
The rapid expansion of multi-chain ecosystems has been a game-changer for decentralized finance, enabling seamless asset flows and interoperability across disparate blockchains. But as protocols race to connect more chains and facilitate complex cross-chain messaging, the security landscape has evolved in ways that demand urgent attention. Multi-chain growth is not just multiplying opportunities – it’s amplifying risks, with cascading vulnerabilities now threatening the very fabric of cross-chain DeFi.
Multi-Chain Security Risks: Attack Surfaces Multiply
Every new chain integrated into a cross-chain messaging protocol introduces its own unique vulnerabilities, expanding the total attack surface. This interconnectedness means that an exploit on a single chain can have far-reaching, domino-like consequences across all connected networks. The Ronin Bridge hack in 2022, which resulted in a $625 million loss, is a stark illustration: attackers compromised the majority of the bridge’s validators, exploiting a single weak link to drain assets across multiple chains (source).
As cross-chain messaging grows more complex, the challenge isn’t just about protecting individual blockchains – it’s about securing the connective tissue that binds them. Attackers are increasingly targeting these protocols, seeking out overlooked vulnerabilities that arise from the interplay of different consensus mechanisms, validator sets, and smart contract standards.
Smart Contract Vulnerabilities: The Achilles’ Heel of Cross-Chain Protocols
Cross-chain messaging relies heavily on smart contracts to coordinate asset transfers and state changes between blockchains. These contracts are often highly complex, juggling multiple chains’ logic and security assumptions. A single bug or logic flaw can have catastrophic consequences. The Nomad Bridge exploit in 2022, where a faulty contract initialization allowed attackers to drain $190 million, is just one high-profile example (source).
Unlike traditional DeFi exploits, cross-chain vulnerabilities can propagate rapidly across ecosystems. A compromised contract on one chain may allow attackers to manipulate assets or messages on several others, amplifying losses and undermining trust in the broader multi-chain infrastructure.
Key Security Risks in Multi-Chain Cross-Chain Messaging
-
Expanded Attack Surface: Integrating multiple blockchains increases the number of potential vulnerabilities. A breach in one chain can cascade across others, as seen in the Ronin Bridge hack where attackers exploited validator weaknesses to steal $625 million.
-

Smart Contract Vulnerabilities: Cross-chain messaging relies on complex smart contracts, which are susceptible to bugs and logic errors. The Nomad Bridge hack in 2022, resulting in a $190 million loss, highlighted the risks of faulty contract initialization.
-
Consensus Mechanism Disparities: Different chains use varied consensus models, leading to inconsistencies in transaction finality. Attackers may exploit these differences for double-spend attacks or invalid transactions.
-
Replay Attacks: Similar signing schemes across chains can enable replay attacks, where a transaction from one chain is maliciously reused on another, causing unintended asset transfers.
-

Centralization of Validators: Many bridges depend on a small set of validators, creating single points of failure. This centralization increases vulnerability to collusion or compromise, undermining trust in the protocol.
Cascading Vulnerabilities: Consensus Disparities and Replay Attacks
The diversity of consensus mechanisms across blockchains introduces new risk vectors for cross-chain messaging. Inconsistent transaction finality and validation standards can be exploited for double-spending or to inject invalid transactions into the system (source). For instance, chains with slower finality are especially vulnerable to race conditions and reorg attacks in a multi-chain context.
Replay attacks are another growing concern. When chains use similar transaction signing schemes, an attacker might replay a valid transaction from one network onto another, causing unintended asset movements or contract executions. Strategies like embedding chain-specific identifiers in signatures and adopting standards such as EIP-712 are critical for mitigation (source).
Centralization: Single Points of Failure in the Multi-Chain Era
Despite their decentralized ethos, many cross-chain bridges still rely on a small group of validators or relayers, creating critical single points of failure. This centralization not only increases the risk of collusion but also makes these protocols attractive targets for attackers seeking maximum impact with minimal effort. Decentralizing validator sets and incorporating robust multi-signature schemes are essential steps toward hardening cross-chain infrastructure against coordinated attacks.
Mitigating these amplified risks requires a holistic, data-driven strategy. Auditing teams must go far beyond traditional smart contract reviews: they need to analyze how different chains interact, scrutinize validator configurations, and model the potential for cascading failures. The sheer complexity of multi-chain environments means that security assumptions valid on one network may not hold on another, this is fertile ground for novel attack vectors that are often missed by standard audits.
One of the most effective approaches is to enforce rigorous cross-chain protocol audits that include formal verification, simulation of adversarial scenarios, and continuous monitoring. Real-time risk scanning tools are now indispensable for identifying new vulnerabilities as soon as they emerge. The adoption of standardized cross-chain messaging formats and interoperability standards can further reduce the likelihood of logic mismatches and signature replay issues.
Proactive Defense: Mitigation Strategies for Multi-Chain Security
To strengthen the security posture of cross-chain messaging protocols in a multi-chain world, projects are increasingly embracing a blend of decentralized infrastructure, robust auditing, and community-driven oversight. Here’s what leading security experts recommend:
Top Strategies to Reduce Multi-Chain Security Risks
-
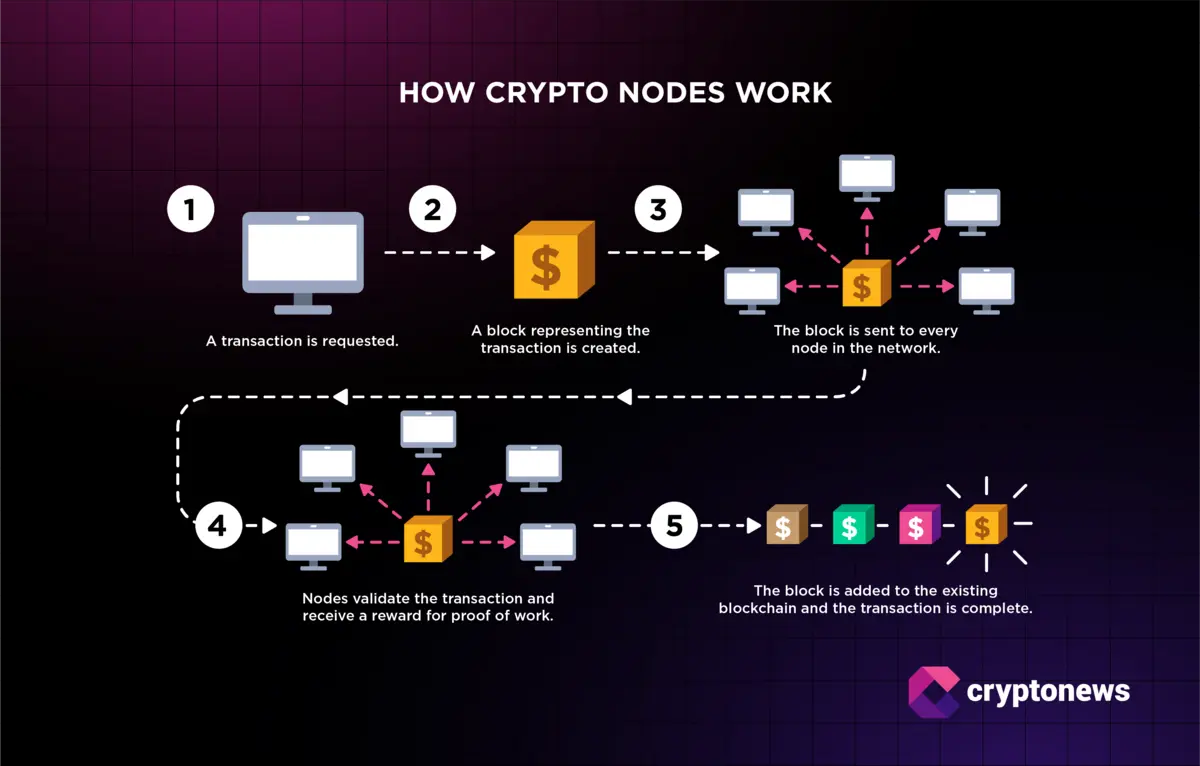
Adopt Decentralized Validator Architectures: Implement decentralized validator sets and multi-signature schemes to eliminate single points of failure and reduce the risk of validator collusion or compromise. Leading protocols like Chainlink CCIP and Polkadot utilize decentralized infrastructure for enhanced security.
-

Conduct Rigorous Smart Contract Audits and Formal Verification: Regularly audit smart contracts and employ formal verification tools to catch vulnerabilities before deployment. Top security firms like ConsenSys Diligence and Trail of Bits are trusted by major DeFi projects for comprehensive code reviews.
-
Implement Cross-Chain Communication Standards: Use standardized protocols such as Inter-Blockchain Communication (IBC) and EIP-712 for secure, interoperable messaging and to prevent replay attacks across chains.
-

Monitor and Respond to Threats with Real-Time Security Analytics: Deploy real-time monitoring solutions like CertiK Skynet and Chainalysis to detect suspicious activity, enabling rapid incident response and minimizing potential losses.
- Decentralized Validator Sets: Distribute control among a wide array of validators to avoid single points of failure.
- Continuous Smart Contract Audits: Employ both manual and automated tools to catch vulnerabilities before they can be exploited.
- Standardized Protocols: Adopt industry-wide standards for message formats, consensus bridging, and relay mechanisms.
- Real-Time Risk Monitoring: Use advanced analytics platforms to detect abnormal activity and emerging threats across all integrated chains.
- Community Engagement: Encourage open disclosure programs and incentivize white-hat reporting to crowdsource security insights.
For teams building in this space, it’s critical to recognize that the risk profile isn’t static, each new chain integration or protocol upgrade can shift the threat landscape overnight. Staying ahead means leveraging up-to-date intelligence feeds, integrating with real-time risk scanners, and collaborating with the broader security research community.
Ecosystem Impact: Why Amplified Risk Demands Better Tools
The consequences of amplified risk in multi-chain environments are not limited to individual protocols, they ripple across the entire DeFi landscape. A single high-profile exploit can erode trust in cross-chain solutions as a whole, draining liquidity and stalling innovation. This makes transparent risk analysis and proactive defense not just a technical necessity but an ecosystem imperative.
Platforms offering real-time cross-chain protocol audits and vulnerability scanning are emerging as critical infrastructure for developers, investors, and users alike. By empowering stakeholders with actionable intelligence, such as up-to-the-minute alerts on validator anomalies or contract exploits, these tools help prevent cascading failures before they spiral out of control.
Amplified risk requires amplified vigilance. In the rapidly evolving world of blockchain interoperability, security is not a one-off checklist but an ongoing process, one that must adapt in lockstep with every new chain added to the network.
The future of multi-chain DeFi depends on our ability to anticipate threats before they materialize. With rigorous audits, decentralized architectures, and dynamic monitoring systems, we can transform amplified risk into an opportunity for building trust, and resilience, across the entire blockchain ecosystem.







