
In the world of blockchain interoperability, cross-chain bridges have become essential infrastructure. They enable users to move assets and data between different blockchains, unlocking new opportunities for decentralized finance (DeFi) and beyond. But with this innovation comes a new class of risks. One of the most pernicious is the message replay attack, a vulnerability that continues to plague bridge security and expose protocols to multimillion-dollar exploits.
How Do Message Replay Attacks Happen?
A message replay attack in cross-chain bridges occurs when an attacker intercepts a valid transaction or message from one blockchain and maliciously reuses it on another chain. This is possible when cross-chain protocols fail to properly distinguish which network a message originated from, or don’t enforce unique identifiers for each transaction. As a result, attackers can trick the bridge into processing the same action multiple times across different chains, often leading to unauthorized asset transfers or minting.
This threat isn’t just theoretical. In September 2022, Ethereum’s Proof-of-Work (PoW) fork was hit by such an exploit. The Omni bridge on EthereumPoW used an outdated chain ID and failed to verify the true source chain of incoming messages. Attackers were able to replay messages that had already been executed on Ethereum’s Proof-of-Stake (PoS) chain, siphoning off 200 ETHW after moving 200 WETH through the Gnosis chain’s Omni bridge. You can read more about this real-world incident in BlockSec’s detailed analysis: Reveal the “Message” Replay Attacks on EthereumPoW.
The Anatomy of Bridge Security Vulnerabilities
Bridge security replay vulnerabilities typically stem from inadequate validation mechanisms within cross-chain protocols. Many early designs overlooked critical fields like chain IDs, nonces (unique numbers per transaction), or contract addresses in their signature schemes. Without these anti-replay measures, signatures generated on one network can be accepted as valid on another – opening the door for attackers.
To better understand how these attacks unfold and what makes some bridges more vulnerable than others, consider these common weaknesses:
Key Causes of Message Replay Attacks in Cross-Chain Bridges
-
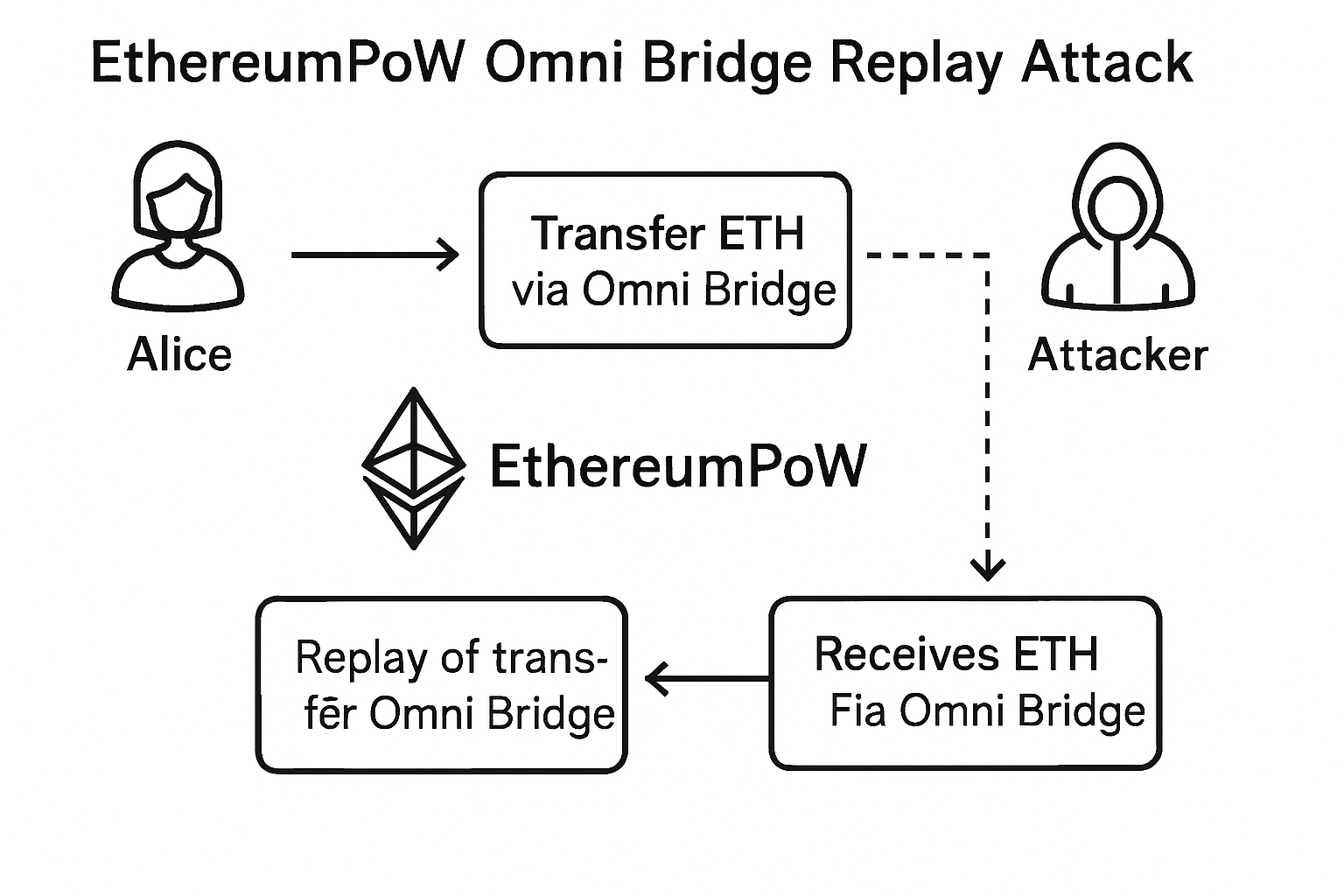
Omission of Chain ID in Message Validation: Failing to include the chain ID in cross-chain message signatures allows attackers to replay valid transactions on different blockchains. This was the main cause in the EthereumPoW Omni bridge replay attack, where an outdated or missing chain ID led to unauthorized asset transfers.
-

Lack of Unique Identifiers for Each Message: Without unique identifiers like nonces or message hashes, the same message can be broadcast multiple times. This allows attackers to execute duplicate transactions and exploit bridge protocols.
-
Improper Validation of Message Uniqueness: If a bridge does not strictly check whether a message has already been processed, it becomes vulnerable to replay attacks. Proper validation ensures each message is executed only once per destination chain.
-
Use of Outdated or Insecure Protocols: Relying on legacy systems or protocols that do not enforce modern anti-replay standards can expose bridges to attacks. Regular updates and audits are essential for maintaining security.
-
Compromised Validator or Bridge Keys: Attackers who gain access to bridge validators’ private keys can forge or replay messages across chains, draining funds or disrupting operations. Secure key management is critical for bridge security.
Mitigation Strategies: How Protocols Are Fighting Back
The good news is that awareness around cross-chain protocol attacks has led to stronger defenses across the ecosystem. Leading projects now incorporate multiple layers of anti-replay protection:
- Chain ID Inclusion: Always embedding both source and destination chain IDs within message signatures ensures that transactions are only valid for their intended network context.
- Unique Identifiers: Using nonces and contract addresses guarantees each cross-chain message is truly unique and cannot be reused elsewhere.
- Strict Validation Logic: Robust checking mechanisms prevent duplicate executions by tracking previously processed messages.
The Wormhole protocol offers a notable example here: it prevents VAA (Verifiable Action Approval) replay attacks by ensuring every message can only be delivered once on its target chain (Sec3 article on Wormhole prevention techniques). Similarly, best practices outlined by security auditors stress always including anti-replay fields in every cross-chain communication (CEEX Global guide on vulnerabilities).






