
Imagine borrowing millions in crypto with no collateral, manipulating prices across chains, and walking away with a fat profit before anyone notices. That’s the nightmare flashloan exploits bring to cross-chain bridge oracles. Just look at Makina Finance: attackers snagged around $4 million using a massive USDC flashloan to twist their oracle feeds. It’s a stark reminder that in DeFi, speed kills if you’re not watching closely.

This isn’t isolated. Flashloans let attackers borrow huge sums instantly from protocols like Aave, pump liquidity pools, and fool oracles into reporting bogus prices. In cross-chain setups, these oracles are the weak link, verifying messages and asset values between blockchains. One slip, and bridges unlock funds on the wrong chain. As a trader who’s seen momentum flips wipe out gains, I say: respect the risk, or get rekt.
Makina’s $4M Meltdown: Oracle Tricks Exposed
Makina got hit hard. Hackers grabbed a 280 million USDC flashloan, flooded the USD-USDC pool to inflate prices, then drained 1,299 ETH worth about $4.1 million. Sources from Yahoo Finance to CryptoPotato paint the same picture: pure bridge oracle manipulation risks. The attacker manipulated price feeds tied to automated execution, exploiting how bridges rely on timely cross-chain data.
Why cross-chain bridges? They shuttle assets and messages via oracles that confirm events on source chains. Flashloans amplify this by creating artificial liquidity spikes in seconds. Without robust checks, oracles spit out lies, approving fake transfers. Makina’s case screams for better defenses in cross-chain messaging vulnerabilities.
Makina Flashloan Attack Steps
-
Borrow 280M USDC flashloan: Attacker borrows 280 million USDC via flash loan to initiate the exploit.
-
Inflate pool prices: Uses loan to inflate prices in Makina’s USD-USDC liquidity pool.
-

Trigger oracle misread: Manipulates oracle to misread inflated prices as real data.
-

Drain ETH via bridge: Exploits faulty oracle data to drain 1,299 ETH (~$4.1M) through cross-chain bridge.
-

Repay loan seamlessly: Returns flash loan plus fees, securing massive profit.
Flashloans vs. Bridge Oracles: The Perfect Storm
Cross-chain bridges aren’t just tunnels; they’re packed with oracles fetching real-time data. Attackers love them because flashloans reset every block. Borrow, manipulate, extract, repay – all atomic. In bridges, this means feeding false deposit proofs or message approvals. Webisoft nails it: non-decentralized oracles crumble under such pressure.
Think systemic risk. One manipulated oracle can cascade failures across lending protocols or DEXes relying on the bridge. We’ve seen $5M swings in DeFi from similar plays. My take? These aren’t black swans; they’re predictable if you scan right. Tools like decentralized oracle networks (DONs) and TWAP pricing help, but they’re bandaids without active monitoring.
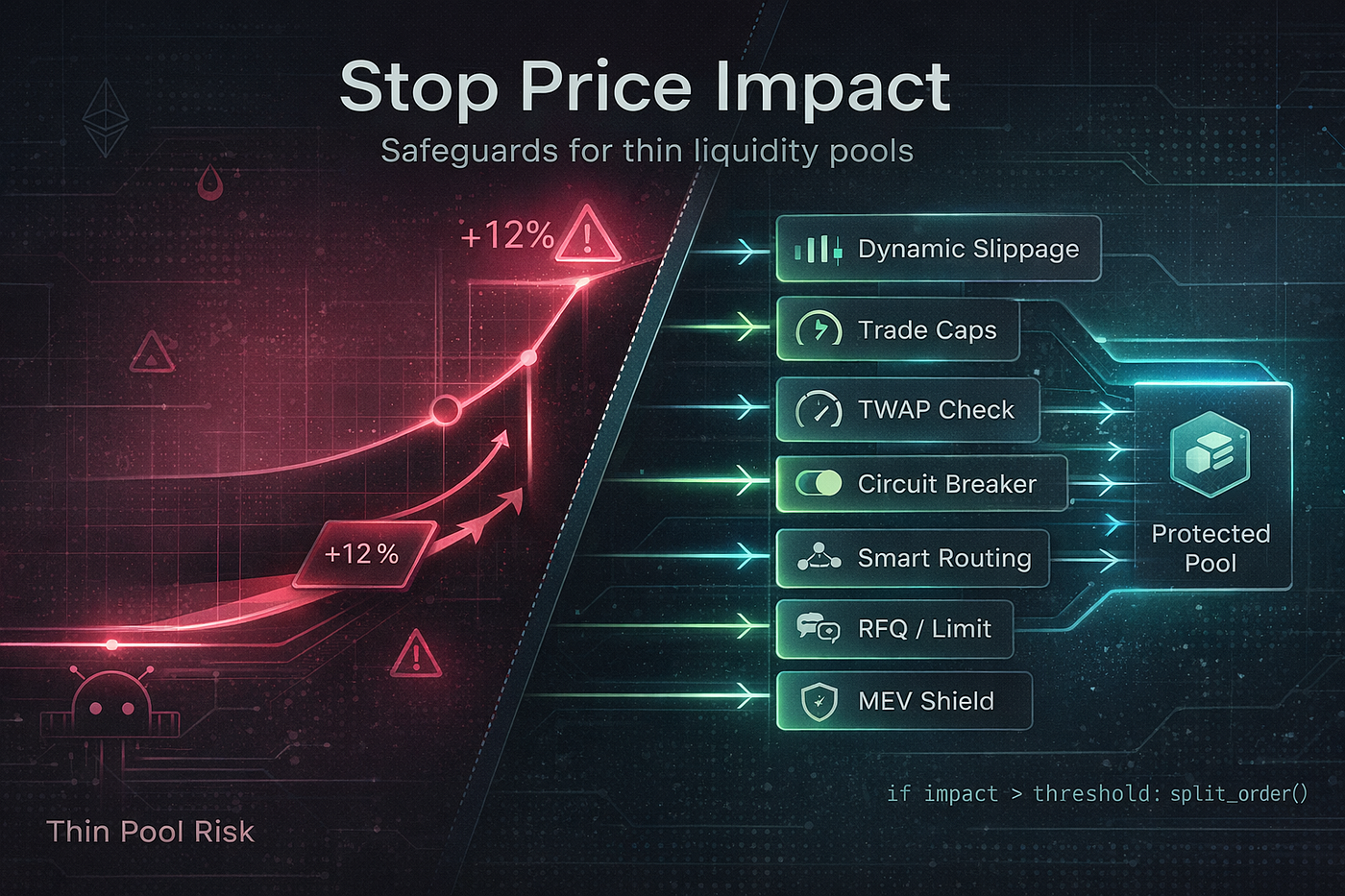
Risk Scanners: Your Frontline Against Flashloan Fury
Enter Cross-Chain Messaging Risk Scanners – our platform turns the tide. Real-time scans flag anomalies in bridge traffic, from unusual loan sizes to oracle divergences. Take XChainWatcher: open-source magic spotting exploits pre-loss. HighGuard models business logic violations across chains. Extractor by Hacken dives into transaction flows for compliance and threats.
These aren’t set-it-forget-it. They watch for flashloan cross-chain bridge exploits like Makinafi’s, alerting on manipulated feeds or rogue messages. As someone who rides trends, I motivate you: integrate scanners now. Spot transaction anomalies early, audit deep, stay secure. DeFi’s interoperable future demands it.
We’ve audited protocols mimicking Makina’s flaws, uncovering honeypots and vault risks. Pair that with QuillAudits’ breakdowns, and patterns emerge: always validate oracle data multi-source.
Patterns like these show up time and again in DeFi bridge security audits. Honeypots lure traders into traps, central vaults become single points of failure. We’ve linked scanners to real wins, like flagging the setups that led to 2.5B-scale hacks. Check our deep dives on honeypot patterns and vault risks – they reveal how proactive scanning stops the bleed.
Anatomy of Detection: Scanners in Action
Let’s break down how Cross-Chain Messaging Risk Scanners catch these beasts. We monitor oracle feeds for divergences – if prices spike unnaturally post-flashloan, alarms blare. XChainWatcher sifts bridge traffic for anomalies, like sudden volume surges mimicking Makinafi’s playbook. It’s open-source, so devs tweak it for custom chains.
HighGuard takes it further with DCR graphs, modeling expected contract flows. A flashloan skewing oracle inputs? It flags logic breaks instantly, cross-chain. Extractor by Hacken layers on transaction forensics, tracing manipulative paths before assets move. Together, they form a shield against bridge oracle manipulation risks.
Comparison of Risk Scanners for Flashloan Exploits in Cross-Chain Bridge Oracles
| Risk Scanner | Detection Capabilities | Key Features | Open-Source | Reference |
|---|---|---|---|---|
| XChainWatcher | Real-time anomalies | Monitors cross-chain bridges continuously; detects anomalies, potential attacks, and unintended behaviors; identified past exploits | ✅ Yes | [arxiv.org](https://arxiv.org/abs/2410.02029) |
| HighGuard | Logic violation detection | Uses dynamic condition response (DCR) graph models; monitors smart contracts across blockchains for business logic violations | No | [arxiv.org](https://arxiv.org/abs/2305.08254) |
| Extractor (by Hacken) | Transaction forensics & compliance | Real-time threat intelligence; deep visibility into transaction flows and contract behavior for suspicious activity detection | No | [extractor.live](https://www.extractor.live/bridges) |
Picture this: you’re bridging ETH to a lending protocol. Scanners spot the flashloan borrow, pool imbalance, oracle ping. No exploit completes without a red flag. I’ve traded through volatile swings; this tech gives the edge, turning defense into momentum.
Building Bulletproof Defenses: Practical Steps Forward
Scanners are step one. Layer on DONs for oracle redundancy – no single feed dominates. TWAP smooths out flashloan spikes, ignoring second-long pumps. Smart contracts need time-locks on big unlocks and multi-sig oracle confirms. For bridges, validate messages with zero-knowledge proofs; cut the oracle trust entirely where possible.
But don’t stop at tech. Audit religiously, simulate attacks. Makina’s makinafi exploit analysis from QuillAudits and PeckShield shows what slips through. Protocols ignoring cross-chain state checks invite chaos, especially in lending where inconsistencies amplify losses. See our take on message misdelivery risks.
Essential Flashloan Defenses
-
Multi-source oracle validation: Use networks like Chainlink DONs to cross-check data from multiple sources, preventing single-point manipulation as seen in Makina’s $4M exploit.
-
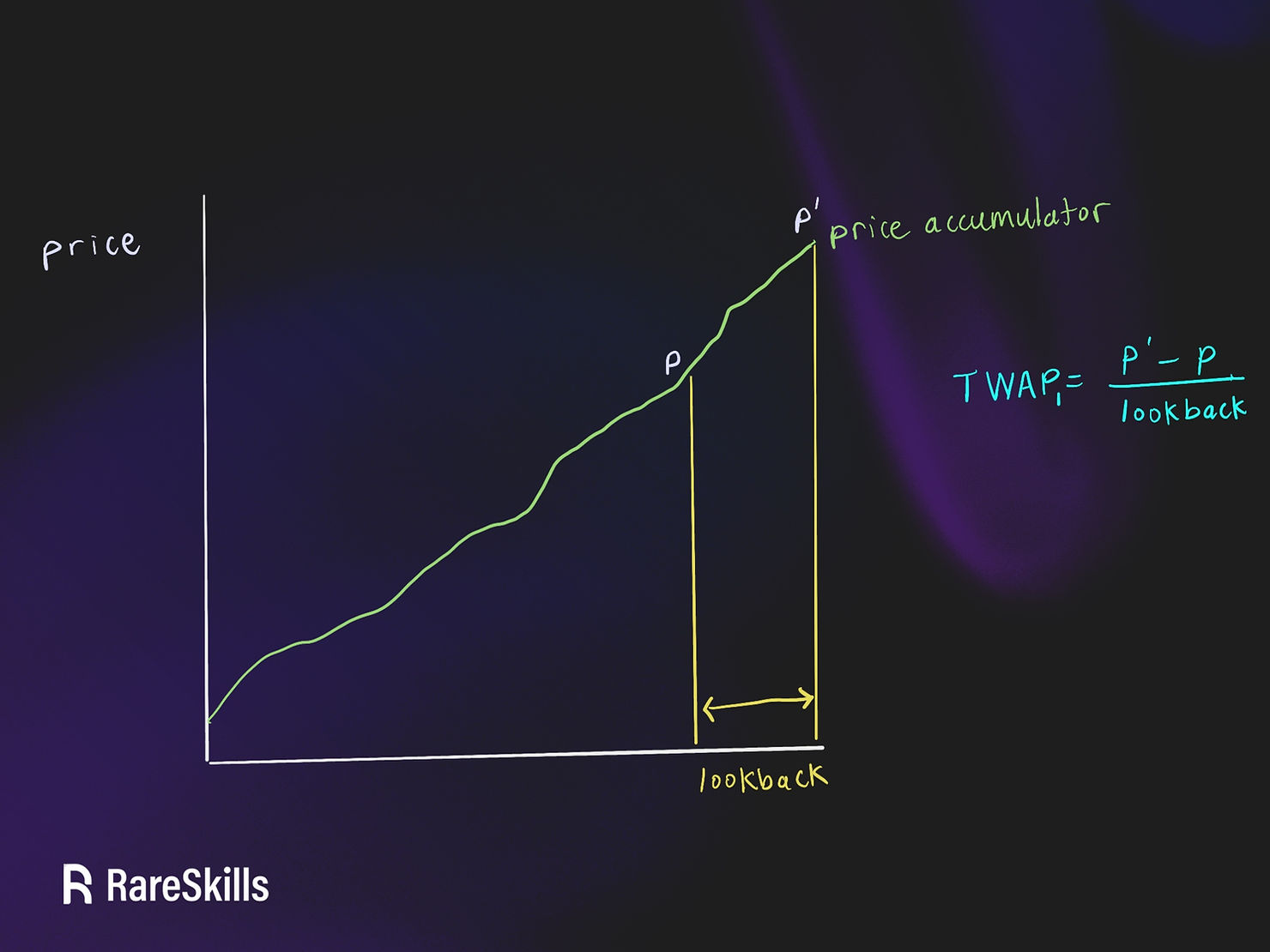
TWAP pricing mechanisms: Implement time-weighted average prices to smooth out flash loan spikes, a proven safeguard against oracle attacks highlighted in DeFi security analyses.
-
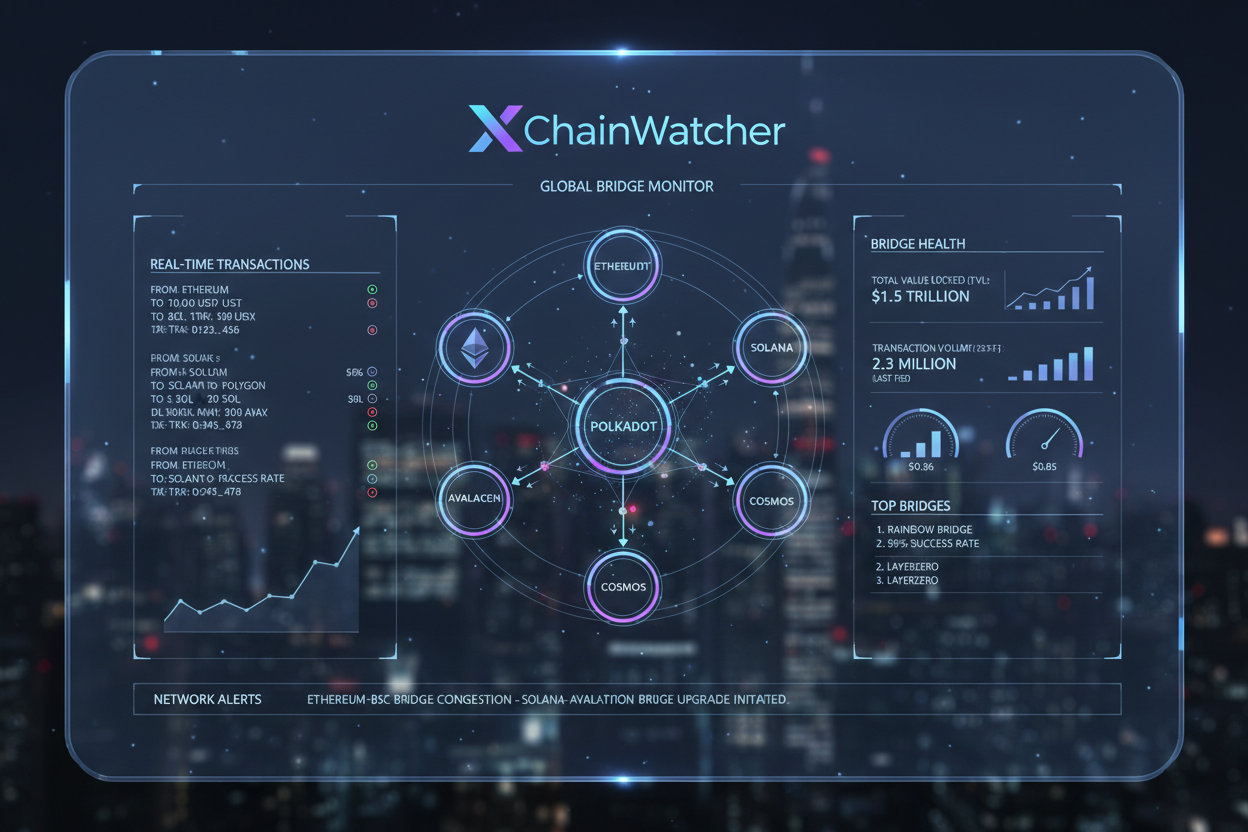
Real-time scanner integration: Integrate tools like XChainWatcher, HighGuard, or Extractor by Hacken for anomaly detection in cross-chain bridges.
-
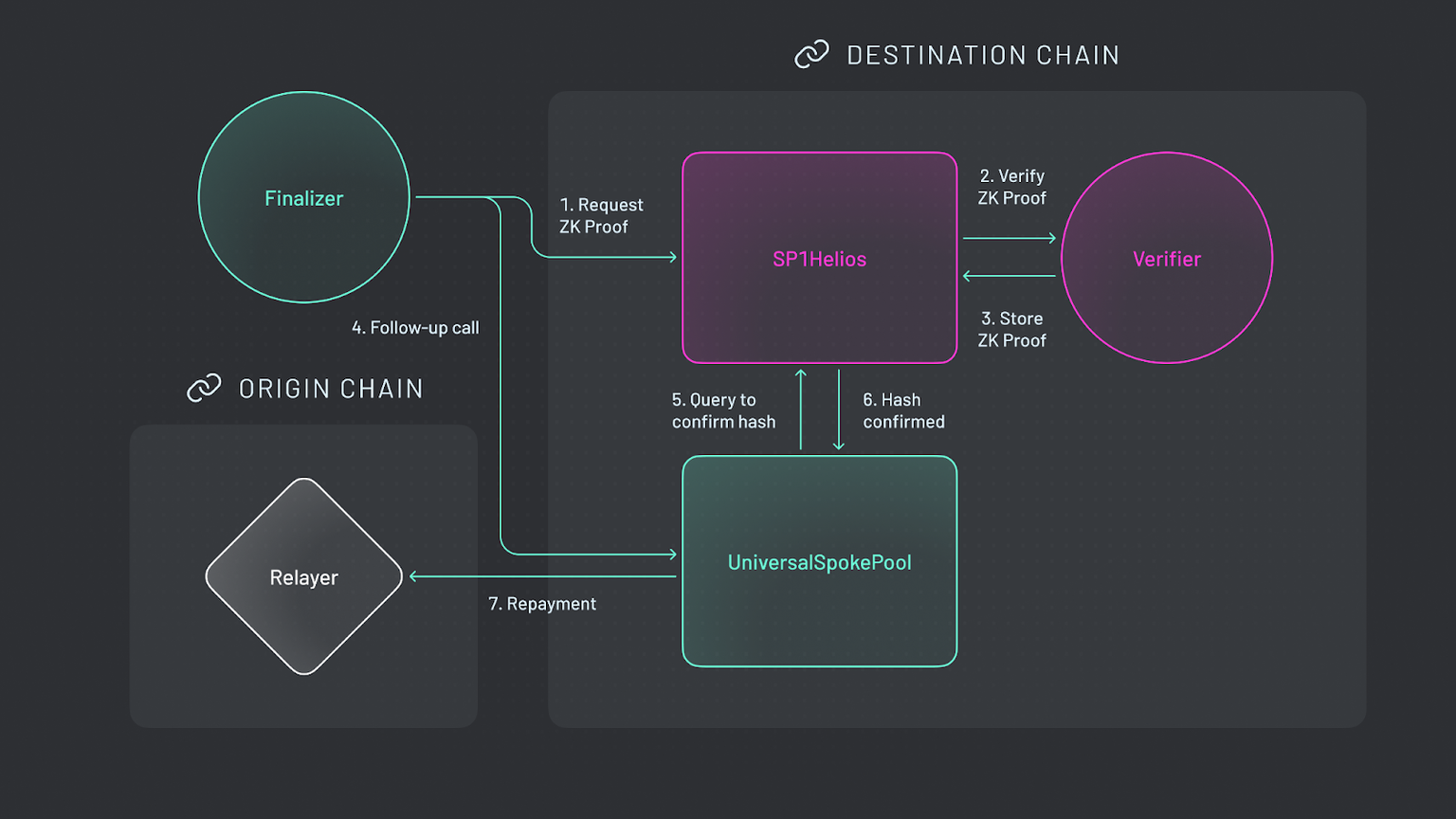
ZK-proof message relays: Employ zero-knowledge proofs for secure, verifiable cross-chain messaging, thwarting fake data feeds in bridges.
-
Regular attack simulations: Conduct red-team exercises and simulations to expose vulnerabilities before attackers do, building resilience like top protocols.
Traders and builders, listen up: DeFi’s cross-chain boom is here. Billions flow daily through bridges. One unchecked oracle, and it’s game over. Risk Scanners aren’t optional; they’re your trend rider’s toolkit. Spot cross-chain messaging vulnerabilities scanners miss? Nah, we evolve with the threats.
Flashloans evolve, but so do we. From Makina’s $4.1 million wake-up to the next frontier, stay vigilant. Ride the interoperability wave smartly – respect the risk, scan relentlessly, and watch your portfolio thrive.






