Cross-chain messaging protocols have become the backbone of blockchain interoperability, enabling asset transfers and data exchange between previously siloed networks. However, the complexity of these systems introduces a wide threat surface. Without a rigorous audit process, vulnerabilities can go unnoticed, leading to catastrophic exploits. The following cross-chain messaging audit checklist distills the most current security requirements and best practices into ten actionable items for protocol engineers and security teams.
Critical Audit Checks for Cross-Chain Messaging Protocols
1. Verify Message Authenticity and Integrity: Every cross-chain message must be cryptographically signed, with robust hashing to prevent tampering or spoofing in transit. This includes signing all relevant fields (token type, chain IDs, receiver address, amount, nonce) and using collision-resistant hash functions. Failing to do so exposes the protocol to forged messages or man-in-the-middle attacks.
2. Assess Authorization and Access Controls: Only authorized parties should be able to initiate or execute cross-chain actions. Audit all access control logic for lapses that could allow unauthorized relayers or contracts to submit fraudulent messages. Recent research highlights how weak authorization remains a common exploit vector in bridge incidents.
3. Evaluate Replay Protection Mechanisms: Replaying valid messages on different chains or at later times can drain funds or disrupt state consistency. Ensure implementation of nonces, unique message identifiers, or timestamp-based replay guards across all message types.
4. Test Bridging Contract Upgradability and Governance: Bridges often need upgrade paths for bug fixes or feature additions, but insecure upgradeability is a major risk. Review upgrade logic for timelocks, multi-sig governance controls, and transparent documentation of upgradability characteristics per chain as outlined in the OWASP Bridge Security Checklist.
5. Analyze Failure Handling and Rollback Logic: Cross-chain operations are susceptible to partial failures (e. g. , one chain confirms while another reorgs). Audit how the protocol detects delivery errors and whether it supports safe rollbacks or compensating transactions to avoid asset loss or inconsistent states.
External Dependencies and Monitoring
6. Review Dependency on External Relayers/Oracles: Many bridges depend on off-chain relayers or oracle networks for message delivery confirmation across chains. Scrutinize trust assumptions here: Are relayers decentralized? Is there slashing for misbehavior? What happens if a relayer is compromised?
7. Check Fee Payment and Gas Abstraction Mechanisms: Fee miscalculations are a frequent source of bugs in cross-chain protocols. Confirm that fee logic accounts for variable gas costs across chains, correctly deducts fees from users, and fairly distributes rewards to validators/relayers.
IBC vs LayerZero: Gas Abstraction Model Comparison
-
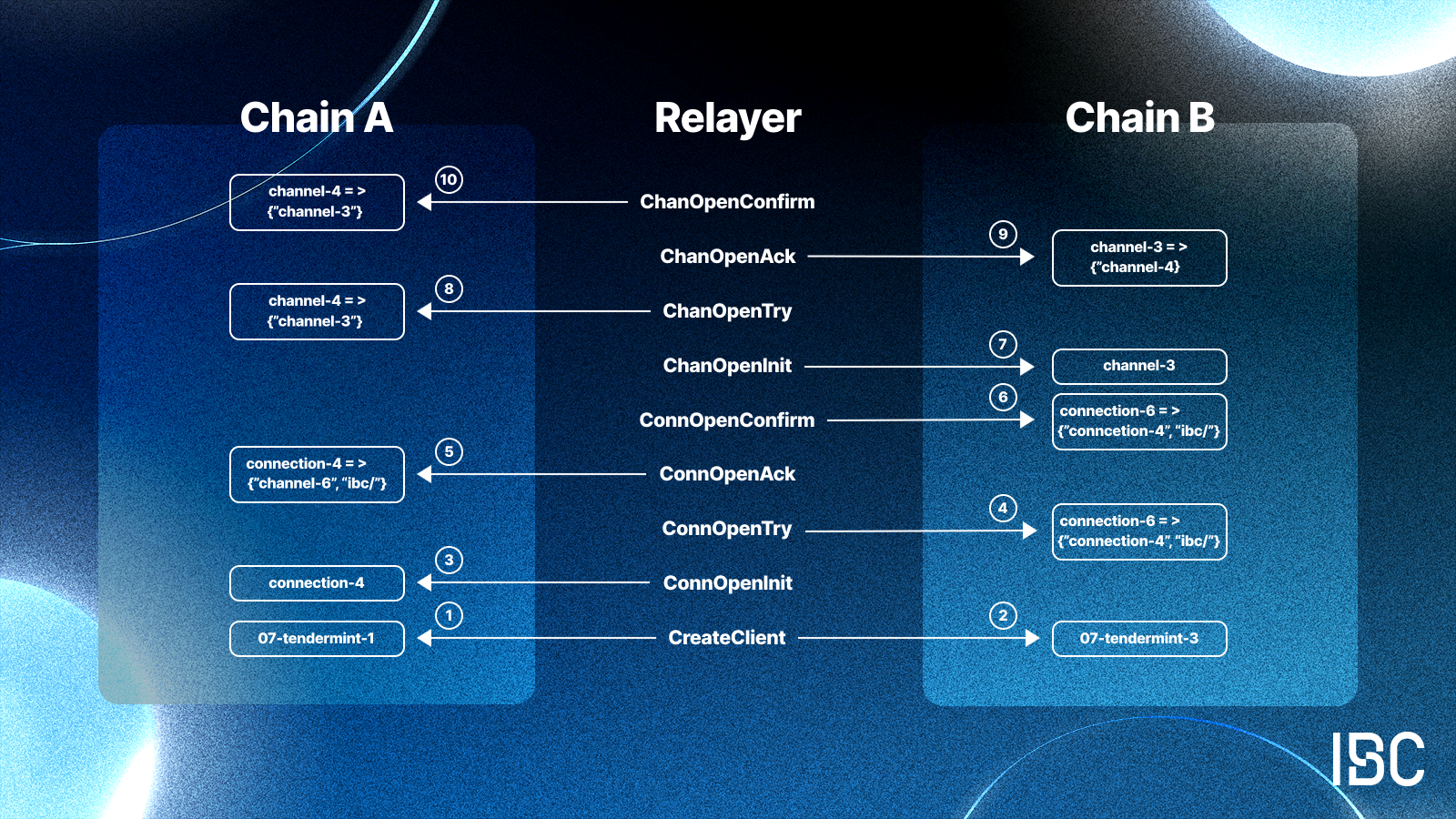
IBC (Inter-Blockchain Communication): IBC relies on the native gas model of each Cosmos SDK chain. Users must hold and pay gas in the destination chain’s native token, with no built-in gas abstraction. This model prioritizes security and sovereignty, but can increase user friction when interacting across multiple chains.
-
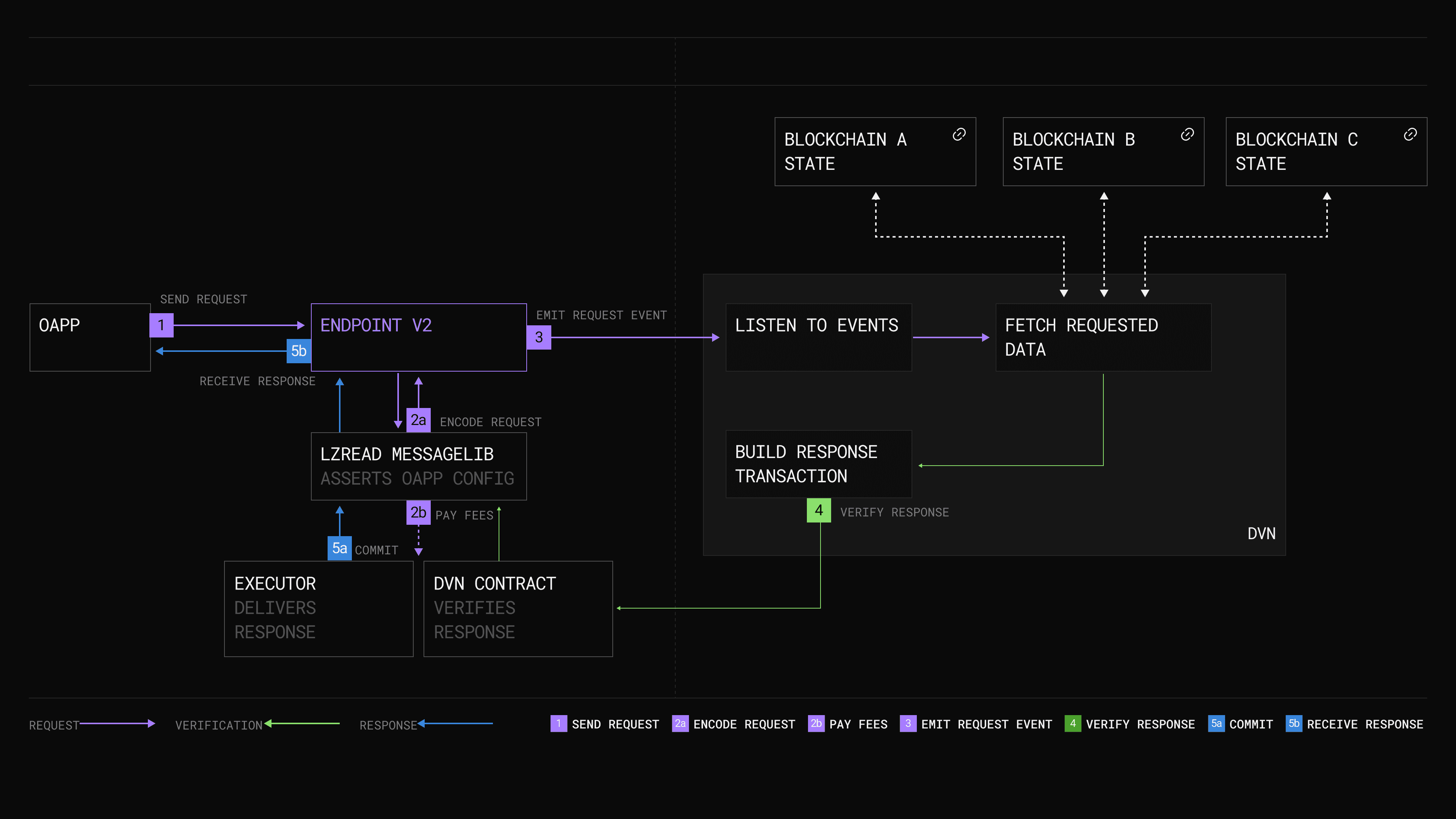
LayerZero: LayerZero implements a gas abstraction mechanism, allowing users to pay for remote execution gas fees on the destination chain using the source chain’s token. The protocol collects and forwards these fees to destination chain relayers, streamlining user experience but introducing additional trust assumptions in relayer operations.
Interoperability Testing and Security Best Practices
8. Inspect Event Logging and Monitoring Capabilities: Effective monitoring is crucial for early detection of anomalies such as double spends or failed deliveries. Audit that all critical events are logged with sufficient granularity for real-time monitoring systems like XChainWatcher (see case studies). Incident response plans should reference these logs directly.
9. Validate Compatibility with Supported Chains: Each supported network (EVM-compatible chains, Cosmos SDK zones, Substrate-based parachains) may handle transactions differently at the consensus level; test protocol logic against each environment to catch interoperability bugs before mainnet deployment.
10. Confirm Compliance with Latest Security Best Practices: Cross-reference your implementation against up-to-date guidelines such as the LayerZero V2 security checklist or IBC protocol docs (audit checklists here). Incorporate lessons learned from recent vulnerability disclosures affecting major bridges.






