
Cross-chain bridges have become the connective tissue of the blockchain world, enabling assets and data to flow between siloed networks. As of 2025, however, these bridges remain the single most lucrative and persistent target for attackers in DeFi. While their existence is critical for interoperability and liquidity, their complexity introduces a unique set of vulnerabilities that have cost users billions.

Why Cross-Chain Bridges Are Still Hacker Honeypots
The numbers are stark: more than $2.8 billion has been lost to cross-chain bridge exploits as of late 2025, dwarfing losses in other DeFi sectors. The reason? Bridges aggregate massive pools of value and rely on intricate technical architectures that often blend on-chain logic with off-chain actors. This makes them a perfect storm for security weaknesses.
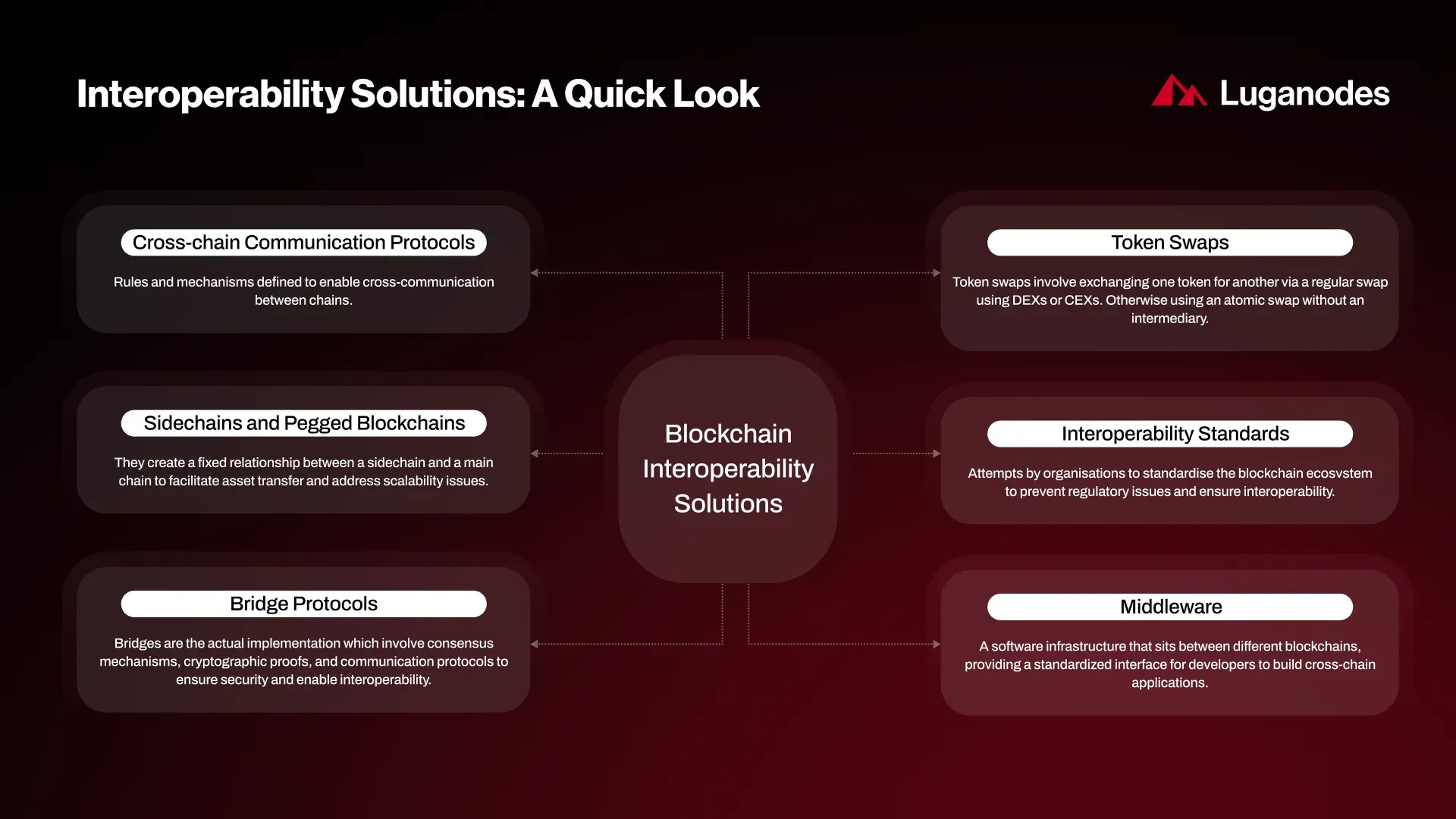
Let’s break down the seven most critical vulnerabilities plaguing cross-chain bridge security in 2025, each representing a distinct attack vector that continues to be exploited by sophisticated adversaries:
The Seven Most Critical Bridge Vulnerabilities (2025)
- Compromised Validator or Relayer Keys: Attackers who gain access to validator or relayer keys can approve fraudulent transactions and drain bridge funds in minutes. This was the root cause behind several headline-making hacks this year.
- Smart Contract Logic Flaws: Complex bridging logic is fertile ground for bugs, replay attacks, incorrect state validation, or unauthorized minting are just a few examples. Even minor oversights can lead to catastrophic losses.
- Insufficient Decentralization of Bridge Consensus: Many bridges still rely on a handful of validators or multisig signers. This limited decentralization makes collusion or targeted attacks feasible, undermining the trust-minimized ethos of blockchain itself.
- Insecure Message Passing Protocols: Weaknesses such as lack of authentication or replay protection in cross-chain messaging allow attackers to forge instructions and siphon assets. Secure message verification remains an unsolved challenge for many protocols.
- Upgradable Contract Exploits: Bridges often feature upgradeable contracts for flexibility, but if governance controls are compromised, attackers can deploy malicious upgrades and seize control over assets without detection.
- Lack of Timely Risk Detection and Response: Without real-time monitoring and automated risk scanners, attackers enjoy long windows to exploit vulnerabilities before anyone notices, a recurring theme in recent multi-million dollar breaches.
- Oracle Manipulation Attacks: Heavy reliance on single or poorly-secured oracles exposes bridges to price feed manipulation or fake event injection, enabling attackers to mint unbacked tokens or trigger false transfers across chains.
The Anatomy of Modern Bridge Attacks
No vulnerability exists in isolation, attackers often chain multiple weaknesses together for maximum impact. For instance, an attacker might first compromise validator keys (Vulnerability #1), then exploit smart contract flaws (Vulnerability #2) to authorize unauthorized asset mints. In several high-profile incidents this year, insecure upgrade mechanisms (Vulnerability #5) were used as backdoors after initial access was gained through key theft.
This layered exploitation is precisely why even well-audited bridges remain at risk if they lack robust real-time risk detection (Vulnerability #6) and strong decentralization models (Vulnerability #3). The interplay between technical flaws and governance gaps creates an ever-shifting threat landscape that traditional audits alone cannot fully address, a reality explored in greater depth in our guide on why cross-chain bridges remain the biggest target in DeFi.
The High Cost of Oracle Manipulation and Message Forgery
A particularly insidious threat comes from oracle manipulation (Vulnerability #7) and insecure message passing (Vulnerability #4). Because bridges depend on external data sources for state verification, such as confirming deposits on one chain before releasing tokens on another, an attacker who compromises an oracle can effectively create assets out of thin air. Similarly, if message replay protections are inadequate, previously valid messages can be resent to trigger repeated asset releases.
This isn’t just theoretical: several attacks this year combined oracle spoofing with forged messages to bypass checks entirely, highlighting why trust-minimized design isn’t just about decentralizing validators but also about hardening every layer where external data meets core protocol logic.
As the cross-chain ecosystem matures, it’s clear that bridge security is a moving target. Attackers are not just exploiting code, they’re probing every aspect of protocol design, from governance and upgradeability to the very mechanisms that detect and respond to threats. The lack of timely risk detection (Vulnerability #6) remains a glaring weakness. In 2025, several major breaches went undetected for hours or even days, allowing attackers to maximize their gains before protocols could react. This highlights an urgent need for real-time monitoring and automated risk scanning tools tailored specifically for cross-chain environments.
Another recurring weakness is the upgradability of contracts (Vulnerability #5). While upgradeable contracts allow teams to patch bugs and add features, they also introduce a new class of risks: if governance or admin controls are compromised, an attacker can deploy malicious logic directly into production. This was the vector behind multiple high-profile exploits where attackers seized control over bridge contracts by manipulating poorly secured upgrade paths.
Why Traditional Audits Aren’t Enough
Despite rigorous smart contract audits, bridges continue to fall victim to multi-stage attacks that combine social engineering, governance manipulation, and technical exploits. Audits often focus on code quality but may overlook operational security, such as how validator keys are stored (Vulnerability #1) or how consensus is achieved (Vulnerability #3). As a result, even well-reviewed bridges can become sitting ducks if their validator set is too small or their admin keys are poorly protected.
This underscores why insufficient decentralization (Vulnerability #3) isn’t just a theoretical concern: when control rests in too few hands, the entire system inherits their weaknesses. Increasing validator diversity and eliminating single points of failure must be priorities for any bridge protocol aiming for long-term resilience. For further reading on how trust models shape risk profiles in cross-chain bridges, see our deep analysis at this resource.
Building Safer Cross-Chain Bridges in 2025
The path forward requires more than incremental improvements, it demands a holistic rethink of how we architect interoperability. Here’s what leading teams are prioritizing:
Top 7 Cross-Chain Bridge Vulnerabilities in 2025
-

Compromised Validator or Relayer Keys: Attackers who gain control over validator or relayer keys can approve fraudulent cross-chain transactions, draining bridge funds and causing massive financial losses. This risk is heightened in bridges using multisig wallets or limited validator sets.
-

Smart Contract Logic Flaws: Bugs or overlooked edge cases in bridge smart contracts can enable exploits such as replay attacks, incorrect state validation, or unauthorized asset minting—often resulting in significant asset theft.
-

Insufficient Decentralization of Bridge Consensus: Bridges that rely on a small set of validators or multisig signers are vulnerable to collusion or targeted attacks, undermining the trust-minimized model essential for blockchain security.
-
Insecure Message Passing Protocols: Weaknesses in cross-chain messaging—such as lack of authentication or message replay protection—can allow forged instructions and asset theft, making robust protocol design essential.
-

Upgradable Contract Exploits: Attackers exploit insecure upgrade mechanisms to deploy malicious contract versions, often by compromising governance or admin controls, leading to unauthorized changes and potential bridge takeovers.
-
Lack of Timely Risk Detection and Response: The absence of real-time monitoring and automated risk scanners allows attackers to exploit vulnerabilities for extended periods before detection, increasing potential losses.
-

Oracle Manipulation Attacks: Dependence on a single or compromised oracle for price feeds or state verification enables attackers to manipulate bridge operations and siphon assets, highlighting the need for robust oracle design.
1. Automated Risk Scanning and Monitoring: Deploying real-time scanners designed to detect anomalous transactions and governance actions across all layers of the bridge stack.
2. Trust-Minimized Architectures: Moving away from multisig-based control towards decentralized validation mechanisms that reduce reliance on any single party or group.
3. Hardened Message Passing: Implementing robust authentication and replay protection in messaging protocols to thwart forgery attempts.
4. Secure Upgrade Paths: Limiting upgradability through time locks, multi-party approvals, and transparent governance processes that make unauthorized upgrades nearly impossible.
5. Oracle Diversity and Verification: Utilizing multiple independent oracles with cryptographic proofs rather than relying on single data feeds.
Staying Ahead in an Adversarial Environment
The reality is that attackers will always seek out new angles, no matter how hardened your codebase may be today. The most resilient bridges are those whose teams embrace continuous improvement: regularly rotating keys, decentralizing consensus further over time, conducting live-fire incident response drills, and adopting community-driven monitoring solutions.
If you’re building or using cross-chain infrastructure in 2025, treat these seven vulnerabilities as your baseline checklist, not as rare edge cases but as likely attack surfaces that require constant vigilance. For more tactical guidance on securing your protocol against these evolving threats, and why trust-minimized architectures represent the future, explore our comprehensive guide at this link.






