
Cross-chain bridges have emerged as the linchpin of blockchain interoperability, enabling seamless movement of assets and data between disparate blockchains. Yet, this very function has made them the biggest target in DeFi security. In the past two years alone, bridge exploits have accounted for nearly half of all DeFi hacks, with losses exceeding $2.5 billion. Understanding why these protocols are so vulnerable requires a close look at the anatomy of recent attacks and the specific weaknesses that have repeatedly been exploited by sophisticated adversaries.

Why Cross-Chain Bridges Are Prime Targets
The sheer volume of funds locked in cross-chain bridges makes them irresistible to attackers. But it’s not just about the money – it’s about complexity and trust models that are difficult to secure. Unlike single-chain DeFi protocols, bridges must maintain security guarantees across multiple networks, using mechanisms like validators, relayers, oracles, and smart contracts that interact with external systems. Each layer introduces new risks.
Let’s break down the seven most critical vulnerabilities that have fueled high-profile bridge hacks as of 2025:
7 Critical Cross-Chain Bridge Vulnerabilities
-

Compromised Validator or Relayer Keys: Attackers who gain access to validator or relayer private keys can mint or release bridged assets without authorization. This was the case in the infamous Ronin Bridge hack, which resulted in a $600 million loss.
-
Smart Contract Logic Flaws: Vulnerabilities in bridge contract code—like unchecked external calls or improper validation—can let attackers bypass security checks and drain funds. The Wormhole bridge suffered a $300 million loss due to such a flaw.
-

Insufficient Multi-Signature Thresholds: Bridges that rely on low multi-signature requirements are vulnerable to collusion or partial key compromise, enabling unauthorized asset transfers.
-
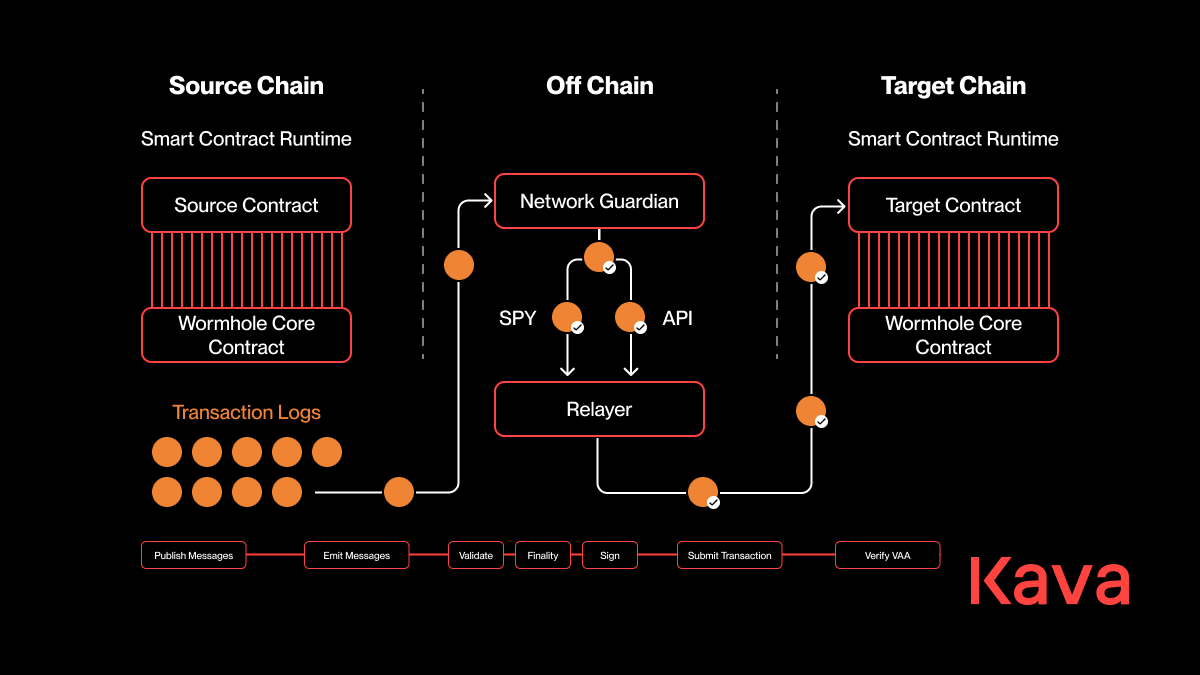
Insecure Cross-Chain Messaging Protocols: Weaknesses in message verification or replay protection allow attackers to forge messages and manipulate asset flows between blockchains.
-
Oracle Manipulation Attacks: Exploiting insecure or overly centralized price feeds (oracles) can lead to incorrect asset valuations and fraudulent transactions across bridges.
-

Lack of Timely Upgrades and Patch Management: Delays in addressing known vulnerabilities or applying critical patches leave bridges exposed to exploits targeting outdated code.
-
Poor Operational Security (OpSec) for Admin Functions: Inadequate protection of admin interfaces, upgrade mechanisms, or emergency controls can result in privilege escalation and full bridge takeover.
about the seven key vulnerabilities affecting cross-chain bridges as described below.
The Seven Most Critical Cross-Chain Bridge Vulnerabilities
- Compromised Validator or Relayer Keys: Many bridges rely on a set of validators or relayers to sign off on asset transfers between chains. If attackers compromise even a subset of these private keys – whether through phishing, malware, or insider threats – they can authorize unauthorized minting or release of assets. The Ronin Bridge hack ($600 million) is a textbook example: attackers gained control over five out of nine validator keys and drained vast sums from the protocol.
- Smart Contract Logic Flaws: Bridges are powered by complex smart contracts that handle asset locking, minting, and burning across chains. Even small logic errors – such as unchecked external calls or improper input validation – can be catastrophic. The Wormhole exploit ($300 million) was traced to such a flaw in message verification logic that allowed an attacker to mint wrapped ETH without providing collateral.
- Insufficient Multi-Signature Thresholds: Security often depends on requiring multiple parties to approve transactions (multi-sig). However, if the threshold is set too low (e. g. , 2-of-5), attackers need only compromise a few keys to gain control. Collusion among validators or partial key leaks can thus lead directly to unauthorized asset transfers.
- Insecure Cross-Chain Messaging Protocols: At their core, bridges depend on reliable messaging between chains. Weaknesses in message verification or lack of replay protection can allow attackers to forge messages or replay old ones, manipulating asset flows undetected until it’s too late.
- Oracle Manipulation Attacks: Some bridges use price feeds or other external data sources (oracles) for operations like collateral valuation during bridging. If these feeds are insecure or overly centralized, attackers can manipulate prices and trigger fraudulent transactions across chains.
- Lack of Timely Upgrades and Patch Management: The rapid pace of DeFi innovation means new vulnerabilities surface regularly. When bridge operators delay patching known issues or fail to upgrade outdated codebases promptly, they leave themselves exposed to exploits targeting already-documented flaws.
- Poor Operational Security (OpSec) for Admin Functions: Beyond code-level risks lie human factors: weak protection around admin interfaces, upgrade mechanisms, or emergency controls can enable privilege escalation attacks and full bridge takeovers if exploited by determined adversaries.
Anatomy of Recent Billion-Dollar Bridge Exploits
The impact of these vulnerabilities is not theoretical – it’s visible in every major headline-grabbing hack from the past two years. For example:
- The Ronin Network breach saw compromised validator keys result in $600 million in losses due to insufficient decentralization and poor OpSec.
- The Wormhole exploit stemmed from a smart contract bug that bypassed critical checks during cross-chain message verification.
- Lesser-known incidents continue to highlight how multi-sig misconfigurations and delayed patching expose even well-audited bridges.
If you’re interested in deeper technical case studies on these attack vectors and how modern mitigations are evolving, see our extended analysis at Why Cross-Chain Bridges Get Hacked: Common Attack Vectors and How To Mitigate Them.
Navigating Bridge Security: What Users Need To Know
No matter how robust an individual chain may be, its assets become vulnerable once they traverse an insecure bridge. This reality underscores why due diligence is non-negotiable for anyone using cross-chain protocols today. In upcoming sections we’ll explore practical steps users can take – from limiting token approvals and using smaller transactions to choosing audited bridges and staying informed about emerging threats – but first let’s examine why certain design patterns keep recurring as points of failure across the industry.
Recurring vulnerabilities in cross-chain bridges are not simply the result of isolated coding errors or unlucky breaches. Instead, they reflect structural weaknesses rooted in how these protocols are architected and operated. Each of the seven critical vulnerabilities outlined above has been directly implicated in multi-million dollar exploits, with attackers consistently seeking out the same classes of weakness across different projects.
Why These Vulnerabilities Persist
Several factors contribute to the persistence and recurrence of these bridge vulnerabilities:
- Complexity: Cross-chain bridges must synchronize states and assets between blockchains with differing consensus models, creating a vast attack surface that is hard to fully secure.
- Centralization Pressure: To achieve speed and usability, many bridges sacrifice decentralization, relying on small validator sets or centralized relayers. This makes compromised validator or relayer keys a perennial risk.
- Pace of Innovation: The rapid development cycles in DeFi often lead to shortcuts in security processes, such as insufficient multi-signature thresholds or delayed upgrades, leaving systems exposed to known threats.
- Human Factors: Poor operational security (OpSec), particularly around admin functions and emergency controls, continues to be a low-hanging fruit for attackers seeking privilege escalation opportunities.
Seven Key Cross-Chain Bridge Vulnerabilities: Exploits & Losses (2025)
| Vulnerability | Description | Real-World Exploit Example | Estimated Loss |
|---|---|---|---|
| Compromised Validator or Relayer Keys | Attackers gain control of validator or relayer private keys, enabling unauthorized minting or release of bridged assets. | Ronin Bridge hack (2022): Attackers compromised validator keys. | $600 million |
| Smart Contract Logic Flaws | Bugs in bridge contract code, such as unchecked calls or improper validation, allow attackers to bypass security and drain funds. | Wormhole Bridge hack (2022): Exploited a smart contract bug. | $300 million |
| Insufficient Multi-Signature Thresholds | Low multi-signature requirements make bridges vulnerable to collusion or partial key compromise. | Poly Network hack (2021): Exploited insufficient multisig controls. | $611 million |
| Insecure Cross-Chain Messaging Protocols | Weaknesses in message verification or replay protection allow forged messages and asset manipulation. | Nomad Bridge hack (2022): Attackers exploited message verification flaws. | $190 million |
| Oracle Manipulation Attacks | Insecure or centralized price feeds/oracles can be exploited for fraudulent transactions and incorrect asset valuations. | Qubit Finance Bridge hack (2022): Exploited oracle vulnerabilities. | $80 million |
| Lack of Timely Upgrades and Patch Management | Delays in fixing known vulnerabilities or applying patches leave bridges open to exploits targeting outdated code. | Multichain Bridge hack (2023): Exploited unpatched vulnerabilities. | $126 million |
| Poor Operational Security (OpSec) for Admin Functions | Weak protection of admin interfaces or emergency controls can lead to privilege escalation and bridge takeover. | Horizon Bridge hack (2022): Attackers gained admin access through poor OpSec. | $100 million |
Mitigating Your Exposure: Best Practices for Bridge Users
If you interact with cross-chain bridges, whether as a DeFi user, developer, or protocol operator, adopting rigorous security practices is essential. Here are practical steps mapped directly to each vulnerability:
- Compromised Validator/Relayer Keys: Favor bridges with decentralized validator sets and robust key management policies. Look for transparency around validator onboarding and offboarding processes.
- Smart Contract Logic Flaws: Only use bridges that have undergone thorough audits by reputable firms. Monitor for bug bounty programs and public code reviews.
- Insufficient Multi-Signature Thresholds: Check whether the bridge uses high-threshold multi-sig schemes (e. g. , 4-of-5 or higher) for critical operations. Avoid protocols with lax signature requirements.
- Insecure Cross-Chain Messaging Protocols: Ensure that message verification includes replay protection and cryptographic proofs. Prefer solutions that publish detailed documentation on their messaging infrastructure.
- Oracle Manipulation Attacks: Assess the decentralization and resilience of any oracle services used by the bridge. Multi-source oracles reduce single points of failure.
- Lack of Timely Upgrades/Patch Management: Stay up to date on protocol announcements regarding upgrades or incidents. Avoid using bridges that lag behind on patching known issues.
- Poor OpSec for Admin Functions: Seek out teams with strong track records in operational security, including regular penetration testing, restricted admin access, and clearly defined emergency procedures.
If you want a more granular risk assessment framework tailored for developers evaluating bridge protocols, visit our guide on How To Evaluate Cross-Chain Bridge Security: A Practical Risk Assessment Framework for Developers.
The Road Ahead: Toward Safer Blockchain Interoperability
The future of blockchain interoperability depends on learning from hard-won lessons. Bridges will remain attractive targets as long as they concentrate value and complexity without matching investments in layered defense. Encouragingly, recent months have seen leading projects adopt distributed verification models, increase multi-signature thresholds, roll out time-locks on large transfers, and implement real-time monitoring tools, steps that meaningfully raise the bar for attackers.
The community’s vigilance is equally important. By demanding greater transparency from bridge operators, and refusing to compromise on audits or OpSec standards, users can help drive industry-wide improvements that make catastrophic exploits less likely over time. For those who wish to dive deeper into specific attack vectors or preventative strategies tailored to evolving threats, our resource library remains continuously updated with technical breakdowns and actionable advice.






