Cross-chain bridges have become the arteries of decentralized finance, enabling assets to circulate freely between otherwise isolated blockchains. Yet, with over $2 billion stolen in bridge hacks according to Chainalysis, these protocols have also emerged as the single largest security risk in DeFi. Understanding why cross-chain bridges fail requires a close look at the most current and critical attack vectors, and how innovative risk scanners are helping to prevent catastrophic losses.
Seven Key Vulnerabilities Plaguing Cross-Chain Bridges
Bridge exploits are rarely the result of a single flaw. Instead, they often arise from a combination of complex vulnerabilities, each offering attackers a unique entry point. Here are the seven most critical attack vectors currently threatening cross-chain bridge security:
7 Key Vulnerabilities in Cross-Chain Bridges
-

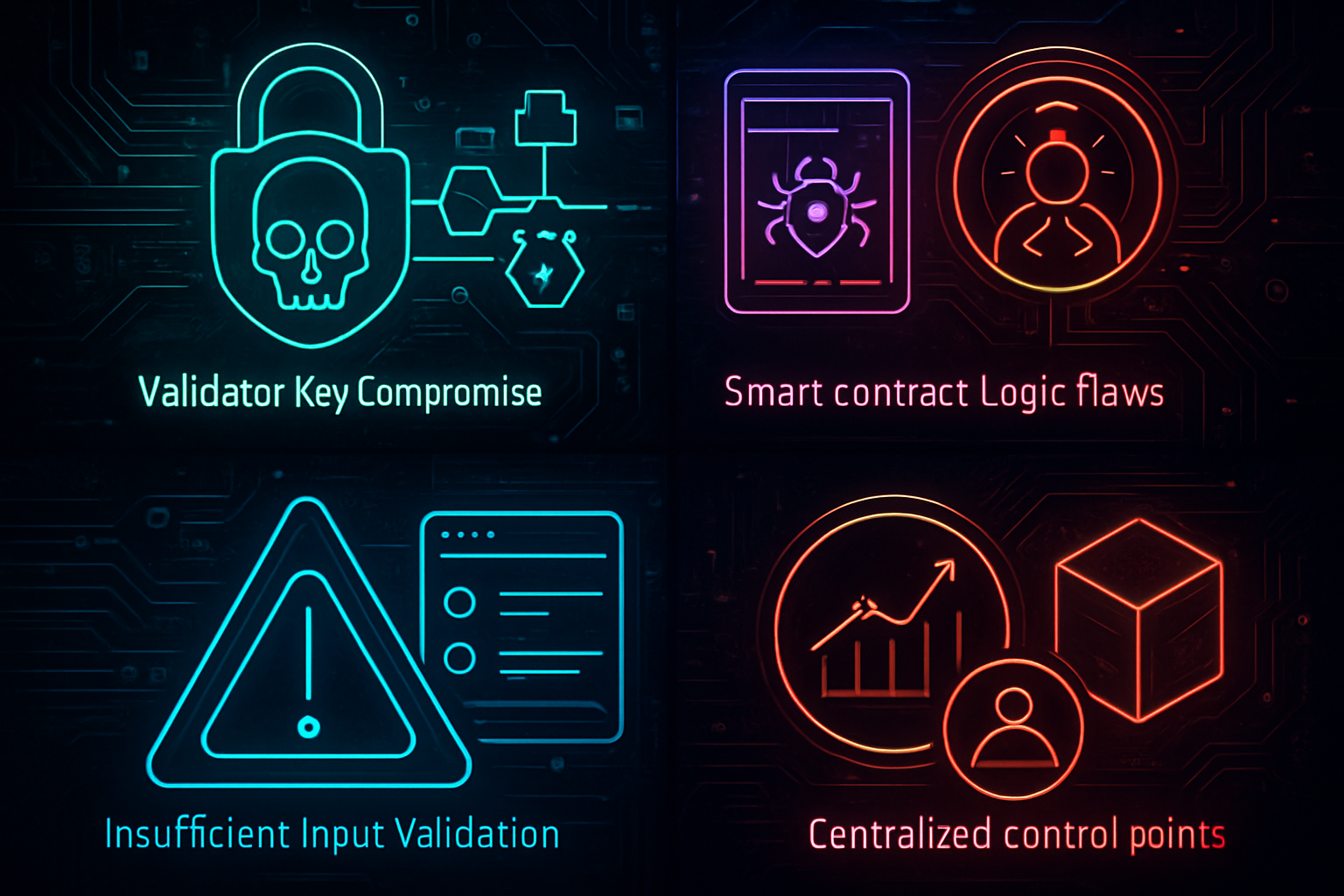
Validator Key Compromise: Attackers gain control of bridge validators, enabling unauthorized asset transfers or minting. Real-world example: The Ronin Network hack in March 2022 led to a $600 million loss after attackers compromised validator keys. The Harmony bridge also suffered a similar exploit.
-

Smart Contract Logic Flaws: Bugs in bridge contract code (such as reentrancy, unchecked external calls, or faulty access controls) allow attackers to bypass intended security checks. Example: The Nomad Bridge hack in August 2022 exploited a contract initialization bug, resulting in $190 million in losses.
-

Insufficient Input Validation: Lack of proper input sanitization on bridge interfaces or contracts enables exploits like arbitrary call injection or parameter manipulation. Example: Unsanitized input allowed attackers to exploit the Poly Network bridge in 2021, resulting in $611 million being temporarily stolen.
-

Oracle Manipulation: Attackers exploit weaknesses in price or state oracles relied upon by bridges, leading to incorrect cross-chain state updates and asset mispricing. Example: The Wormhole bridge hack in February 2022 involved manipulation of oracle data, resulting in a $320 million loss.
-

Centralized Control Points: Bridges with centralized admin keys or multisigs are vulnerable to insider threats, collusion, or key theft, resulting in potential rug pulls or unauthorized withdrawals. Example: The Multichain bridge suffered losses in 2023 after its admin keys were compromised, leading to millions in stolen assets.
-

Replay Attacks: Poorly designed message formats or signature schemes allow attackers to reuse valid messages on different chains or at different times, causing double-spending or asset theft. Example: Several bridges, including Binance Bridge, have patched vulnerabilities related to replay attacks in their cross-chain protocols.
-
Insecure Cross-Chain Message Validation: Weaknesses in how bridges validate cross-chain proofs (such as light client bugs or Merkle proof errors) can let attackers forge transactions or spoof messages. Example: The Qubit Finance bridge was exploited in January 2022 due to flawed message validation, resulting in an $80 million loss.
1. Validator Key Compromise
Many bridges rely on a set of validators to approve cross-chain transactions. If attackers manage to compromise enough validator keys, through phishing, malware, or social engineering, they can unilaterally approve fraudulent transfers or mint assets out of thin air. The Ronin Network hack, which resulted in a $600 million loss, is a stark example of this threat. The Harmony bridge suffered a similar fate, with attackers exploiting validator weaknesses for massive gains.
2. Smart Contract Logic Flaws
Smart contracts are the backbone of bridge functionality, but even minor bugs can have devastating consequences. Vulnerabilities like reentrancy, unchecked external calls, or faulty access controls allow attackers to bypass intended logic and seize control of assets. Unlike simple token contracts, bridges often involve intricate state management and message passing, making them especially prone to subtle logic errors.
3. Insufficient Input Validation
Poorly sanitized inputs on bridge interfaces or contracts can open the door to exploits such as arbitrary call injection or parameter manipulation. If an attacker can craft malicious data that the bridge fails to validate properly, they may be able to execute unauthorized actions or manipulate bridge logic at will. This vector is particularly dangerous because it can be triggered remotely and at scale.
How Attackers Exploit Bridge Weaknesses
Attackers are constantly probing bridges for weak spots. From orchestrated validator key thefts to sophisticated oracle manipulations, the methods are evolving as fast as the technology itself. Below is an overview of real-world exploit techniques mapped to the seven key vulnerabilities:
- Validator Key Compromise: Attackers use spear-phishing or malware to steal validator credentials, then coordinate fraudulent approvals.
- Smart Contract Logic Flaws: Exploiting bugs like reentrancy or logic errors to drain bridge reserves.
- Insufficient Input Validation: Sending malformed or malicious transactions that bypass security checks.
- Oracle Manipulation: Feeding false data into price or state oracles relied upon by bridges, causing mispriced or unauthorized transfers.
- Centralized Control Points: Targeting bridges with admin keys or multisig wallets that serve as single points of failure.
- Replay Attacks: Reusing valid messages on different chains or at different times to double-spend assets.
- Insecure Cross-Chain Message Validation: Exploiting flaws in proof validation (such as Merkle proof mishandling) to forge or spoof cross-chain messages.
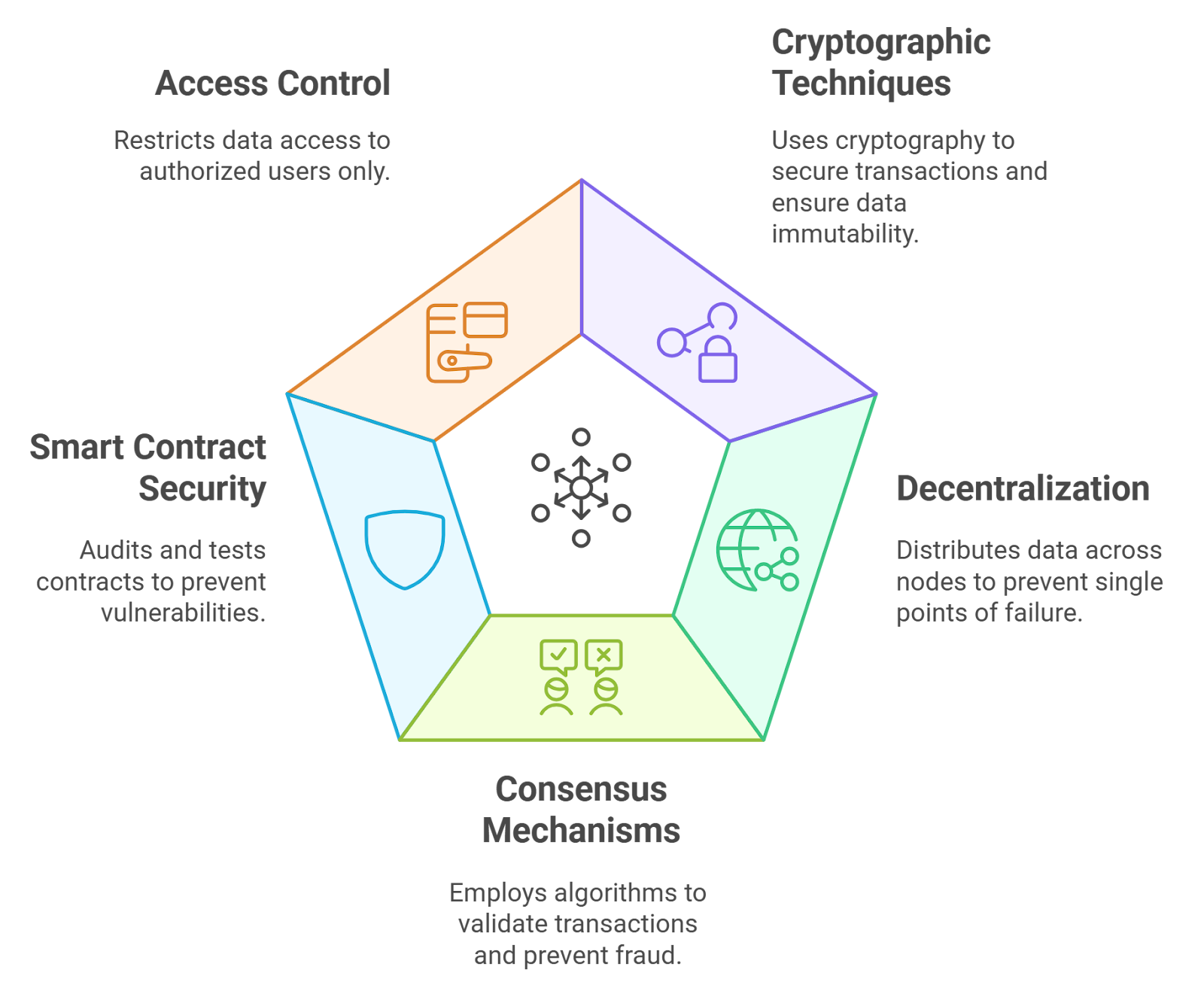
The Role of Cross-Chain Risk Scanners
The sheer complexity and high stakes of cross-chain bridges demand advanced monitoring and prevention tools. This is where cross-chain risk scanners come into play. These systems continuously analyze bridge transactions and behaviors, detecting anomalies before they escalate into full-blown attacks.
For example, tools like XChainWatcher and BridgeGuard employ real-time transaction monitoring and graph-based attack detection, respectively. By flagging suspicious activity, such as unauthorized validator approvals or unusual contract calls, risk scanners provide early warning and actionable intelligence for teams and users alike.
To explore more on why these vulnerabilities persist and how modern mitigations are evolving, you can read our deep dive at this link.
But risk scanners are not just passive observers. Their real power lies in their ability to actively prevent losses by intercepting suspicious transactions and providing automated alerts when attack patterns emerge. Let’s break down how these tools specifically counteract each of the seven most pressing vulnerabilities in today’s cross-chain landscape.
How Risk Scanners Address 7 Key Bridge Vulnerabilities
-

Validator Key Compromise: Attackers gain control of bridge validators, enabling unauthorized asset transfers or minting, as seen in the Ronin and Harmony bridge hacks. How risk scanners help: Tools like XChainWatcher monitor validator behaviors in real time, flagging abnormal signature patterns or sudden validator set changes. In the Ronin hack, such monitoring could have detected the unauthorized validator approvals before $600 million was stolen.
-

Smart Contract Logic Flaws: Bugs in bridge contract code (e.g., reentrancy, unchecked external calls, faulty access controls) allow attackers to bypass intended security checks. How risk scanners help: Solutions like BridgeGuard analyze transaction graphs to detect anomalous contract interactions, while audit tools continuously scan for known vulnerability patterns, reducing the risk of exploits like those seen in the Nomad bridge attack.
-

Insufficient Input Validation: Lack of proper input sanitization on bridge interfaces or contracts enables exploits such as arbitrary call injection or parameter manipulation. How risk scanners help: Automated scanners simulate diverse user inputs and monitor for unexpected contract state changes, alerting teams to injection attempts or abnormal parameter usage before attackers can exploit them.
-

Oracle Manipulation: Attackers exploit weaknesses in price or state oracles relied upon by bridges, leading to incorrect cross-chain state updates and asset mispricing. How risk scanners help: Platforms like Chainlink Risk Management and custom bridge scanners track oracle feeds for inconsistencies or sudden deviations, helping to identify and block suspicious oracle updates that could facilitate asset theft.
-

Centralized Control Points: Bridges with centralized admin keys or multisigs are vulnerable to insider threats, collusion, or key theft, resulting in potential rug pulls or unauthorized withdrawals. How risk scanners help: Continuous monitoring of admin actions and multisig transactions, with alerts for unusual withdrawal patterns or changes in control, empowers teams to respond quickly to insider threats.
-

Replay Attacks: Poorly designed message formats or signature schemes allow attackers to reuse valid messages on different chains or at different times, causing double-spending or asset theft. How risk scanners help: Risk scanners inspect cross-chain message logs for duplicate or out-of-context transactions, flagging suspicious repeats that could indicate replay attacks, and helping teams patch signature schemes promptly.
-

Insecure Cross-Chain Message Validation: Weaknesses in how bridges validate cross-chain proofs (e.g., light client bugs, Merkle proof errors) can let attackers forge transactions or spoof messages. How risk scanners help: Advanced tools like BridgeGuard model proof validation logic and monitor for inconsistencies in proof submissions, ensuring only legitimate cross-chain messages are processed and reducing the risk of forged transactions.
How Risk Scanners Disarm Critical Bridge Attack Vectors
1. Validator Key Compromise: By monitoring the behavior of validators in real-time, risk scanners can detect sudden changes in signing patterns or anomalous approvals that may indicate a compromise. For example, if a validator begins approving large, unexpected transfers, automated alerts can prompt immediate investigation or trigger circuit breakers to halt bridge operations temporarily.
2. Smart Contract Logic Flaws: Automated code analysis and real-time execution monitoring help scanners spot irregularities in contract calls, such as reentrancy attempts or deviations from expected logic flows. This allows teams to patch vulnerabilities before they are exploited in the wild.
3. Insufficient Input Validation: Risk scanners inspect transaction payloads for malformed or unusual data inputs, flagging attempts at arbitrary call injection or parameter manipulation. Some tools even simulate transactions in a sandbox before execution to catch exploits preemptively.
4. Oracle Manipulation: By cross-referencing oracle data with multiple independent sources and monitoring for outlier values, scanners can detect and block attempts to feed false information into the bridge’s decision-making process. This is crucial for preventing asset mispricing and unauthorized state changes.
5. Centralized Control Points: Scanners track the activity of admin keys and multisig wallets, alerting teams to any suspicious withdrawals or configuration changes. Enhanced transparency around key movements can deter insider threats and provide an audit trail in the event of a breach.
6. Replay Attacks: By analyzing the uniqueness of transaction signatures and message formats across chains, risk scanners can identify duplicate or replayed messages, blocking double-spending attempts before they cause harm.
7. Insecure Cross-Chain Message Validation: Advanced scanners validate the integrity of cross-chain proofs in real-time, checking for inconsistencies or evidence of tampering in Merkle proofs and light client data. This prevents attackers from forging or spoofing cross-chain transactions.
The Future of Cross-Chain Bridge Security
As the cross-chain ecosystem matures, attackers will continue to innovate – but so will defenders. The next generation of cross-chain risk scanners is moving toward AI-driven anomaly detection, collaborative threat intelligence, and automated incident response. These advancements promise not just to detect attacks faster, but to stop them in their tracks.
For developers, integrating robust risk scanning tools is no longer optional. Regular smart contract audits, continuous transaction monitoring, and transparent key management are the new baseline for responsible bridge deployment. For users, staying informed about which bridges employ these protections can make all the difference between safe passage and catastrophic loss.
Ultimately, the security of cross-chain bridges will determine the pace and scope of DeFi’s next wave of growth. By understanding the seven key vulnerabilities and leveraging state-of-the-art risk scanners, the community can build a more resilient, interoperable future for blockchain finance.






