As blockchain ecosystems race toward greater interoperability, the promise of seamless asset transfers and cross-chain communication is transforming DeFi. However, this multi-chain expansion comes at a price: the attack surface grows with every new integration, amplifying the security risks that cross-chain messaging protocols must manage. In this article, we’ll explore why multi-chain growth is a double-edged sword, unpacking the most critical vulnerabilities and what they mean for users and protocol developers alike.

Why Multi-Chain Expansion Increases Security Complexity
At its core, cross-chain messaging is about enabling different blockchains to communicate and transfer value. But each new chain added to a protocol’s roster introduces unique consensus mechanisms, transaction finality times, and data structures. This diversity complicates security in several ways:
- Broader attack surface: More chains mean more potential entry points for attackers to exploit.
- Inconsistent standards: Varying security practices and transaction models can lead to unforeseen vulnerabilities.
- Operational complexity: Monitoring, updating, and patching across multiple chains requires significant resources and expertise.
Recent research from Chainlink and the National Institutes of Health underscores that cross-chain bridges are now among the most targeted components in DeFi, with vulnerabilities ranging from smart contract bugs to inconsistent cross-chain standards. Learn more about these challenges here.
The Seven Most Critical Cross-Chain Messaging Vulnerabilities
7 Key Cross-Chain Bridge Vulnerabilities
-
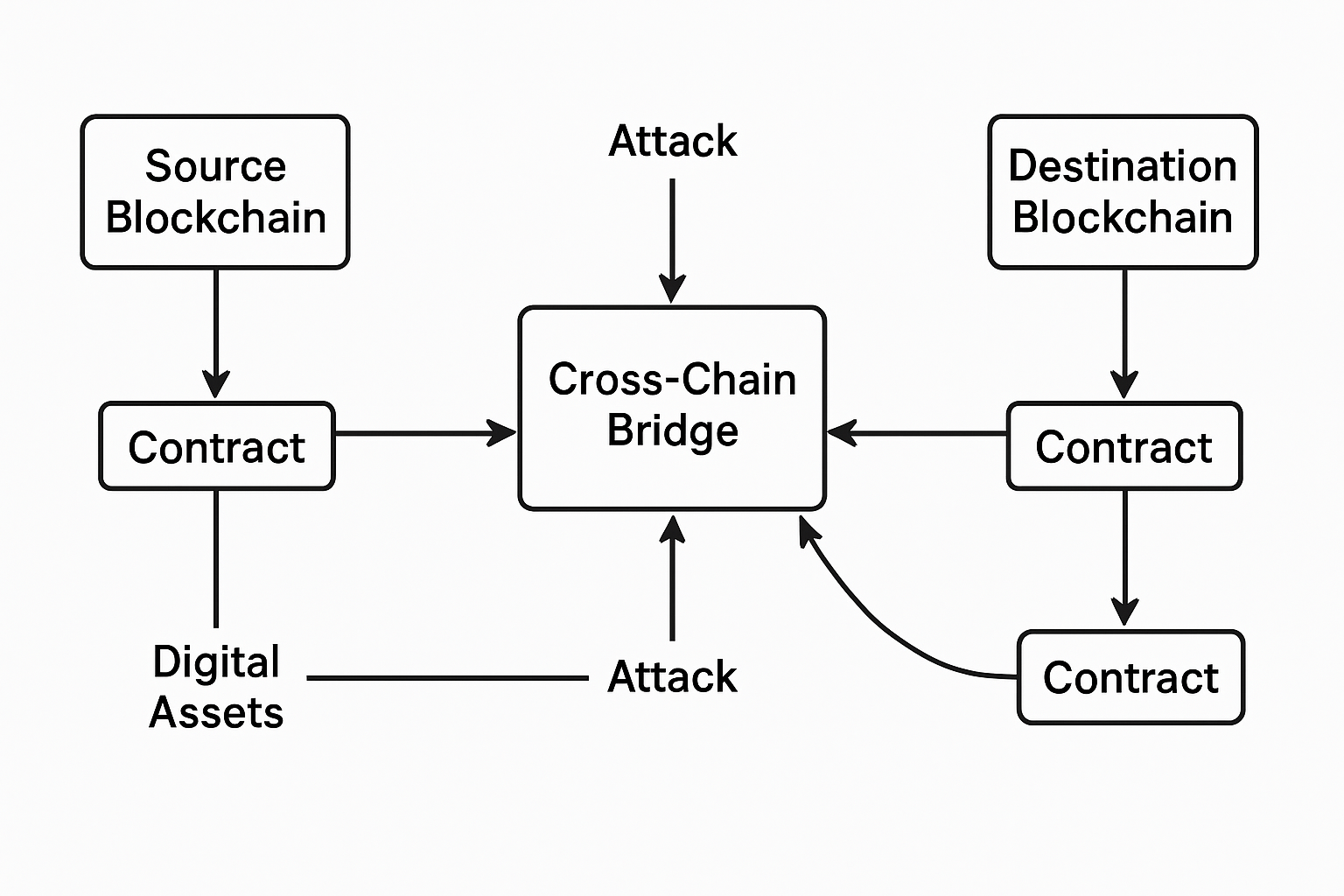
Increased Attack Surface: Integrating multiple blockchains creates more entry points for attackers, as each chain introduces unique security challenges and potential vulnerabilities.
-
Smart Contract Vulnerabilities: Complex smart contracts power most bridges, but coding flaws can enable exploits—such as the Wormhole bridge hack that led to a $325 million loss.
-

Centralization Risks: Many bridges rely on a small group of validators or multi-signature wallets. If these are compromised, attackers can steal massive sums, as seen in the $600 million Ronin Bridge hack.
-
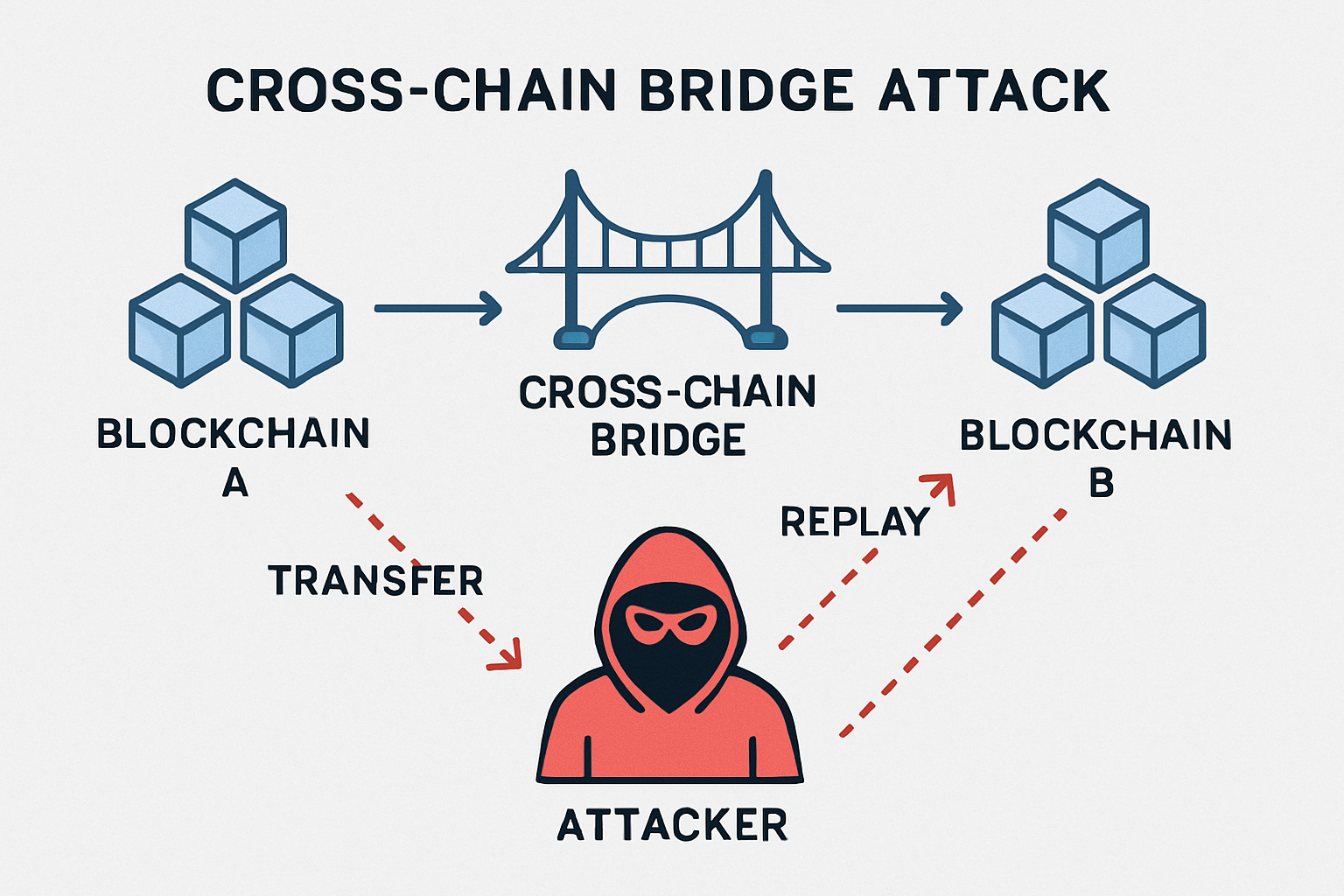
Replay Attacks: Transactions signed on one chain can be maliciously reused on another if signatures lack chain-specific identifiers, leading to unauthorized actions.
-
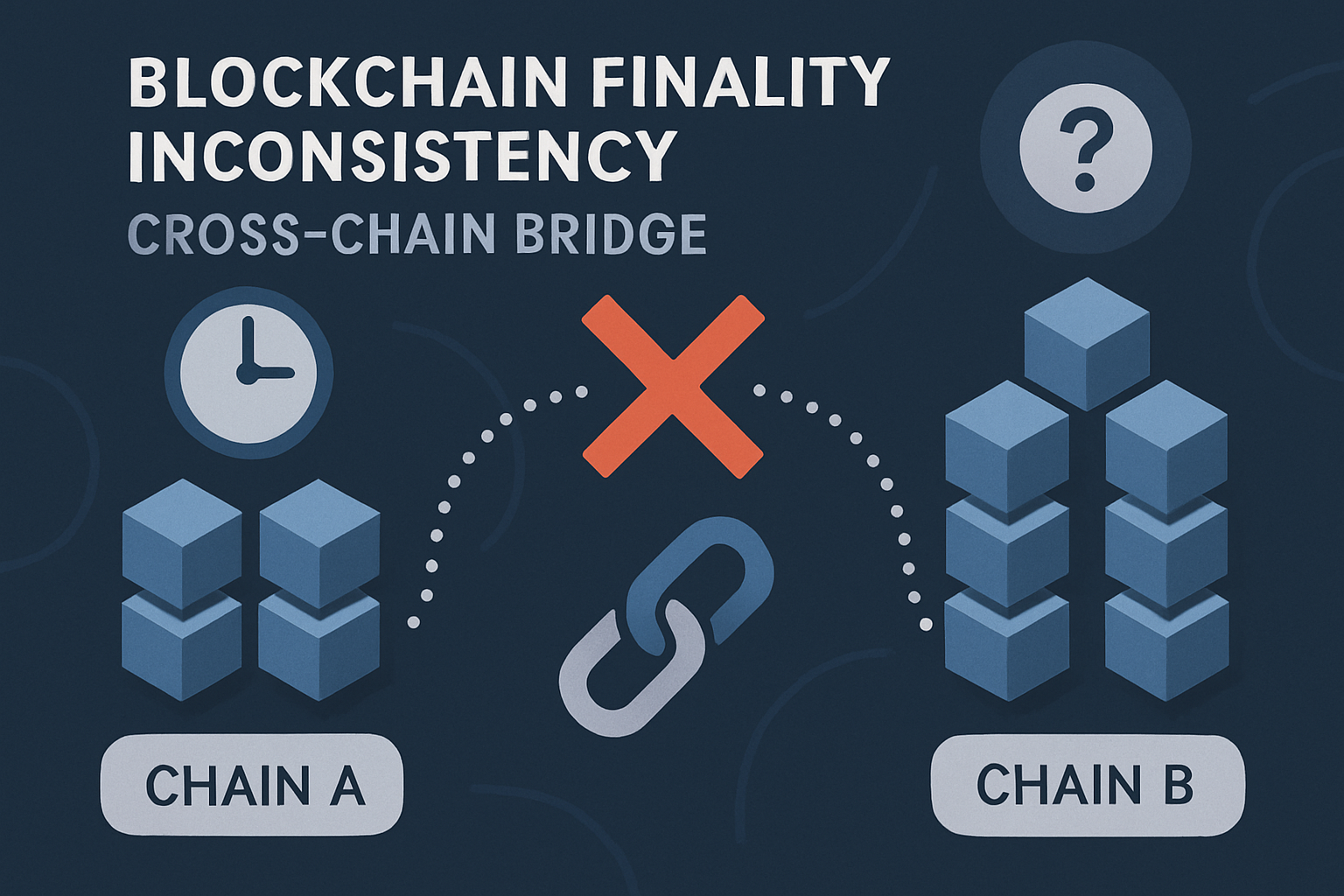
Inconsistent State and Settlement Finality: Different blockchains finalize transactions at varying speeds, creating windows for double-spend attacks and state mismatches during cross-chain operations.
-
Liquidity Fragmentation: Multi-chain ecosystems scatter liquidity across networks, increasing the risk of user errors, phishing, and transaction misrouting.
-
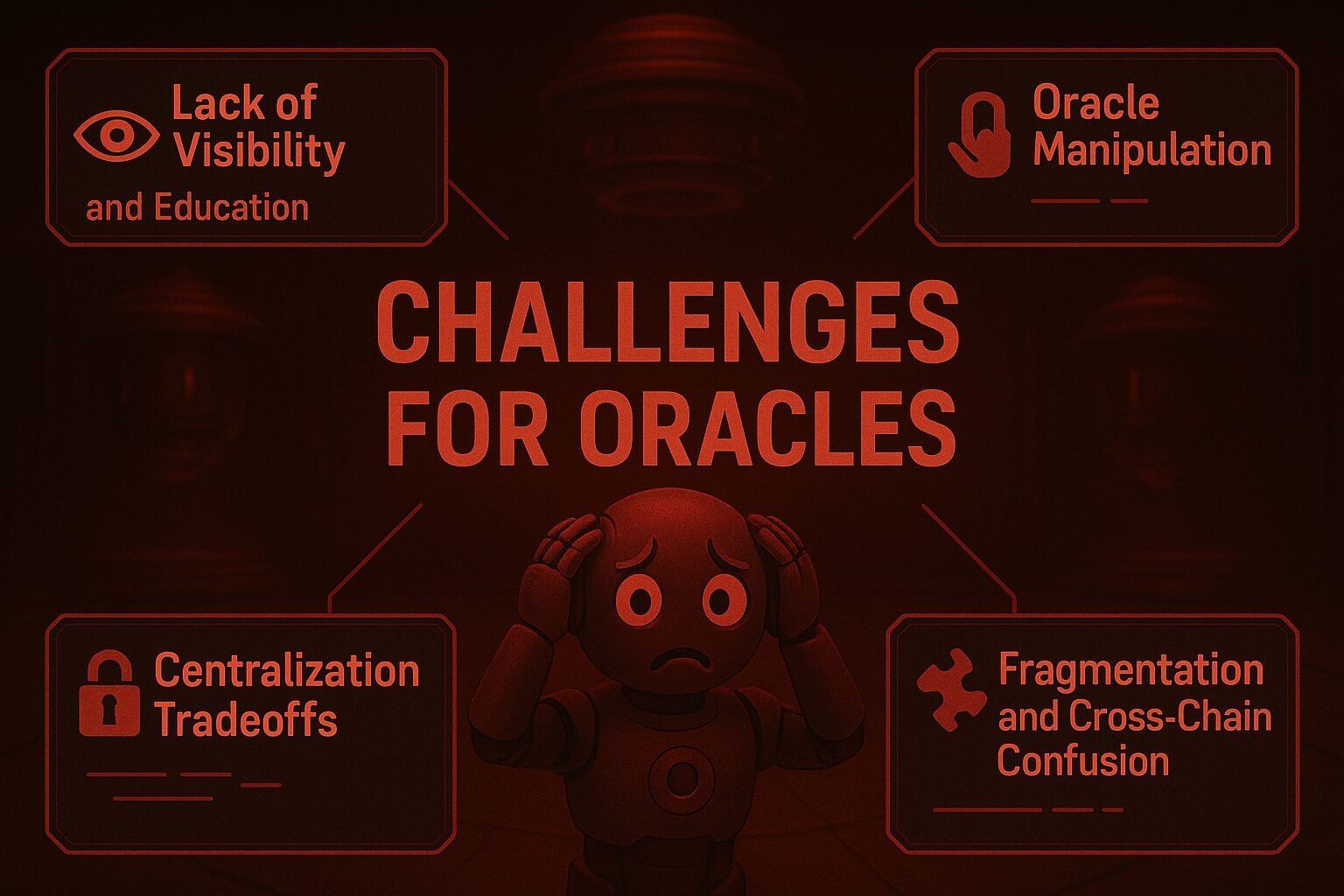
Oracle Manipulation: Bridges often depend on oracles for external data. If oracles are compromised or manipulated, attackers can trigger fraudulent cross-chain transfers or asset swaps.
Let’s break down the top vulnerabilities currently plaguing multi-chain protocols:
- Smart Contract Flaws: Complex logic in bridge contracts can be exploited, as seen in the Wormhole bridge hack that resulted in a $325 million loss due to unauthorized minting.
- Centralization Risks: Many bridges rely on a small group of validators. If compromised, like in the Ronin Bridge incident ($600 million lost), attackers gain control over cross-chain transfers.
- Replay Attacks: Transactions signed on one chain can be maliciously replayed on another if signatures lack chain-specific identifiers.
- Inconsistent Settlement Finality: Varying confirmation times across blockchains can lead to double-spending or state mismatches during asset transfers.
- Liquidity Fragmentation: Multi-chain environments often scatter liquidity, increasing user error rates and susceptibility to phishing or misrouted transactions.
- Oracle Manipulation: Oracles providing off-chain data can be attacked or manipulated, leading to incorrect asset valuations or transfers.
- Standardization Gaps: Lack of unified protocols makes it difficult to audit and secure bridges consistently across chains.
“The safety of your assets is only as strong as the weakest link in your cross-chain infrastructure. “
Real-World Examples: What Happens When Security Fails?
The theory isn’t just academic, real-world bridge exploits have resulted in some of the largest losses in DeFi history. The Wormhole and Ronin hacks are only the tip of the iceberg, with attackers leveraging everything from smart contract bugs to validator collusion. These incidents underscore why multi-chain security must be proactive, not reactive.
For example, inconsistent state finality between Ethereum (15-minute block finalization) and faster chains can allow attackers to manipulate transaction order or double-spend tokens before a transfer is finalized. Similarly, replay attacks become possible when wallets don’t enforce chain-specific identifiers, allowing malicious actors to reuse signatures across domains.
In the next section, we’ll dive deeper into proven mitigation strategies and what the future holds for secure cross-chain messaging protocols.
Mitigation Strategies: Building Resilience in a Multi-Chain World
Given the high-profile failures and persistent vulnerabilities, robust security measures are no longer optional for cross-chain messaging protocols. The following strategies are critical for any project aiming to survive, and thrive, in an environment where attackers constantly seek weak points:
Essential Cross-Chain Security Mitigation Checklist
-
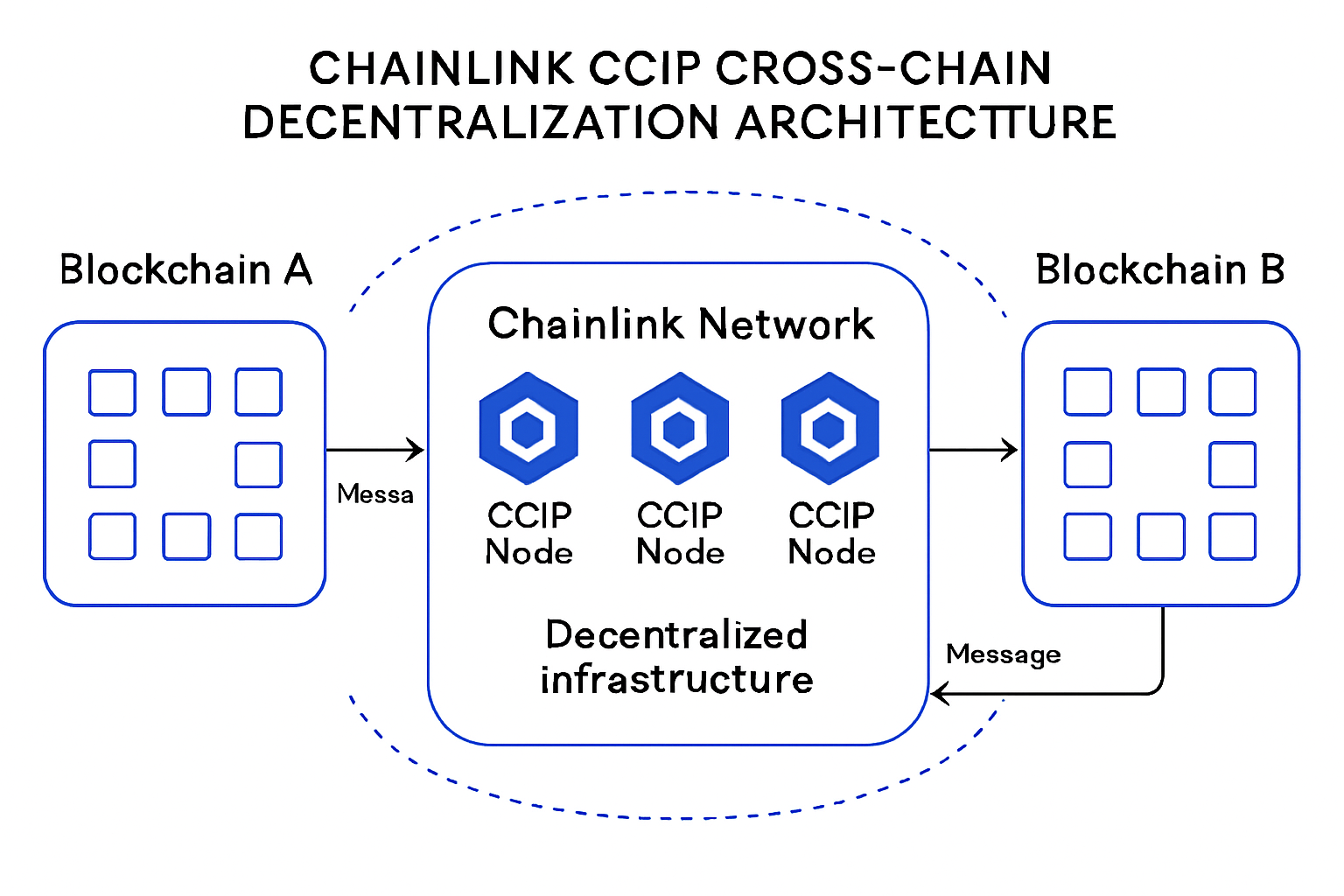
Prioritize Decentralized Validator Sets: Use decentralized infrastructures like Chainlink CCIP or Axelar to eliminate single points of failure and reduce the risk of coordinated attacks.
-
Implement Formal Verification for Smart Contracts: Use tools like ConsenSys Diligence and CertiK to mathematically verify cross-chain smart contracts and eliminate critical vulnerabilities before deployment.
-

Standardize Cross-Chain Communication Protocols: Support and integrate with standards such as IBC (Inter-Blockchain Communication) to ensure interoperability and consistent security practices across chains.
-

Enforce Chain-Specific Transaction Signatures: Require wallets and protocols to include chain identifiers in signatures, preventing replay attacks across different blockchains. Solutions like EIP-155 are industry standards for this purpose.
-

Monitor and Manage Settlement Finality: Integrate tools that account for varying finality times across chains, such as Blocknative for Ethereum, to prevent double-spend and state inconsistency attacks.
-
Participate in Bug Bounty Programs: Engage with established platforms like Immunefi to incentivize security researchers to discover and report vulnerabilities before they can be exploited.
Decentralized infrastructure is a foundational step. By distributing trust across many nodes or validators, projects can reduce the catastrophic risk of a single point of failure, something the Ronin Bridge exploit made painfully clear. Decentralization also increases the cost and complexity for would-be attackers, making exploits less feasible.
Formal verification of smart contracts is another powerful tool. This process uses mathematical proofs to ensure code behaves as intended, catching bugs before they can be exploited in the wild. While resource-intensive, formal verification is increasingly seen as essential for protocols handling large volumes of value.
Standardization and interoperability are equally important. When bridges and messaging systems follow open standards, it becomes easier to audit code, identify vulnerabilities, and share security improvements across projects. As the ecosystem matures, expect to see more industry-driven efforts to create and enforce these standards.
The Future of Cross-Chain Security
Multi-chain expansion is here to stay. As DeFi and blockchain infrastructure become more interconnected, security teams will need to stay agile, constantly updating their defenses as new attack vectors emerge. The next generation of cross-chain protocols will likely feature:
- Automated risk scanners that monitor bridges in real-time for suspicious activity or configuration drift.
- Incentivized bug bounties that reward white-hat hackers for finding flaws before criminals do.
- Greater transparency around audits and incident disclosures to build user trust.
Community vigilance is also vital. Users should demand transparency from bridge operators and only interact with protocols that openly publish audit results and incident reports. As always, “not your keys, not your coins” applies doubly in a multi-chain context, users must understand the risks before bridging assets across networks.
If you’re a developer or protocol designer, now’s the time to invest in advanced security tooling and participate in cross-ecosystem standardization efforts. If you’re a user or investor, pay close attention to which bridges have survived real-world attacks, and which are most transparent about their security posture.
The bottom line? Multi-chain growth will continue amplifying both opportunity and risk. But with thoughtful design, open collaboration, and relentless focus on security fundamentals, it’s possible to build cross-chain messaging protocols that are as resilient as they are innovative.
If you want a deeper dive on specific vulnerabilities or mitigation techniques for your project, check out our dedicated resources at this page.







