifting toward real-time risk scanning for cross-chain bridges as a foundational layer of defense.
Why Real-Time Risk Scanning Is Reshaping Bridge Security
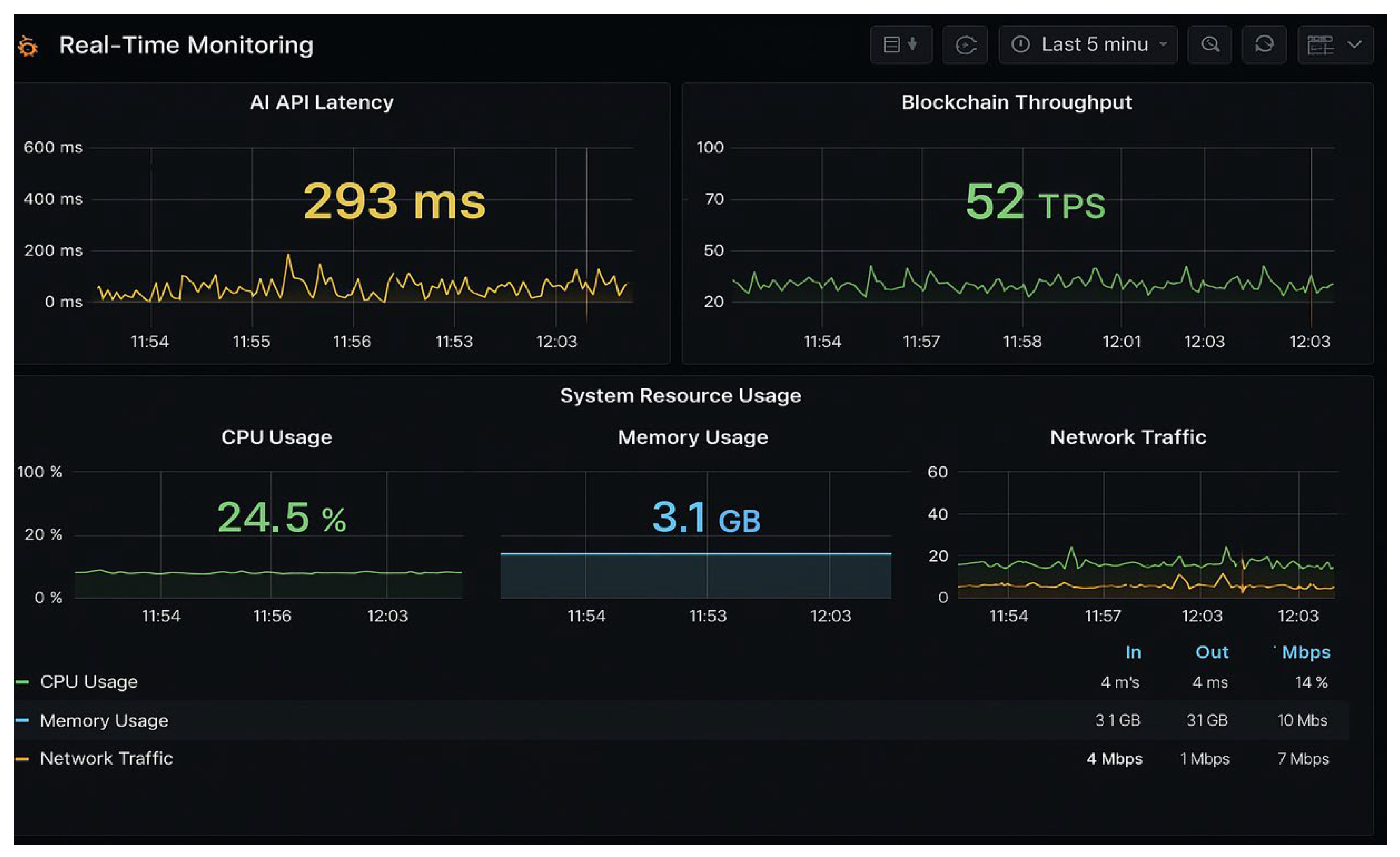
The goal of real-time scanning is clear: detect and neutralize threats before they can inflict damage. Unlike static code reviews or periodic audits, real-time systems analyze every transaction and contract interaction as it happens. This means that anomalous behaviors, such as unauthorized withdrawals, suspicious contract calls, or unexpected changes in validator sets, can trigger immediate alerts or even automated responses.
Recent research from Chainlink and Hacken highlights seven key vulnerabilities inherent to cross-chain bridges:
Top 7 Cross-Chain Bridge Vulnerabilities
-

1. Smart Contract Bugs: Vulnerabilities in bridge smart contracts, such as unchecked inputs or logic errors, can be exploited by attackers to drain funds or disrupt operations.
-

2. Privileged Role Exploits: Attackers target bridges with poorly managed admin keys or multisig wallets, enabling unauthorized access or control over bridge assets.
-
3. Insufficient Transaction Validation: Weaknesses in transaction verification processes allow malicious or invalid cross-chain messages to be processed, leading to potential asset loss.
-

4. Oracle Manipulation: Manipulating or compromising off-chain data feeds (oracles) can result in incorrect state updates and unauthorized asset transfers across chains.
-

5. Bridge Liquidity Attacks: Exploiting low liquidity or faulty liquidity management can cause imbalances, enabling attackers to siphon funds or destabilize the bridge.
-

6. Inadequate Real-Time Monitoring: Lack of continuous, automated monitoring (e.g., absence of tools like Extractor or XChainWatcher) delays threat detection and incident response, increasing risk exposure.
-

7. Cross-Chain Message Replay Attacks: Attackers reuse valid bridge messages on different chains or at different times, exploiting insufficient replay protection to steal assets or disrupt operations.
Each vector represents a potential entry point for attackers. Without continuous monitoring, malicious activity can go undetected until it’s too late, a pattern seen in high-profile hacks like Harmony Bridge and Ronin Network.
The Mechanics of Real-Time Risk Scanning
How does real-time risk scanning actually work? At its core, these systems ingest live data from multiple blockchains and bridge contracts, applying anomaly detection algorithms that flag deviations from normal behavior. Solutions like XChainWatcher provide comprehensive surveillance across different chains, while advanced tools such as BridgeShield employ heterogeneous graph attention networks to map complex transaction flows and identify coordinated attack patterns.
This approach offers several advantages:
- Immediate Threat Detection: Suspicious activity is flagged the moment it occurs, no waiting for daily reports or manual reviews.
- Enhanced Anomaly Detection: AI-driven analytics reduce false positives by understanding context-specific behaviors unique to each bridge protocol.
- Comprehensive Monitoring: All assets and messaging channels are watched continuously, ensuring no blind spots across multi-chain environments.
- Compliance Support: Automated tracking helps teams stay ahead of regulatory requirements by logging every cross-chain movement for auditability.
This shift isn’t just theoretical; it’s already being put into practice by leading DeFi protocols integrating platforms like Hirule Labs’ Cross-Chain Vulnerability Detection System and Extractor. live’s compliance monitoring suite.
The Stakes: Quantifying Bridge Security Risks in 2025
The numbers speak volumes. According to Chainalysis and OneKey, cross-chain bridge exploits have accounted for nearly half (44.8%) of all DeFi hacks over the past three years, with losses now exceeding $3.2 billion since May 2021 alone. Attackers are increasingly leveraging sophisticated methods such as compromised validator keys, logic bugs in message verification contracts, and flash loan manipulations that evade static defenses but can be caught by dynamic monitoring systems.
This is why real-time anomaly detection isn’t just a nice-to-have, it’s an operational necessity for any project aiming to build trust with users and institutional partners alike. The most secure bridges today don’t just rely on audits; they deploy layered defenses that include automated security for blockchain bridges at every stage of operation.
If you’re building or maintaining a protocol that depends on secure interoperability, now is the time to invest in continuous security monitoring solutions tailored specifically for cross-chain messaging protocol risks. For guidance on integrating these tools into your workflow, see our detailed walkthrough at How Blockchain Developers Can Integrate Risk Scanners for Cross-Chain Messaging.
As the threat landscape grows more complex, the most effective protocols are those that treat cross-chain bridge security monitoring as a living process rather than a one-time checkbox. Real-time risk scanning platforms not only catch attacks in progress but also generate actionable intelligence that can inform ongoing code improvements and incident response planning. For instance, after an attempted exploit is detected and blocked, teams can analyze the flagged transaction patterns to harden their contracts or refine their anomaly detection models further.
Best Practices for DeFi Bridge Anomaly Detection
Best Practices for Real-Time Risk Scanning in DeFi Bridges
-
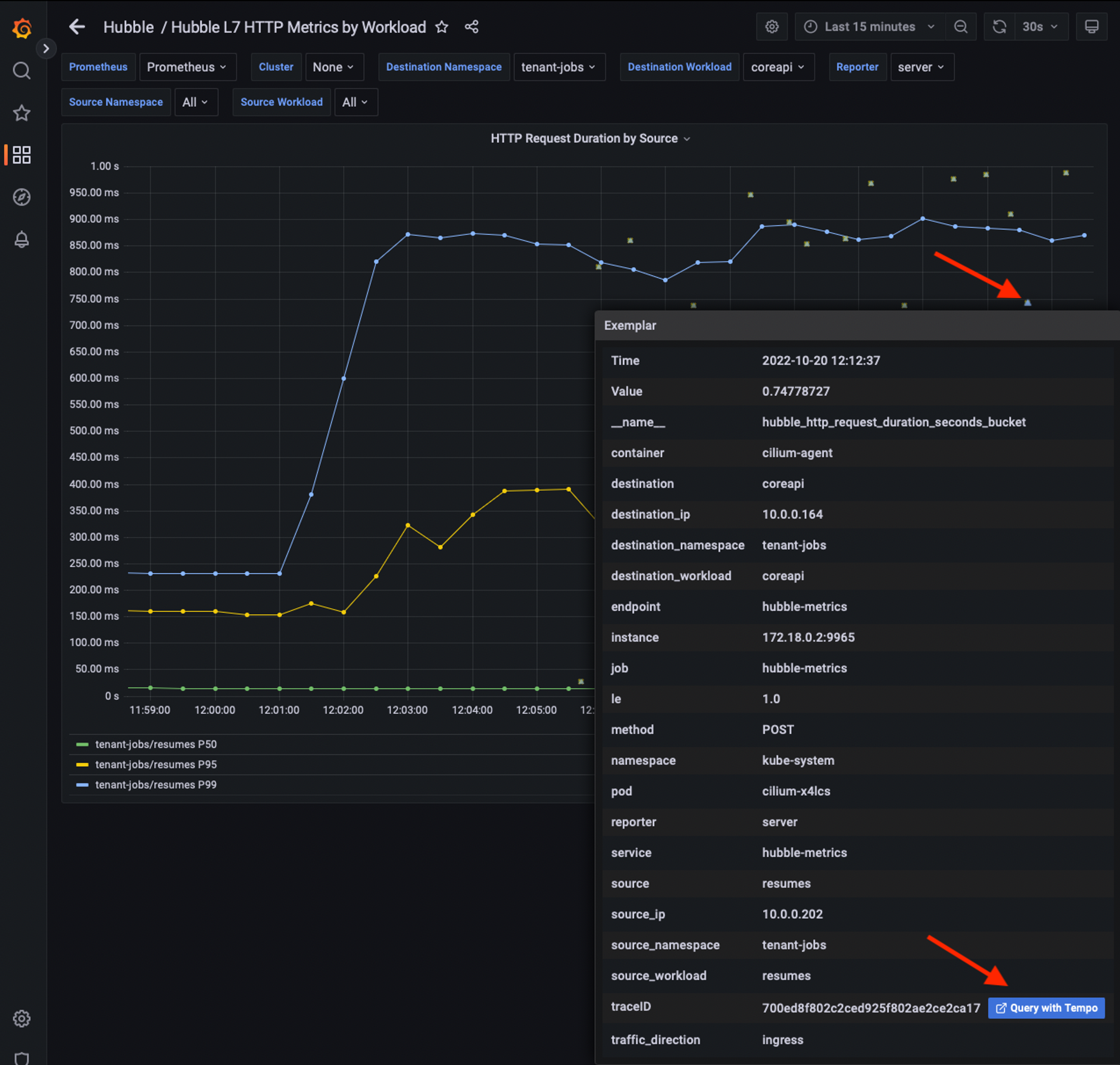
Deploy Specialized Monitoring Platforms: Use established tools like Extractor and Hirule Labs’ Cross-Chain Vulnerability Detection System for continuous, real-time threat detection across bridge operations.
-
Integrate AI-Driven Anomaly Detection: Incorporate solutions such as BridgeShield that leverage machine learning and graph attention networks to identify suspicious cross-chain behaviors and minimize false positives.
-
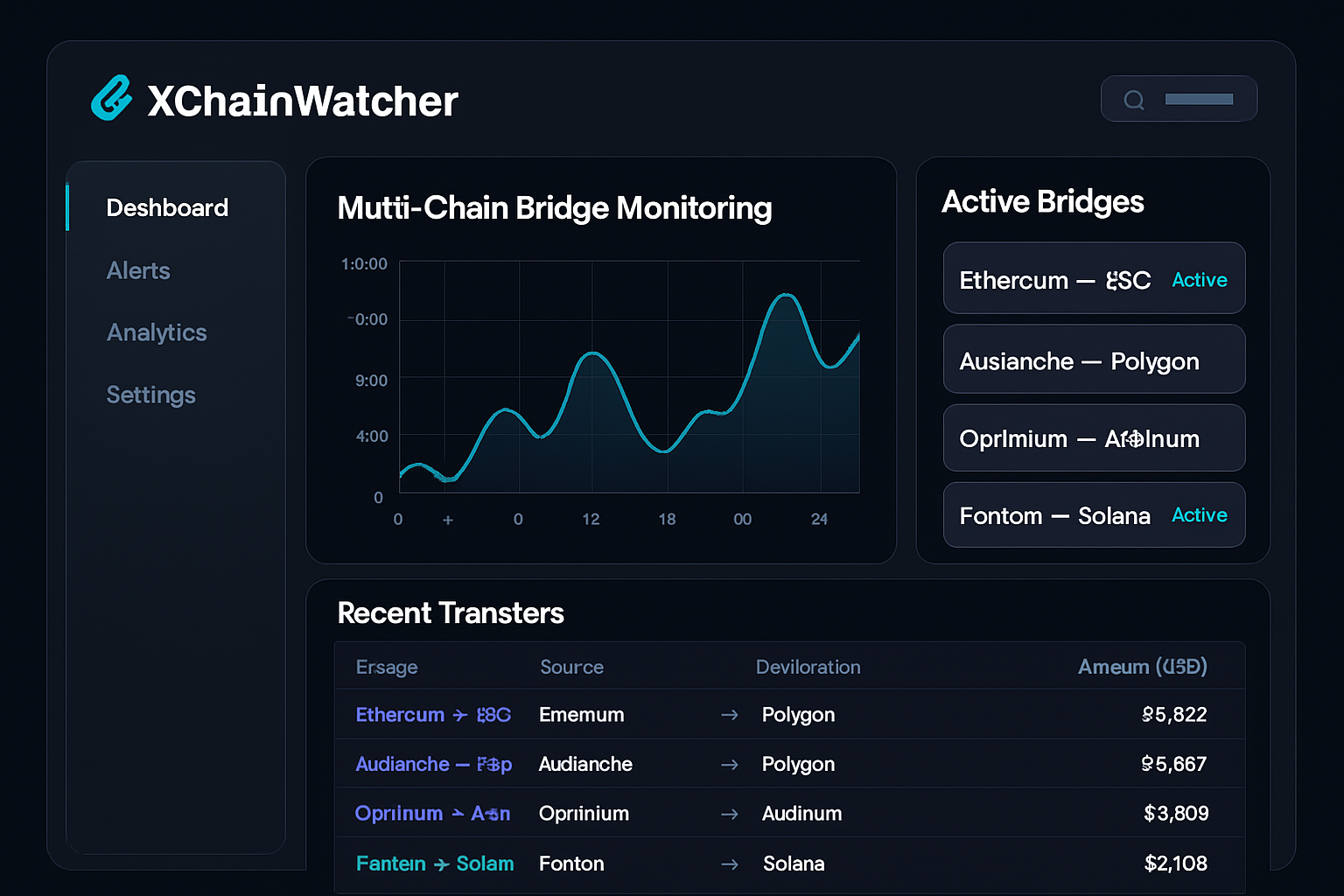
Implement Multi-Chain Surveillance: Adopt comprehensive monitoring platforms like XChainWatcher to track activity and vulnerabilities across multiple blockchain networks in real time.
-
Automate Incident Response Protocols: Establish and regularly test automated response systems that can quickly isolate or halt anomalous transactions when threats are detected, reducing the window for potential exploits.
-

Ensure Regulatory Compliance Monitoring: Use real-time scanning tools to flag illicit or non-compliant activities, supporting adherence to evolving regulatory standards and maintaining user trust.
Effective deployment of these systems requires more than just technical integration. Teams should:
- Continuously update threat models as new attack vectors emerge in the wild.
- Automate incident response wherever possible to minimize human error and reduce reaction time.
- Regularly test alerting systems with simulated attacks to ensure reliability under pressure.
- Foster collaboration between security engineers, developers, and compliance teams so that findings from real-time scans translate into meaningful protocol upgrades.
The result: a dynamic defense-in-depth posture that evolves alongside both attacker capabilities and regulatory expectations.
What’s Next for Automated Security in Blockchain Bridges?
The next wave of innovation will see even tighter integration between AI-powered scanners, on-chain governance mechanisms, and automated remediation workflows. Imagine a scenario where detection of a suspicious cross-chain message instantly triggers a protocol-level pause or multi-sig review before any funds move, substantially raising the bar for would-be attackers. Leading solutions are already experimenting with predictive analytics to anticipate emerging threats based on patterns observed across multiple blockchains.
This relentless focus on proactive security is beginning to shift user expectations as well. Institutional capital is increasingly demanding continuous monitoring as a prerequisite for deploying assets across bridges. Retail users are seeking out protocols that publish transparent risk metrics powered by real-time data feeds rather than marketing promises alone.
If you’re looking to implement these capabilities yourself, our step-by-step guide at How to Use Cross-Chain Messaging Risk Scanners for DeFi Protocol Security details practical integration strategies, whether you’re securing an existing bridge or designing a new one from scratch.
The bottom line: The cost of ignoring continuous monitoring is simply too high in today’s high-stakes cross-chain environment. With over $3.2 billion lost since May 2021, every project must prioritize dynamic defenses that adapt at machine speed. The future of blockchain interoperability depends on it, and so does your protocol’s reputation.






