In 2025, cross-chain bridges have become the most lucrative target for blockchain attackers, accounting for over $3 billion in losses during the first half of the year. While these protocols promise seamless interoperability and composability across disparate blockchains, their complexity and central role in DeFi infrastructure have exposed a series of vulnerabilities that are being ruthlessly exploited by sophisticated adversaries. Understanding why bridges are so persistently attacked – and how these attacks succeed – is critical for anyone operating in the DeFi or Web3 space.
![]()
Why Cross-Chain Bridges Dominate Blockchain Attack Vectors in 2025
The fundamental challenge with cross-chain bridges is their position as custodians of massive pooled assets and their reliance on intricate mechanisms to coordinate state between blockchains. As a result, a successful exploit can net attackers not just isolated funds but vast troves spanning multiple chains. The multifaceted risk profile of bridges has led to an arms race between security researchers and malicious actors, with the latter often staying one step ahead.
This year’s most damaging incidents – from the Bybit Exchange hack ($1.5 billion in Ethereum stolen) to the Force Bridge exploit ($3 million siphoned via Tornado Cash) – all share a common thread: exploitation of core weaknesses unique to bridge architecture. The following seven vulnerabilities have repeatedly surfaced as root causes behind these breaches.
The Seven Most Critical Cross-Chain Bridge Vulnerabilities Explained
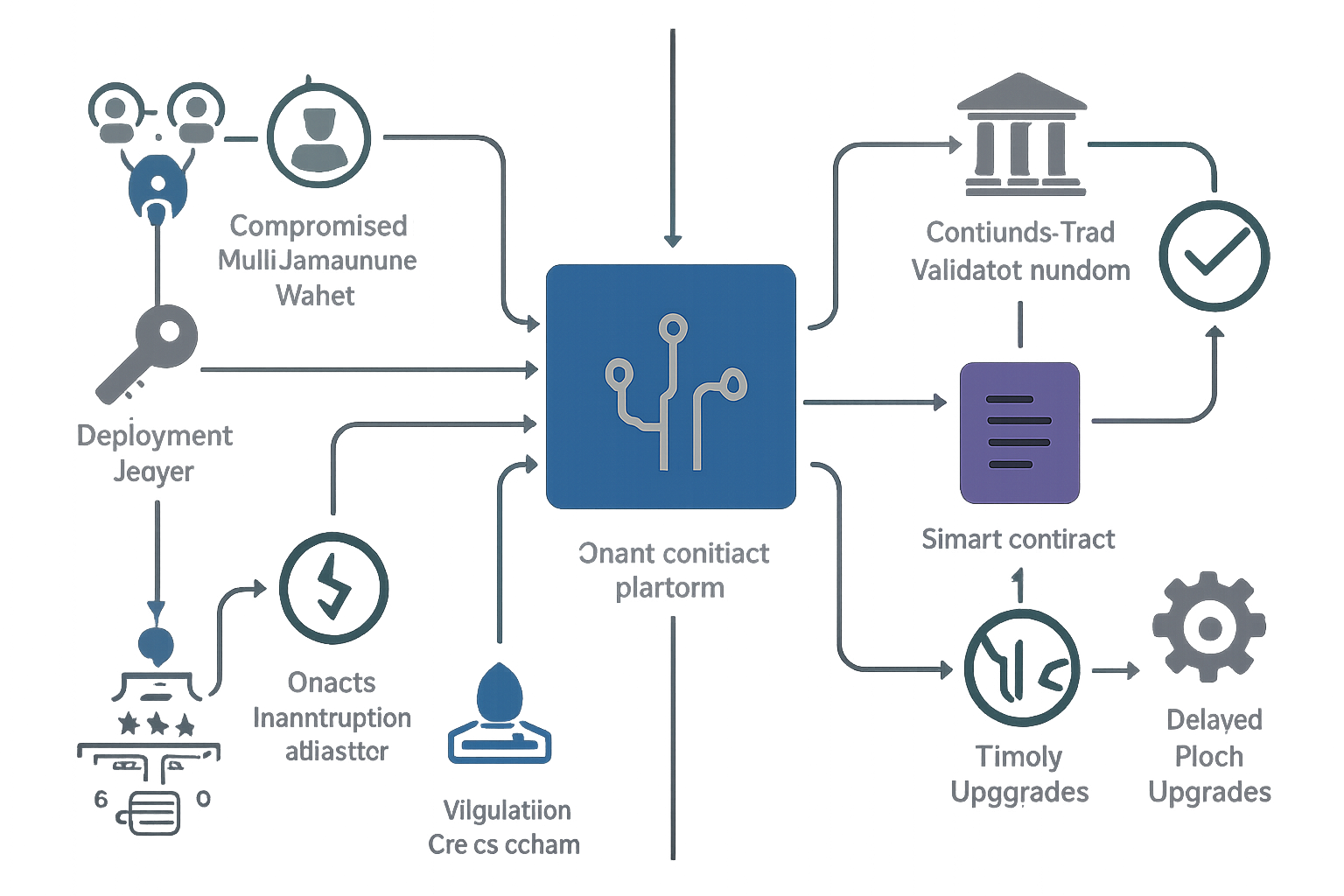
Top 7 Cross-Chain Bridge Vulnerabilities in 2025
-
Compromised Multi-Signature Wallets: Attackers exploit weaknesses in multi-sig setups, often through social engineering or phishing, to gain control over bridge governance and asset transfers. The UXLINK multisig breach in 2025 is a prime example of this risk.
-

Stolen or Leaked Deployment Keys: Unauthorized access to bridge deployment keys enables attackers to deploy malicious contracts or mint unbacked tokens. Several high-profile 2025 hacks, including the September DeFi bridge exploit, leveraged this vulnerability.
-
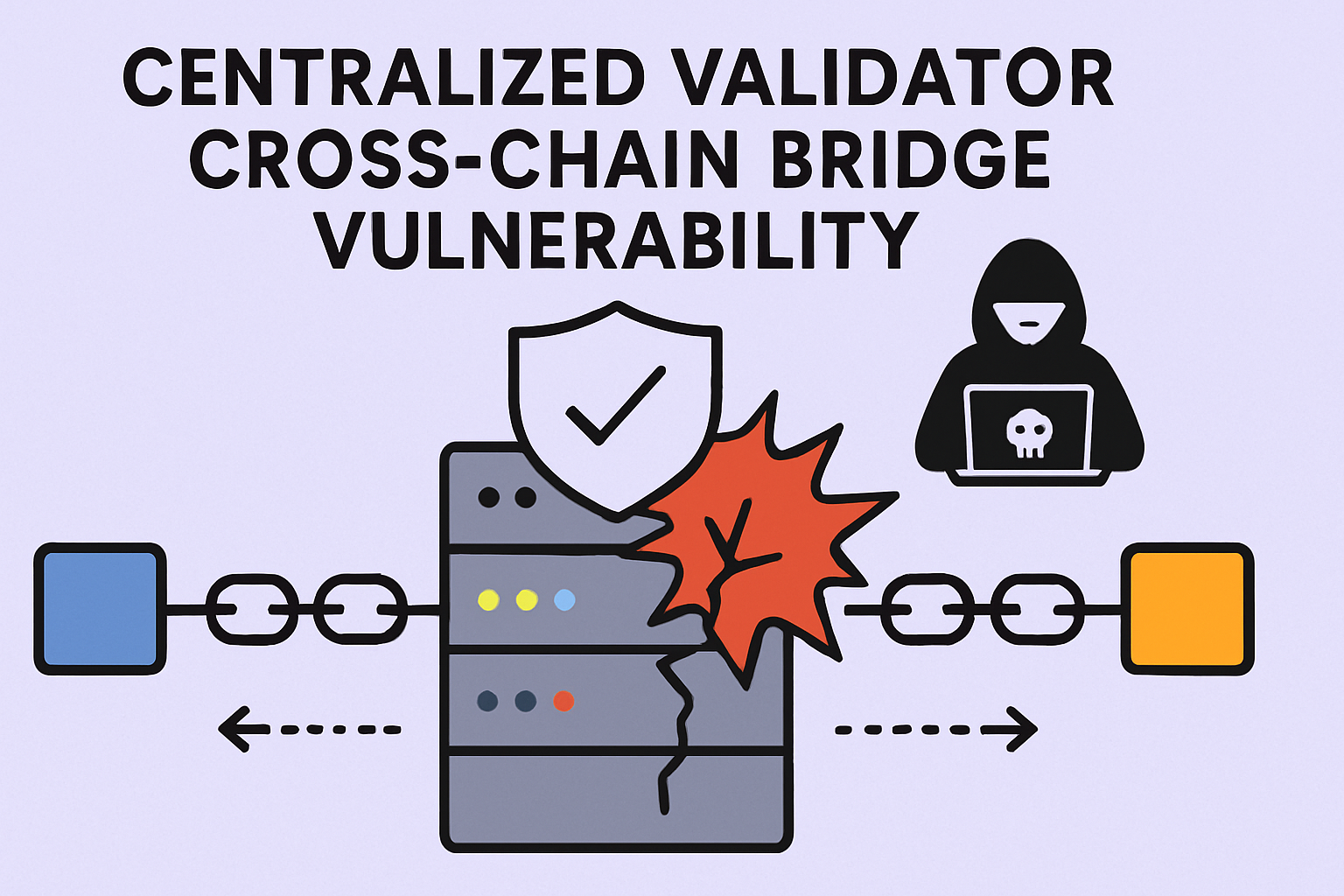
Centralized Validator/Custodian Risks: Bridges relying on centralized validators or custodians become single points of failure. This centralization makes them attractive targets for coordinated attacks or insider threats, as highlighted in recent research and incidents.
-

Smart Contract Logic Flaws: Vulnerabilities in cross-chain contract code, such as improper validation of messages or replay attacks, allow attackers to manipulate bridge operations and siphon funds. The Balancer V2 $128M exploit in 2025 exposed such risks.
-
Insecure Cross-Chain Messaging Protocols: Weaknesses in message verification or lack of cryptographic guarantees can lead to forged cross-chain transactions and asset theft, undermining the trust in bridge infrastructure.
-
Oracle Manipulation Attacks: Attackers exploit delays, inaccuracies, or manipulation in price or state oracles used by bridges to trigger fraudulent transfers or liquidations, a persistent risk in multi-chain DeFi systems.
-

Lack of Timely Upgrades and Patch Management: Slow response to emerging threats and delayed patching of known vulnerabilities leave bridges exposed to exploits targeting outdated code, as seen with several bridge hacks in 2025.
about “A ranked list of the seven most critical vulnerabilities affecting cross-chain bridges in 2025, based on real-world incidents and current security research”
- Compromised Multi-Signature Wallets: Many bridges rely on multi-signature (multi-sig) wallets for governance and asset transfers. In theory, requiring multiple parties to sign transactions should prevent unilateral control. In practice, attackers use social engineering, phishing campaigns, or malware to compromise enough key holders to gain majority control. The UXLINK multisig breach is a recent example where this vulnerability led to catastrophic losses.
- Stolen or Leaked Deployment Keys: Unauthorized access to deployment keys enables attackers to deploy malicious contracts or mint unbacked tokens at will. September’s DeFi hacks saw adversaries use stolen deployment keys to create fraudulent bridge deployments that drained user funds before detection.
- Centralized Validator/Custodian Risks: Bridges often depend on a small set of validators or custodians – sometimes as few as three entities – creating single points of failure. If these validators are compromised (via collusion or attack), they can approve fraudulent transactions across chains without resistance.
- Smart Contract Logic Flaws: Given their code complexity, cross-chain contracts are prone to bugs such as improper message validation or replay attack vectors. Balancer’s $128 million exploit was rooted in such logic flaws within smart contracts managing pooled assets across chains.
- Insecure Cross-Chain Messaging Protocols: Weaknesses in how messages are verified between blockchains can allow forged transactions and asset theft. Without robust cryptographic guarantees, adversaries can inject fake messages that trigger unauthorized transfers.
- Oracle Manipulation Attacks: Many bridges rely on external oracles for price feeds or state confirmation. Delays, inaccuracies, or outright manipulation of these data sources enable attackers to trigger fraudulent liquidations or transfers at opportune moments.
- Lack of Timely Upgrades and Patch Management: Even when vulnerabilities are discovered, slow response times and delayed patching leave bridges exposed far longer than necessary. Attackers actively monitor open-source repositories and audit reports for laggards slow to address known issues.
Pervasive Multi-Sig Compromises and Stolen Key Incidents
The two most common entry points for high-profile bridge attacks this year have been compromised multi-signature wallets and stolen deployment keys. In both scenarios, human error remains a significant factor: phishing emails targeting validator operators, poorly secured hot wallets containing deployment credentials, or simple lapses in operational security have all contributed directly to major breaches.
The lesson? No amount of cryptographic sophistication can compensate for weak key management practices at the human layer. As more value flows through bridges connecting major L1s like Ethereum and Solana with emerging L2s and appchains, the stakes only grow higher.
The Centralization Dilemma: Validators and Custodial Risks
A recurring theme in recent incidents is excessive reliance on centralized custodians or validators within bridge protocols. While decentralizing validator sets can introduce coordination challenges and increase costs, it is clear that minimal validator diversity creates honeypots irresistible to attackers – especially when combined with lackluster monitoring tools or slow incident response times.
This centralization dilemma sits at the heart of ongoing debates about optimal bridge design; projects must balance user experience against security tradeoffs while recognizing that every shortcut introduces new attack surfaces.
Another persistent risk factor is the prevalence of smart contract logic flaws and insecure cross-chain messaging protocols. The complexity of coordinating state and value across multiple blockchains means that even minor bugs in validation logic or message parsing can have devastating consequences. In 2025, attackers have repeatedly exploited these flaws to bypass intended controls, replay messages, or forge transactions, often with little resistance from underdeveloped monitoring systems.
For example, Balancer’s $128 million exploit was ultimately traced to a subtle vulnerability in smart contract code governing pooled asset transfers. Similarly, several recent hacks leveraged weaknesses in cross-chain messaging protocols where insufficient cryptographic guarantees allowed adversaries to inject fraudulent messages. These incidents underscore the importance of rigorous code audits and ongoing threat modeling specifically tailored to the unique demands of cross-chain interoperability.
Oracle Manipulation and the Patch Management Problem
The reliance on external oracles for price feeds or state confirmations introduces yet another vector for exploitation. Attackers have demonstrated that by manipulating oracle inputs, whether through latency attacks, flash loan-driven price swings, or collusion with compromised data providers, they can trigger false liquidations or unauthorized asset movements across bridges. Oracle manipulation remains a subtle but potent threat, especially as bridges increasingly support complex DeFi primitives like lending and derivatives.
Equally alarming is the sector’s ongoing struggle with timely upgrades and patch management. In a fast-moving environment where vulnerabilities are often disclosed publicly (sometimes before fixes are available), even brief windows between discovery and remediation can be catastrophic. Attackers actively monitor open-source repositories and audit disclosures for signs of lagging patch adoption, a fact that has fueled several high-profile exploits this year.
Building Resilience: Security Best Practices for 2025
If there is a silver lining to 2025’s relentless barrage of bridge hacks, it is the growing consensus around best practices for mitigating these risks. Security experts recommend several concrete steps:
- Decentralize validator sets: Increase diversity among validators to minimize single points of failure and reduce susceptibility to coordinated attacks or insider threats.
- Enforce robust key management: Use hardware security modules (HSMs), multi-factor authentication, and stringent operational security procedures for all key custodians.
- Pursue continuous auditing: Treat audits as an ongoing process rather than a one-off event; employ both internal reviews and reputable third-party auditors specializing in cross-chain protocols.
- Implement real-time anomaly detection: Deploy active monitoring systems capable of flagging suspicious activity before large-scale losses occur.
- Migrate toward advanced bridge models: Consider architectures leveraging light clients or zero-knowledge proofs to reduce trust assumptions around validators and key holders.
The imperative for robust risk management extends beyond technical fixes. As institutional capital continues pouring into DeFi, and regulators sharpen their focus on systemic vulnerabilities, the industry must prioritize transparency, rapid incident response, and user education alongside technical innovation. For those building or relying on cross-chain infrastructure, complacency is no longer an option.
The events of this year have made it clear: as long as bridges remain vital arteries connecting fragmented blockchain ecosystems, and as long as they control access to billions in pooled assets, they will remain at the forefront of crypto’s security battles. Proactive defense strategies rooted in decentralization, continuous monitoring, and agile patching are essential if DeFi is to realize its vision without succumbing to its own weakest links.






