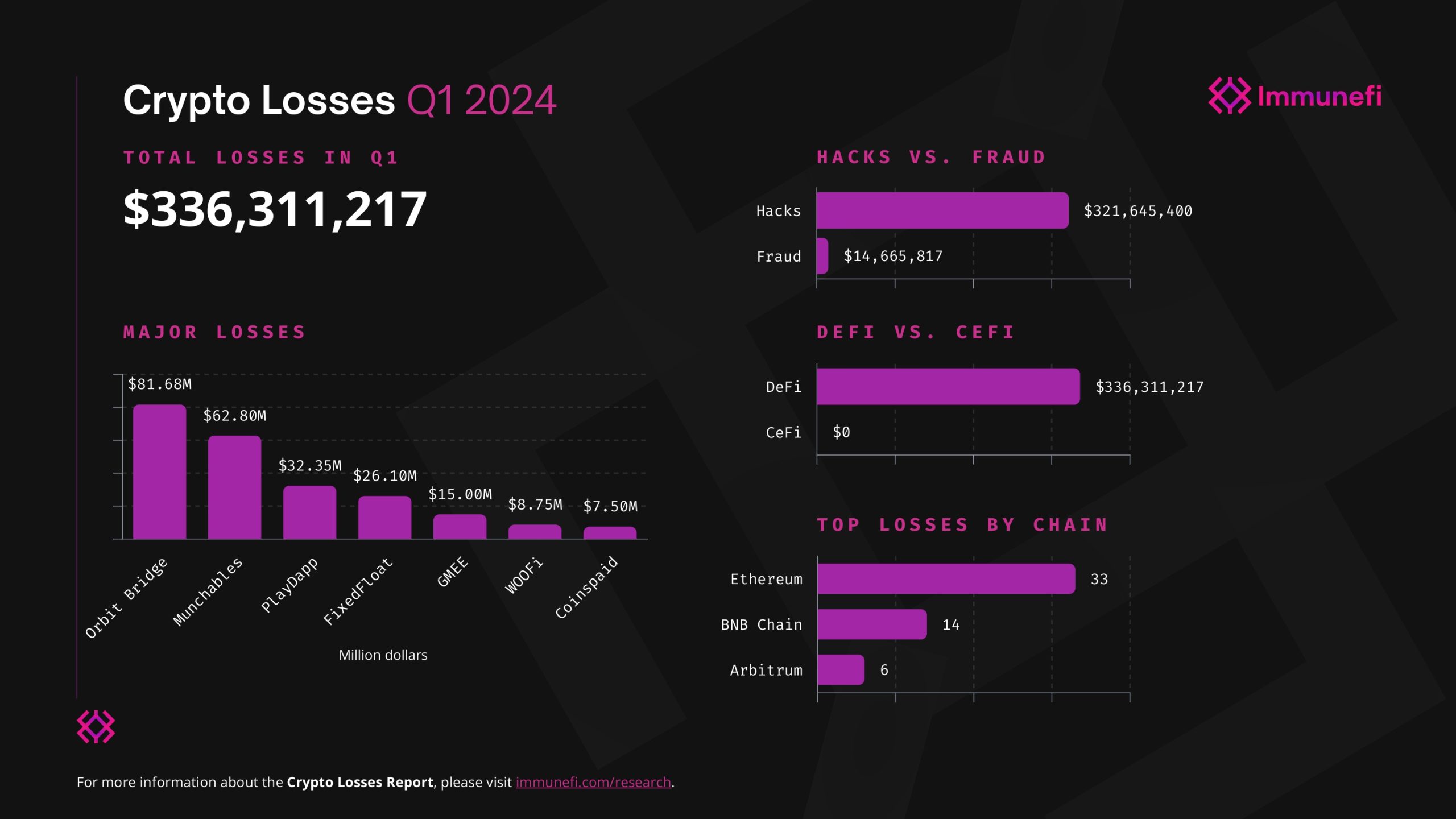
Cross-chain bridges are the lifeblood of blockchain interoperability, but they’re also the industry’s Achilles’ heel. Since May 2021, these bridges have been at the center of roughly $3.2 billion in losses, making them a top target for hackers. Why? Because the complexity of moving assets and data between blockchains creates a playground for attackers, and a minefield for developers and users alike. In 2024, as DeFi continues to expand across chains, the need for rigorous cross-chain bridge audit practices has never been clearer.

The Three Most Critical Cross-Chain Bridge Risks in 2024
Let’s break down the specific vulnerabilities that auditors and security teams are laser-focused on right now:
Top 3 Cross-Chain Bridge Risks in 2024
-

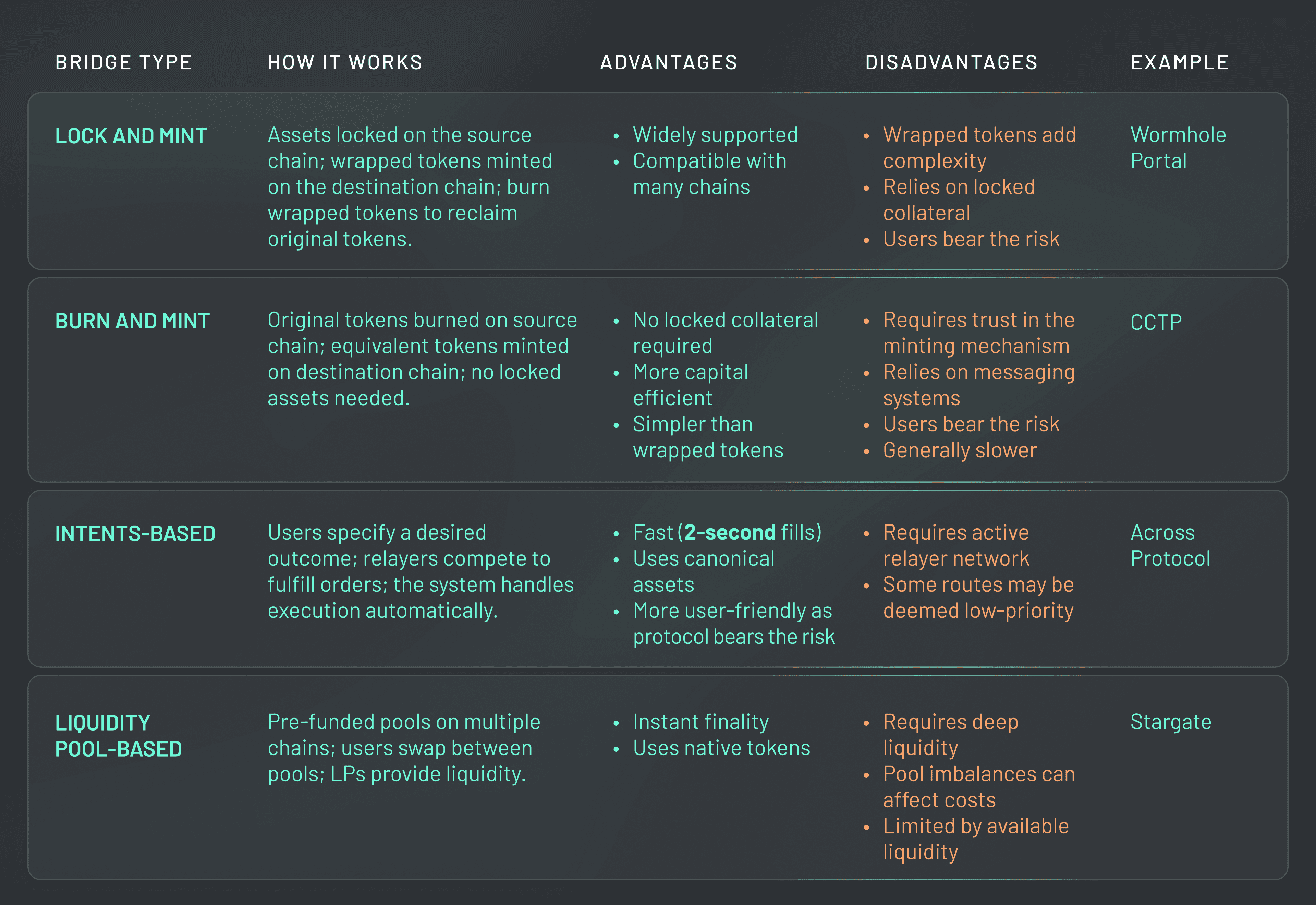
Compromised Private Key Management: When private keys controlling bridge validators or relayers are stolen or mismanaged, attackers can seize control of the bridge, redirect funds, or disrupt operations. High-profile exploits like the Ronin Bridge hack (over $600 million lost) highlight the devastating impact of poor key security.
-

Exploitable Smart Contract Logic: Vulnerabilities in unaudited or poorly designed bridge smart contracts can be exploited to manipulate transactions or drain funds. The Wormhole bridge incident, which saw $325 million stolen, is a prime example of how critical robust contract logic and thorough audits are.
-
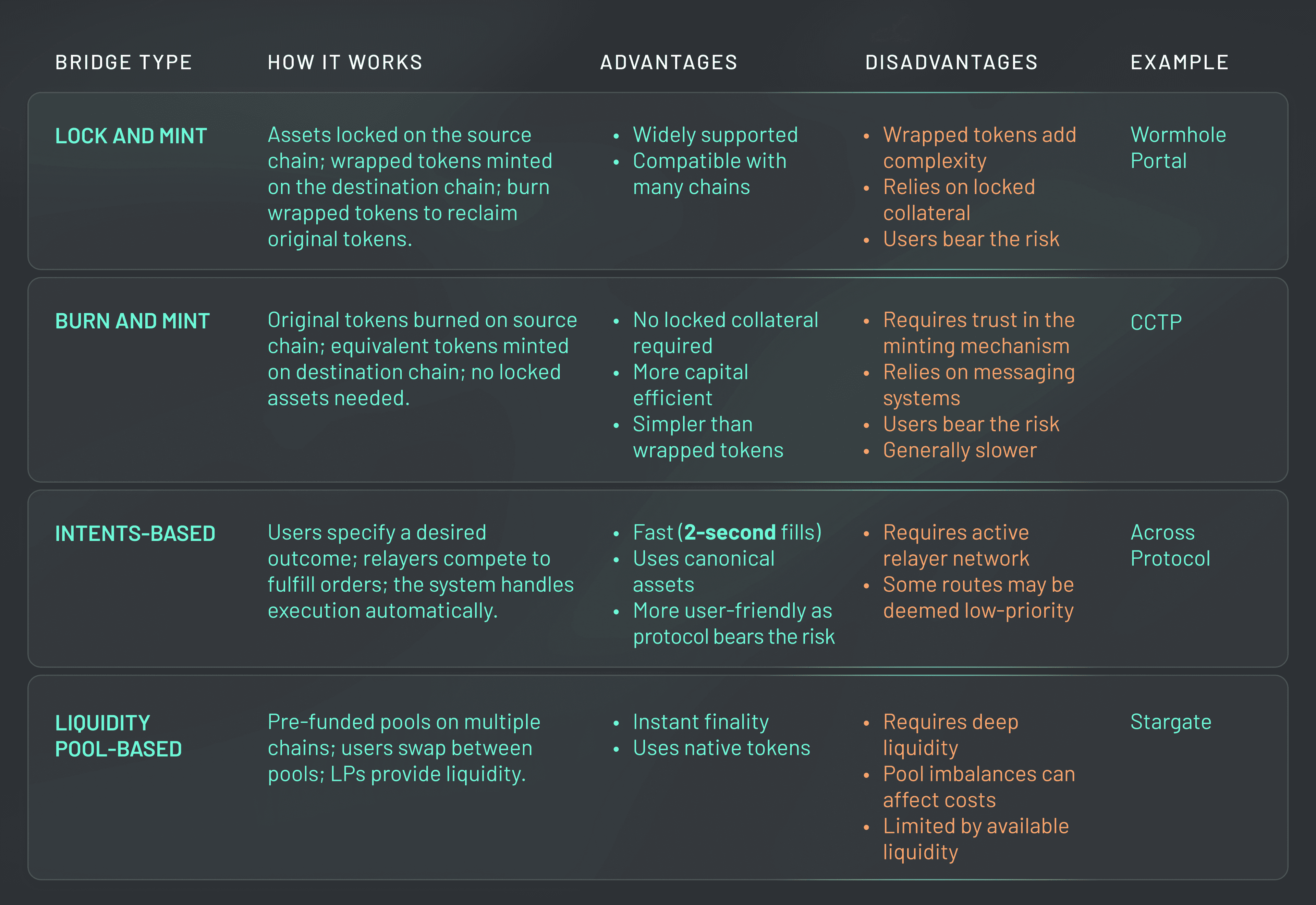
Centralization Risks in Governance or Relaying: Relying on a small group of validators, operators, or centralized governance creates single points of failure. Attackers or insiders can collude, or a single compromised entity can jeopardize the entire bridge, making decentralization and transparency vital for security.
Here’s why these matter:
- Compromised Private Key Management: If validators or relayers lose control of their keys, or if those keys are poorly protected, the entire bridge can be hijacked. This is how attackers pull off nine-figure exploits in a single transaction.
- Exploitable Smart Contract Logic: Even one overlooked bug in a bridge’s smart contract can open the door to massive fund drains. The $325 million Wormhole exploit is a textbook example of how unaudited or poorly designed contracts become ticking time bombs.
- Centralization Risks: When a bridge relies on a handful of operators or centralized governance, it creates single points of failure, making collusion or targeted attacks much easier to execute.
If you want to dig deeper into real-world incidents and root causes, check out our recent incident analysis.
The Leading Audit Tools Powering Bridge Security
No human team can keep up with every emerging threat alone. That’s why advanced tools are now essential for any serious blockchain bridge risk analysis. Here are the three platforms dominating cross-chain bridge security right now:
Top 3 Tools for Cross-Chain Bridge Audits in 2024
-

ChainSecurity Bridge Auditor: This advanced tool offers automated vulnerability scanning and formal verification for cross-chain bridge smart contracts. By leveraging state-of-the-art analysis, it helps identify exploitable logic and access control flaws before attackers can exploit them.
-

CertiK Skynet: A leading continuous monitoring platform, CertiK Skynet provides real-time surveillance of bridge contracts and on-chain behaviors. Its AI-powered alerts help projects detect suspicious activity and respond rapidly to emerging threats.
-

Immunefi Bug Bounty Platform: Specializing in incentivizing white-hat hackers, Immunefi enables projects to crowdsource security by rewarding the discovery of cross-chain bridge exploits. This proactive approach has helped prevent numerous high-profile attacks.
- ChainSecurity Bridge Auditor: Automates vulnerability scanning and formal verification of complex bridge logic, catching subtle bugs before they go live.
- CertiK Skynet: Offers continuous, real-time monitoring of on-chain behaviors and contract states to flag suspicious activity as soon as it happens.
- Immunefi Bug Bounty Platform: Incentivizes white-hat hackers worldwide to find and responsibly disclose critical cross-chain exploits before malicious actors do.
Together, these tools form a robust defense-in-depth strategy, covering everything from code review to live monitoring and community-driven testing.
Best Practices That Actually Move the Needle in Bridge Security
You can’t just rely on tech, you need strong processes too. The most forward-thinking projects are setting new standards with these actionable best practices:
Top Risks, Tools, and Best Practices for Securing Cross-Chain Bridges in 2024
-
Risk 1: Compromised Private Key Management — Poor key management can lead to validator or relayer takeover, enabling attackers to control bridge operations and steal funds. Recent high-profile bridge hacks have often exploited weak or centralized key storage.
-

Risk 2: Exploitable Smart Contract Logic — Unaudited or poorly designed bridge contracts may contain vulnerabilities that attackers can exploit to drain assets or manipulate transactions. Thorough code review and formal verification are essential to prevent such exploits.
-

Risk 3: Centralization Risks — Relying on a single validator set or centralized governance creates single points of failure. Attackers or insiders can compromise the bridge if decentralization is lacking.
-

Tool 1: ChainSecurity Bridge Auditor — An advanced platform for automated vulnerability scanning and formal verification of bridge smart contracts, helping identify and remediate critical security issues before deployment.
-
Tool 2: CertiK Skynet — Provides continuous, real-time monitoring of bridge contracts and on-chain behaviors, alerting teams to suspicious activity and emerging threats.
-
Tool 3: Immunefi Bug Bounty Platform — Specializes in incentivizing white-hat hackers to discover and responsibly disclose cross-chain bridge exploits, reducing the risk of undetected vulnerabilities.
-
Best Practice 1: Enforce Multi-Sig and Threshold Cryptography — Require multiple approvals for all key management processes, reducing the risk of single key compromise and unauthorized access.
-

Best Practice 2: Mandate Regular Third-Party Audits and Public Disclosure — Schedule frequent, independent audits and publish audit reports to foster transparency and trust in bridge security.
-
Best Practice 3: Implement Permissionless Validator Sets and Decentralized Governance — Reduce single points of failure by allowing open participation and decentralized decision-making in bridge operations.
- Enforce Multi-Sig and Threshold Cryptography: Every key management process should require multiple signers, no more single points of compromise. Threshold cryptography adds even more resilience against collusion or loss.
- Mandate Regular Third-Party Audits: Don’t just audit once, require frequent reviews by independent experts. And always publish those reports so users know what’s under the hood.
- Implement Permissionless Validator Sets: Open up validator participation and decentralize governance to make it much harder for any single group to take down (or corrupt) your bridge.
If you want to see how these practices stack up against real-world attack vectors, and why they’re critical for stopping billion-dollar exploits, explore our deep dive on common attack vectors and mitigations here.
But here’s the truth: even with the best intentions, most bridges still fall short unless they combine these practices with relentless vigilance. The rapid pace of DeFi innovation means new vulnerabilities are always lurking around the corner. That’s why the most resilient teams treat security as a living process, not a checkbox.
Bringing It All Together: A Modern Security Stack for Cross-Chain Bridges
Let’s connect the dots between risk, tooling, and process. When you layer multi-sig key management on top of real-time monitoring from CertiK Skynet, and back it up with ongoing audits and bug bounties via ChainSecurity and Immunefi, you’re building true defense-in-depth. Add in permissionless validator sets and you dismantle the biggest single point of failure left in most bridges today.
This isn’t just theory, these are the same strategies that separated protocols that survived 2024’s wave of cross-chain exploits from those that lost hundreds of millions. The data is clear: projects that combine robust key management, automated auditing, and decentralized governance have dramatically lower incident rates. If you’re serious about securing your bridge (and your users’ assets), this is the playbook to follow.
Why Continuous Audit and Public Transparency Matter
One-off audits are no longer enough in a landscape where exploits can be discovered and weaponized overnight. Regular third-party reviews force teams to stay honest and up-to-date with emerging threats. Just as importantly, publishing audit reports builds trust, users can see exactly what’s been checked and what remains a work in progress.
If you’re evaluating a bridge protocol or considering deploying your own cross-chain solution, demand public proof of security practices, not just promises. Look for recent audits from independent firms, evidence of active bug bounty programs on Immunefi, and transparent documentation around validator set management.
Which best practice do you believe is most important for cross-chain bridge security?
Cross-chain bridges have become prime targets for billion-dollar exploits. Security experts recommend several best practices to protect against these risks. Which one do you think matters most for keeping bridges secure?
Looking Ahead: Evolving Threats and Adaptive Defenses
The arms race between attackers and defenders isn’t slowing down. As bridges become more composable and feature-rich, expect new types of exploits targeting protocol upgrades or cross-chain message relaying logic. Staying ahead will require not just technical rigor but also community engagement, bug bounties, open-source collaboration, and rapid response protocols when things go wrong.
If you want to stay current on top vulnerabilities in blockchain bridge cross-chain messaging, and how leading teams are adapting, bookmark our ongoing coverage at Top Vulnerabilities in Blockchain Bridge Cross-Chain Messaging.
Key Takeaways for 2024
- Never compromise on private key security: Multi-sig or threshold cryptography is non-negotiable.
- Treat audits as an ongoing process: Use tools like ChainSecurity Bridge Auditor for every deployment cycle.
- Pursue real-time monitoring: CertiK Skynet should be running 24/7 over all critical contracts.
- Decentralize governance: Permissionless validator sets are your best bet against collusion risks.
- Crowdsource defense: Incentivize white-hats through Immunefi to catch what automation misses.
The bottom line? Billion-dollar exploits aren’t inevitable, but they’re only avoidable if we treat bridge security as both an art and a science. The protocols that thrive will be those willing to invest in layered defenses, radical transparency, and constant improvement. Don’t wait until your users become the next headline, raise your standards now.






