
As cross-chain bridges become the backbone of blockchain interoperability, their security is under relentless scrutiny. The surge in cross-chain bridge hacks throughout 2022 and 2023 has underscored the urgent need for a rigorous, data-driven approach to risk assessment. Developers, security engineers, and DeFi architects must move beyond superficial audits and adopt a practical framework that systematically addresses each layer of risk.
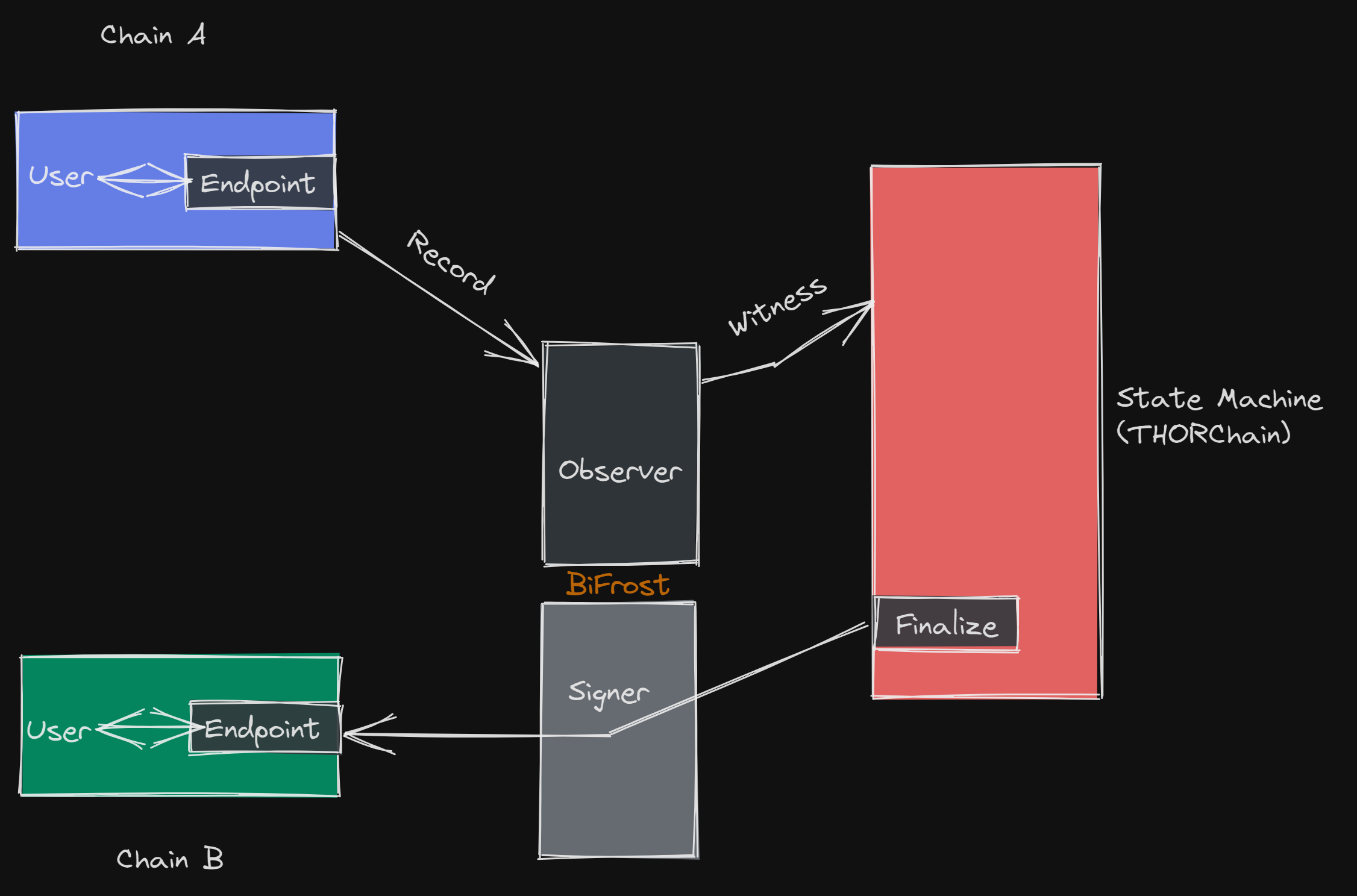
Dissecting Bridge Architecture: Where Do Vulnerabilities Hide?
Recent research (SoK: Cross-Chain Bridging Architectural Design Flaws, ScienceDirect) identifies 13 key architectural components in cross-chain bridges, each with its own potential for design flaws. These components range from smart contract logic and validator design to message-passing schemes and user authentication layers. The most exploited vulnerabilities, as cataloged by arXiv and the ACM Digital Library, cluster around:
- Validator centralization: Single points of failure remain a critical risk vector.
- Poor access control: Insufficient permissioning allows unauthorized actions.
- Message-passing flaws: Unverified or replayed messages can trigger unauthorized transfers.
- Inadequate monitoring: Delayed detection of exploits leads to amplified losses.
Developers must analyze each component through the lens of historical exploits and systemic risk. For a deeper dive into why cross-chain bridges remain DeFi’s biggest attack surface, see our detailed case study.
Core Elements of a Practical Cross-Chain Bridge Risk Assessment
A robust risk assessment framework is not just a checklist, it’s a living process that adapts to evolving threats. Here are the foundational elements every developer should integrate:
8 Essential Components of Cross-Chain Bridge Risk Assessment
-

Comprehensive Code Audits: Rigorous manual and automated reviews of the bridge’s codebase to uncover vulnerabilities, logic flaws, and ensure best practice adherence. Engaging trusted third-party auditors is key for unbiased evaluation.
-
Decentralized Validator Design: Utilizing multiple independent validators (e.g., via Proof of Stake or Delegated Proof of Stake) to prevent single points of failure and reduce the risk of centralization attacks.
-

Robust Access Control Mechanisms: Implementing strict permissioning to ensure only authorized entities can execute critical bridge operations, minimizing unauthorized access risks.
-

Regular Security Testing and Monitoring: Continuous vulnerability assessments, penetration tests, and real-time monitoring to promptly detect and respond to threats or suspicious activities.
-

Implementation of Rate Limits: Setting transfer rate caps to limit the value that can be bridged within a set timeframe, reducing the potential impact of exploits.
-

Utilization of Established Protocols: Leveraging well-tested, widely adopted protocols with strong uptime and security records to enhance bridge reliability and trust.
-

Incorporation of Multi-Signature Schemes: Requiring multiple validator approvals for cross-chain operations, which significantly increases resistance to validator compromise.
-

Adoption of a Cross-Chain Risk Framework: Applying comprehensive frameworks (such as the Crosschain Risk Framework) for systematic identification, assessment, and mitigation of cross-chain bridge risks.
Comprehensive Code Audits: Manual and automated code reviews remain the gold standard. Engage reputable third-party auditors and require public disclosure of findings. Audits should focus on both smart contract logic and off-chain components.
Decentralized Validator Design: Bridges that rely on a single validator or limited set of signers are inherently vulnerable. Adopt decentralized mechanisms like Proof of Stake (PoS) or Delegated Proof of Stake (DPoS) to distribute authority and reduce collusion risk.
Robust Access Control: Ensure that only authorized entities can initiate sensitive operations. Implement granular permissions and regularly review access policies for drift or privilege escalation.
Continuous Security Testing and Monitoring: Real-time threat detection is non-negotiable. Deploy monitoring tools that flag anomalies in bridge activity, and run regular penetration tests to simulate evolving attack vectors. For more on this, see our guide to real-time risk scanning for bridges.
Rate Limits, Protocol Selection, and Multi-Signature Defenses
Mitigating the blast radius of an exploit is just as important as preventing it. Setting rate limits on token transfers caps potential losses during an attack window, a tactic increasingly adopted after high-profile breaches. Selecting protocols with proven security records (such as those with years of uptime and no major incidents) can drastically reduce exposure to unknown risks.
Finally, the incorporation of multi-signature schemes ensures that no single validator can unilaterally approve cross-chain operations. This collective decision-making dramatically raises the bar for attackers seeking to compromise bridge consensus.
Comparison of Security Features and Risk Factors in Leading Cross-Chain Bridges (2025)
| Bridge Name | Comprehensive Code Audits | Decentralized Validator Design | Robust Access Control | Regular Security Testing & Monitoring | Rate Limits | Established Protocols | Multi-Signature Schemes | Adoption of Risk Framework | Notable Vulnerabilities (2022-2023) |
|---|---|---|---|---|---|---|---|---|---|
| Wormhole | ✅ Yes (3rd-party audits) | ⚠️ Partial (Guardian set, not fully decentralized) | ✅ Yes | ✅ Yes (ongoing) | ❌ No | ✅ Yes | ✅ Yes (multi-sig for upgrades) | ⚠️ Partial | Exploit in 2022 due to validator compromise |
| Axelar | ✅ Yes (audited) | ✅ Yes (DPoS with many validators) | ✅ Yes | ✅ Yes (continuous) | ✅ Yes | ✅ Yes | ✅ Yes (multi-sig for critical ops) | ✅ Yes | No major exploits reported |
| Polygon Bridge | ✅ Yes (audited) | ❌ No (centralized validators) | ✅ Yes | ✅ Yes | ❌ No | ✅ Yes | ⚠️ Partial (multi-sig for admin ops only) | ⚠️ Partial | 2022: Validator key compromise |
| Multichain | ✅ Yes (audited) | ⚠️ Partial (semi-centralized) | ✅ Yes | ✅ Yes | ✅ Yes | ✅ Yes | ✅ Yes (multi-sig withdrawals) | ⚠️ Partial | 2023: Admin key exploit |
| LayerZero | ✅ Yes (audited) | ⚠️ Partial (Ultra Light Node, not fully decentralized) | ✅ Yes | ✅ Yes | ❌ No | ✅ Yes | ❌ No | ⚠️ Partial | No major exploits reported |
| ChainBridge | ✅ Yes (audited) | ⚠️ Partial (configurable validators, often semi-centralized) | ✅ Yes | ✅ Yes | ❌ No | ✅ Yes | ✅ Yes (multi-sig supported) | ⚠️ Partial | 2022: Bridge logic bug exploited |
The sophistication of today’s attackers demands that bridge developers adopt a holistic, layered security stance. In the next section, we’ll break down how to apply these principles using real-world incident data, validator model comparisons, and actionable checklists tailored for modern DeFi teams.
Applying the Framework: Incident Analysis, Validator Models, and Actionable Steps
Leveraging historical incident data is a powerful way to stress-test your bridge’s architecture. Analyzing attack vectors from notorious exploits, such as validator key compromises, replay attacks, and message relay failures, reveals how seemingly minor oversights can cascade into systemic losses. For developers, conducting a bridge incident history analysis is not optional; it’s a critical feedback loop for strengthening controls and anticipating new threats.
Validator model selection is another pivotal decision. The landscape spans from centralized or semi-decentralized multisig schemes to fully decentralized PoS/DPoS validator sets. Each model presents distinct trade-offs between performance, cost, and security:
Validator Models for Cross-Chain Bridges: Strengths & Weaknesses
-
Federated (Multi-Signature) Validator Model: Used by bridges like Binance Bridge and Multichain. Strengths: Simple implementation, fast transaction finality.Weaknesses: Security depends on a small, fixed set of validators—if a majority collude or are compromised, funds are at risk.Ideal Use Case: Trusted environments or where speed is prioritized over decentralization.
-
Decentralized Proof-of-Stake (PoS) Validator Model: Employed by Axelar Network and Poly Network. Strengths: Broad validator participation, economic incentives for honest behavior, and resistance to single points of failure.Weaknesses: Complex governance, potential for validator collusion if stake is concentrated.Ideal Use Case: Public, permissionless bridges prioritizing decentralization and security.
-

Light Client-Based Model: Utilized by NEAR Rainbow Bridge and IBC (Inter-Blockchain Communication).Strengths: High trust-minimization, as each chain independently verifies the other’s state.Weaknesses: Resource-intensive, slower transaction processing, and higher development complexity.Ideal Use Case: High-value transfers or scenarios requiring maximum trustlessness.
-
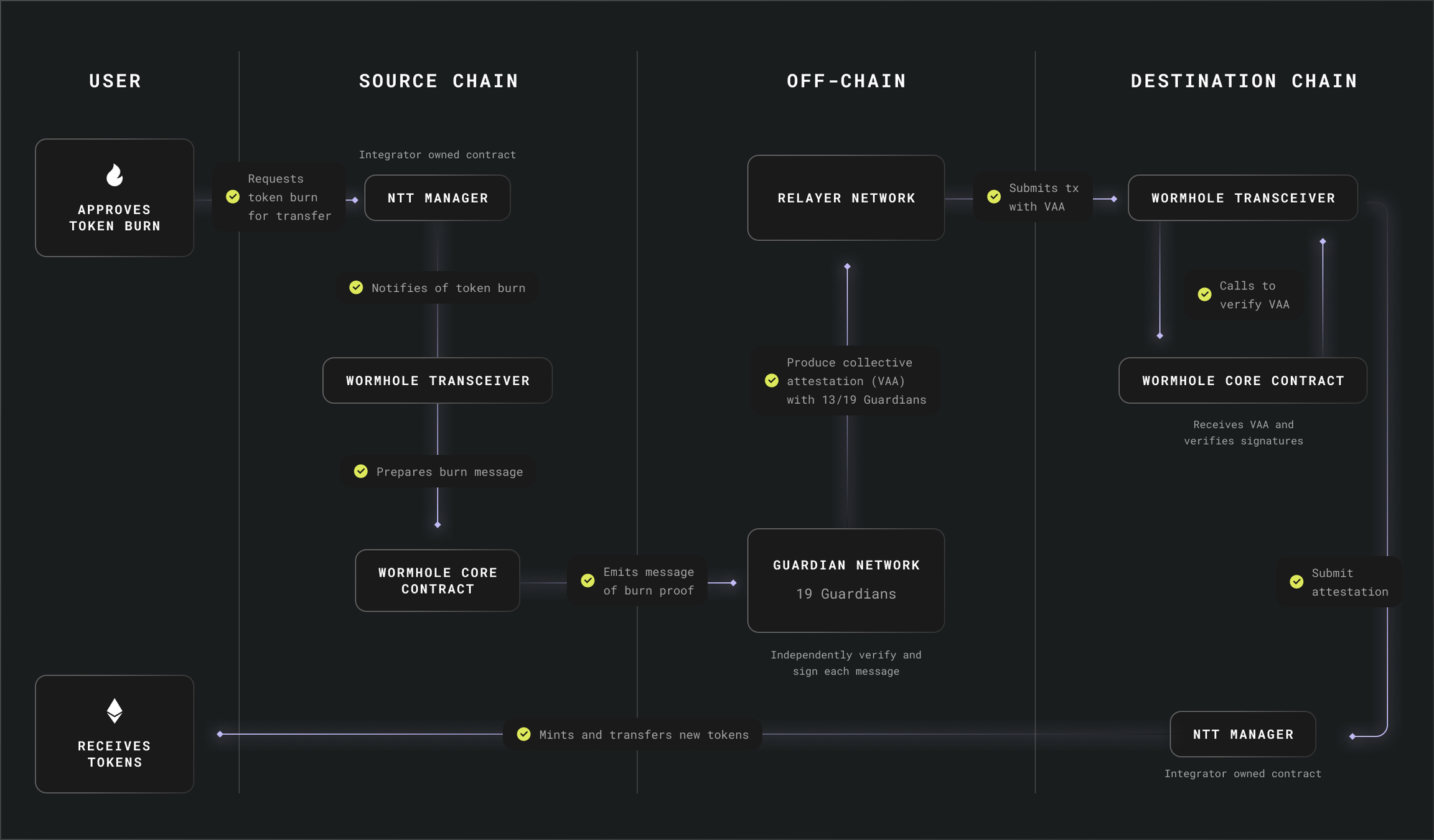
External Oracle-Based Model: Implemented by Wormhole and Chainlink CCIP.Strengths: Leverages established oracle networks for data integrity and cross-chain messaging.Weaknesses: Security depends on the oracle network’s robustness; oracles can be targeted by sophisticated attacks.Ideal Use Case: Bridges requiring real-time data feeds and interoperability across multiple blockchains.
-

Permissioned Validator Model: Seen in Celer cBridge and Allbridge.Strengths: Controlled validator set enables fast upgrades and targeted responses to threats.Weaknesses: Centralization risk and potential censorship by validator operators.Ideal Use Case: Enterprise or consortium blockchains where participants are known and trusted.
For example, while multisig models offer simplicity, they’re susceptible to collusion or key leakage, as seen in several 2023 bridge breaches. In contrast, decentralized validator networks enhance resilience but demand robust coordination and incentive alignment. Developers should rigorously evaluate their chosen model against both current best practices and the evolving threat landscape. For a technical breakdown of validator decentralization and real-time monitoring, see our research on validator security.
Bridge Message-Passing Models: Security Implications
The choice of message-passing protocol, lock-and-mint, burn-and-mint, or generic cross-chain messaging, directly impacts the bridge’s attack surface. Lock-and-mint models, while common, concentrate risk on the custody contract, making it a prime target. Generic messaging protocols (e. g. , Wormhole, Axelar) introduce additional complexity but can offer greater flexibility and modularity. However, complexity itself is a risk factor if not matched by rigorous testing and monitoring.
To minimize vulnerabilities, developers should:
Integrating Continuous Risk Scanning and Framework Adoption
Static audits provide a snapshot in time, but the threat landscape is never static. Integrating continuous risk scanning tools enables teams to catch emerging vulnerabilities before they are exploited. Platforms like Cross-Chain Messaging Risk Scanners empower teams with real-time analytics, anomaly detection, and up-to-date intelligence on cross-chain messaging vulnerabilities. For a practical how-to on integration, check out our implementation guide.
Ultimately, adopting a comprehensive blockchain bridge security framework means more than ticking boxes, it’s about establishing a culture of transparency, rapid iteration, and relentless vigilance. The most resilient projects are those that treat risk assessment as an ongoing process, not a one-off event.
As cross-chain interoperability matures, the protocols that thrive will be those that combine architectural soundness with dynamic risk management. The stakes are high, but so are the rewards for teams willing to invest in robust, data-driven security strategies. Stay proactive, benchmark against real-world exploits, and never underestimate the creativity of adversaries in the rapidly evolving world of blockchain bridges.






