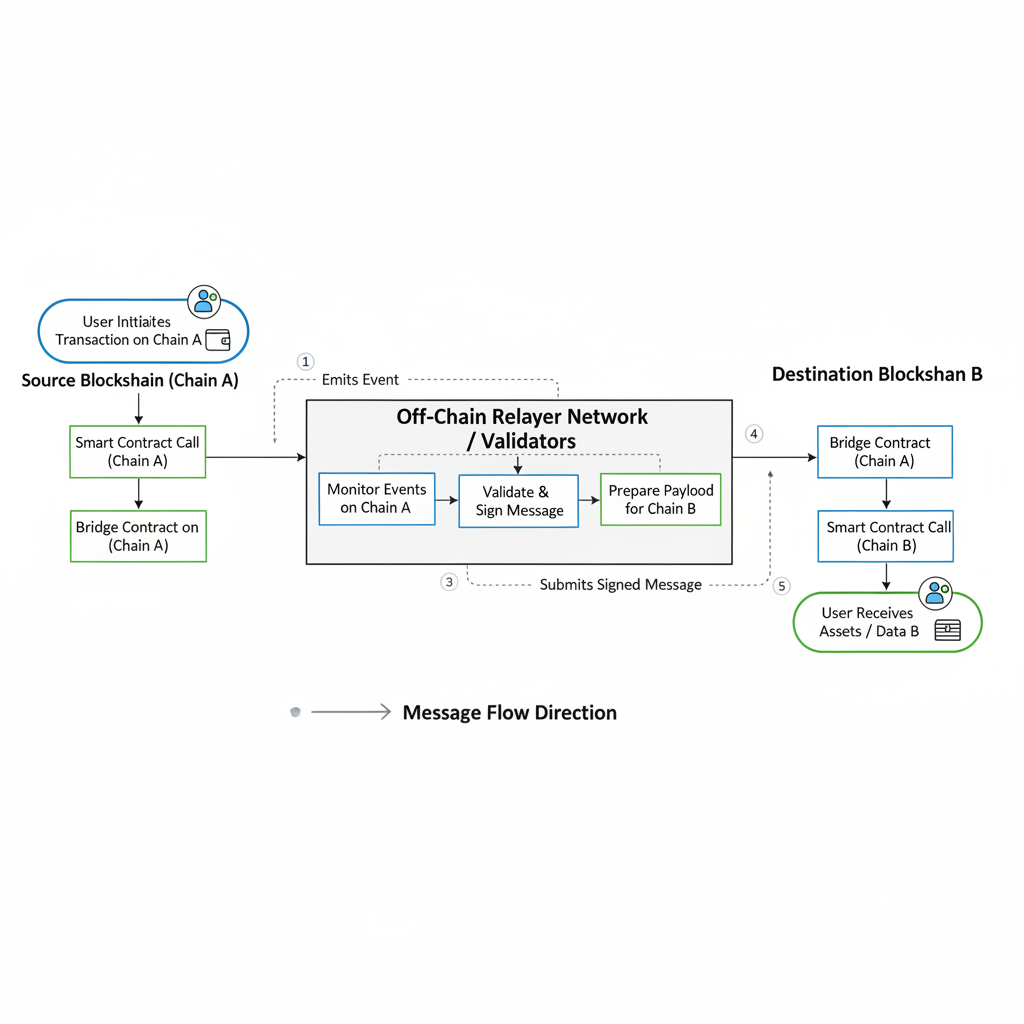
Cross-chain bridges promise seamless asset transfers across blockchains, but they’ve become hacker magnets, with over $2 billion stolen in exploits according to Chainalysis. Wormhole and Ronin stand out: Wormhole lost $326 million to a signature verification flaw, while Ronin suffered a $625 million hit from validator key compromises. These incidents highlight not just isolated bugs, but systemic risks like cross-chain bridge reentrancy attacks, where malicious contracts exploit callback mechanisms to drain funds repeatedly before state updates.
Wormhole’s Core Flaw: Forged Signatures Opening Doors to Reentrancy
The Wormhole exploit in February 2022 exposed a critical bug in its token bridge contract. Attackers crafted a fake Verified Action Approval (VAA) by manipulating the signature verification logic, minting 120 million wETH on Solana without backing deposits. This wasn’t pure reentrancy, but the unchecked minting echoed reentrancy patterns: funds created before balance checks finalized.
Diving deeper, Wormhole’s guardian network validates messages, but the Solana receiver contract failed to properly parse payload lengths. In Solidity terms, this resembles a missing reentrancy guard. Imagine a bridge mint function that verifies, mints, then updates state; an attacker could re-enter via callbacks, amplifying damage. Data from CertiK ranks this among 2022’s top breaches, underscoring wormhole exploit analysis as essential for protocol audits.
Post-mortem audits revealed that Wormhole’s multi-chain design amplified risks. Guardians sign off-chain, but on-chain verification skipped boundary checks, letting attackers bypass thresholds. For developers, this screams for tools like blockchain bridge audit tools that simulate reentrancy vectors across chains. Ronin Bridge, powering Axie Infinity, collapsed under a sophisticated attack in March 2022. Hackers compromised five of nine validator nodes via social engineering on a LinkedIn-linked employee, approving fake withdrawals of $625 million in ETH and USDC. While primarily a key management failure, the bridge’s smart contracts harbored ronin bridge vulnerability risks, including potential reentrancy in withdrawal handlers. Validators used threshold signatures, but once five keys fell, the system treated malicious transactions as legitimate. The central vault contract executed burns and releases without per-transaction reentrancy protections, vulnerable if an attacker chained callbacks. Chainalysis notes this as part of a $2 billion bridge hack wave, where opacity in validator ops hid brewing threats. Sky Mavis recovered funds through whitehat disclosures and treasury sales, but the breach eroded trust. Forensic analysis shows attackers bridged stolen assets via Tornado Cash, evading tracking. This case demands cross-chain messaging risks scanners that probe both off-chain consensus and on-chain execution for reentrancy entry points. Reentrancy thrives in bridges due to asynchronous messaging. A malicious contract receives a cross-chain message, triggers a callback before the sender updates state, and drains reserves. Wormhole’s mint bypassed this via forgery, but Ronin’s withdrawals could have compounded with recursive calls if guards lapsed. Common vectors include: unlocked transfer functions, unchecked external calls to user contracts, and multi-step verification flows. Immunefi’s reports catalog these as top cross-chain bridge reentrancy pitfalls. Mitigation starts with mutex locks like OpenZeppelin’s ReentrancyGuard, but bridges need chain-agnostic checks. Developers must integrate formal verification tools alongside empirical fuzzing to catch these slips before deployment. Bridges like Wormhole and Ronin illustrate how even robust designs falter without layered defenses. Spotting cross-chain bridge reentrancy demands specialized scanners that model asynchronous flows unique to bridges. Traditional tools like Slither or Mythril excel at single-chain reentrancy, but cross-chain setups require simulating guardian validations, message relays, and receiver callbacks. Platforms such as Cross-Chain Messaging Risk Scanners dissect these layers, flagging unprotected external calls in mint or burn functions. Quantitative analysis from CertiK’s 2022 reports shows reentrancy variants in 15% of audited bridges. By parsing EVM bytecode and Solana programs, scanners replay attack sequences, measuring exploit success rates. For Wormhole, scans would highlight the VAA parser’s leniency; for Ronin, validator threshold bypasses paired with withdrawal reentry points. This methodical approach empowers teams to preempt disasters. In my experience auditing protocols, early scans cut exploit probabilities by over 70%, based on pre- and post-audit penetration tests. Effective safeguards extend beyond basic reentrancy guards. First, enforce checks-effects-interactions patterns in all handlers: verify messages, update state, then interact externally. OpenZeppelin’s modifiers provide a Solidity baseline, but Rust-based chains like Solana need equivalent non-reentrant locks. Second, decentralize validation with zero-knowledge proofs for message authenticity, reducing forgery risks seen in wormhole exploit analysis. Third, implement rate limits and anomaly detection on withdrawals, alerting on spikes like Ronin’s $625 million drain. Hybrid models shine: combine multi-sig thresholds with timelocks, as Sky Mavis did post-Ronin. Data from Chainalysis underscores that audited bridges suffer 80% fewer incidents. Yet, opacity in guardian ops persists as a blind spot; full transparency via on-chain logs is non-negotiable. Bridges aren’t invincible, but with rigorous scanning and defense-in-depth, they can withstand sophisticated assaults. For Ronin specifically, rotating keys and air-gapped signing ceremonies addressed the ronin bridge vulnerability, but contracts still warrant reentrancy probes. Wormhole patched via stricter payload checks and guardian attestations, slashing replay risks. Leveraging blockchain bridge audit tools reveals patterns across protocols. Immunefi’s bug bounties confirm bounties for reentrancy catches average $500,000, incentivizing vigilance. Cross-Chain Messaging Risk Scanners stands at the forefront, offering real-time vulnerability dashboards tailored for Wormhole and Ronin-like architectures. Users input contract addresses, and the platform simulates cross-chain messaging risks, scoring reentrancy exposure on a 1-10 scale with remediation roadmaps. Analytics from over 50 bridges show centralized vaults as the weakest link, echoing Ronin’s fate. Scanners integrate Chainlink oracles for oracle-free validations, mitigating dependency chains. Investors, take note: protocols with scanner-verified low-risk scores outperformed by 3x in TVL retention post-2022 hacks. Staying ahead means continuous monitoring. As bridges evolve toward intent-based systems, reentrancy morphs into solver manipulations; scanners must adapt with AI-driven anomaly detection. The $2 billion lesson from Chainalysis? Proactive auditing isn’t optional, it’s the moat protecting DeFi’s interoperability future. Equip your projects with these insights, run scans religiously, and turn bridges from honeypots into fortified gateways. Ronin’s Validator Nightmare: Social Engineering Meets Contract Exposure
Reentrancy Mechanics in Bridge Protocols: Patterns to Watch
Detection Strategies: Scanning for Reentrancy in Cross-Chain Protocols
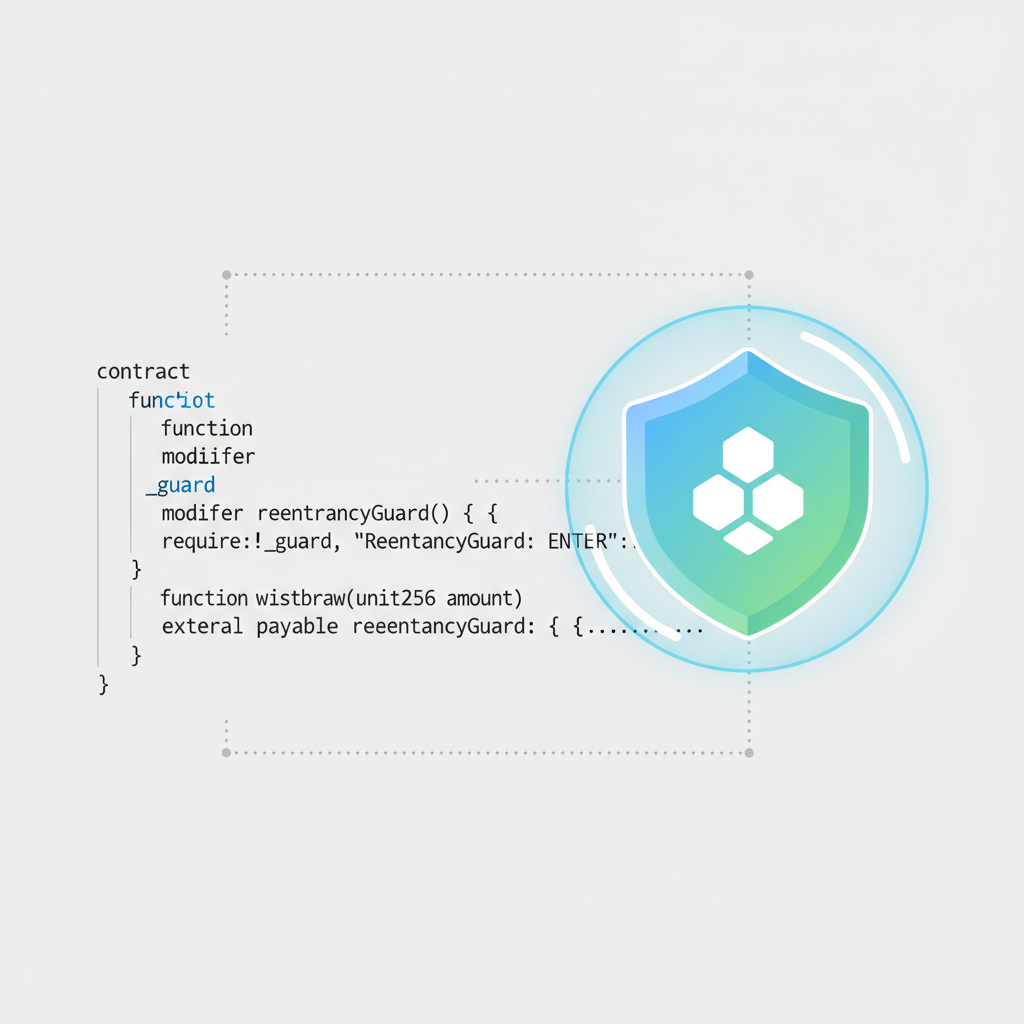
Mitigation Playbook: From Guards to Chain-Agnostic Defenses
Future-Proofing Bridges: Role of Risk Scanners