Blockchain bridges are the connective tissue of decentralized finance, enabling assets and data to move seamlessly across disparate blockchain ecosystems. Yet, their very function as gateways to liquidity and interoperability also places them squarely in the crosshairs of sophisticated attackers. The past two years have seen over $2 billion lost to bridge exploits, a sobering testament to their status as some of the most lucrative and vulnerable infrastructure in crypto. To understand why blockchain bridges are prime targets, we need to examine the specific security risks and attack vectors that consistently undermine cross-chain messaging protocols.
Bridge Security Risks: Why Attackers Focus Here
Unlike single-chain protocols, bridges must coordinate state across multiple networks, each with its own consensus model, security assumptions, and operational quirks. This complexity creates a sprawling attack surface where even minor oversights can have catastrophic consequences. Let’s break down the five most critical vulnerabilities that make blockchain bridges especially attractive to adversaries:
Top 5 Security Vulnerabilities in Blockchain Bridges
-
Compromised Validator or Oracle Manipulation: Attackers gain control over a majority of bridge validators or manipulate oracles to approve fraudulent cross-chain transactions, enabling unauthorized asset transfers. Example: The Ronin Bridge hack in 2022 resulted in a $625 million loss after attackers compromised validator nodes.
-
Smart Contract Exploits and Logic Flaws: Vulnerabilities in bridge smart contracts, such as unchecked external calls, reentrancy, or improper event validation, allow attackers to drain bridge funds or mint unbacked assets. Example: The Wormhole Bridge exploit in 2022 led to a $325 million loss due to a smart contract flaw.
-

Weak or Incomplete On-Chain Event Verification: Insufficient verification of source chain events (e.g., block headers, proofs) enables attackers to forge or replay messages, resulting in double-spending or asset theft. Example: The Nomad Bridge attack in 2022 exploited faulty event verification, allowing attackers to drain $190 million.
-
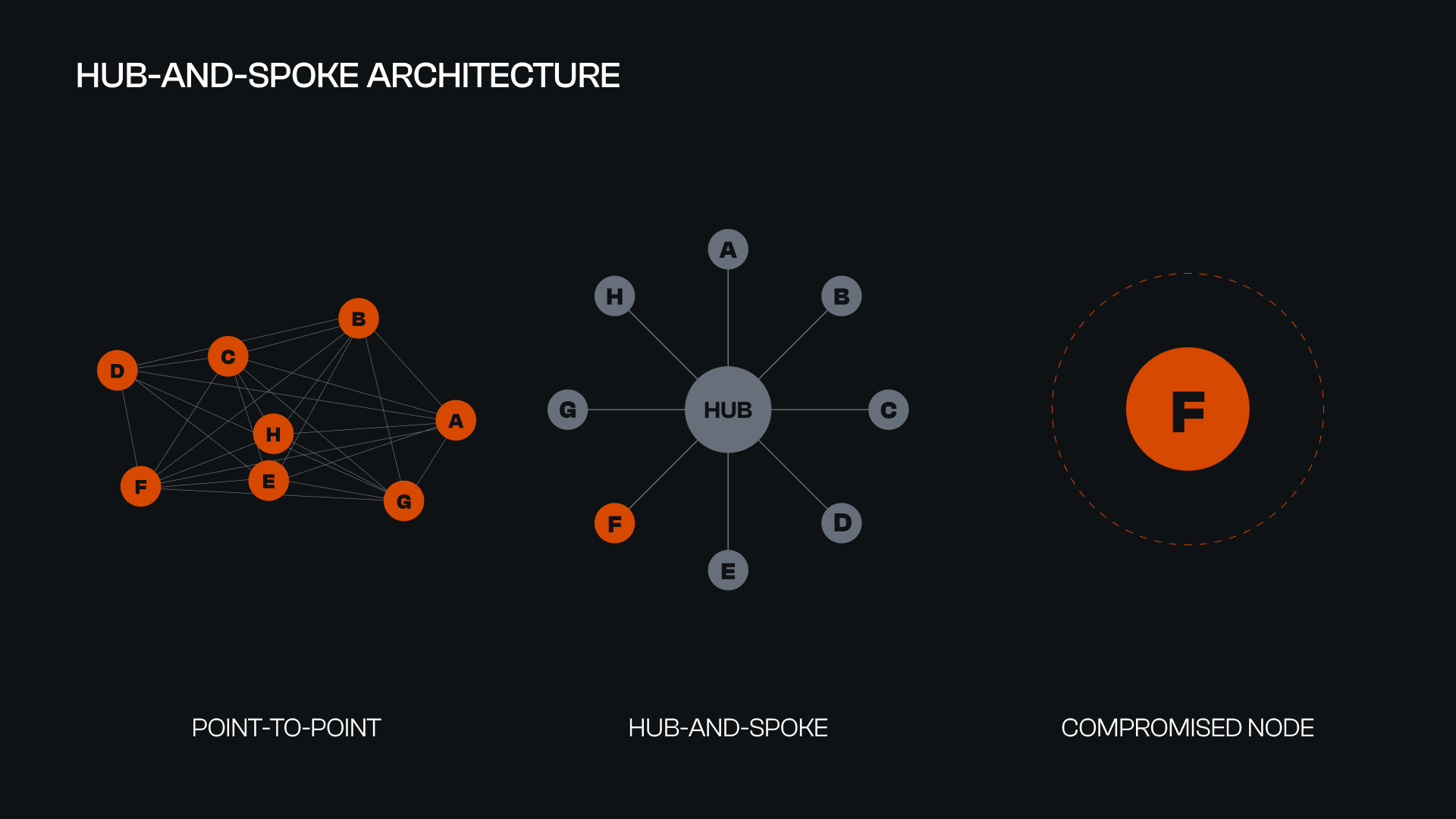
Private Key or Admin Key Compromise: Attackers obtain privileged keys controlling bridge contracts or relayers, leading to direct asset theft or protocol manipulation. Such compromises have led to major losses across several bridges due to inadequate key management practices.
-
Cross-Chain Replay Attacks: Malicious actors replay valid messages on different chains or bridge instances, exploiting insufficient message uniqueness and nonce management to duplicate transactions or drain funds. Replay attacks remain a critical threat in cross-chain messaging protocols.
1. Compromised Validator or Oracle Manipulation
Most cross-chain messaging relies on validators or oracles to confirm that an event on one chain (like locking tokens) has genuinely occurred before triggering a corresponding action on another chain (such as minting wrapped assets). If attackers manage to compromise a majority of these validators – whether by hacking private keys or exploiting poor operational security – they can approve fraudulent transactions at will. The infamous Ronin Bridge hack is a case in point: attackers gained control over five out of nine validator nodes, resulting in an unprecedented $625 million theft (source).
This centralization risk is inherent in bridges that rely on small validator sets or trusted multisigs. The fewer parties involved in verification, the easier it is for attackers to seize control and siphon funds undetected.
2. Smart Contract Exploits and Logic Flaws
Bridges are powered by intricate smart contracts designed to lock, mint, burn, or release assets based on cross-chain messages. Any flaw – from unchecked external calls to mismanaged event validation – can open the door for devastating exploits. For example, if a contract fails to properly verify proofs from the source chain or allows reentrancy attacks during token transfers, adversaries may drain bridge liquidity or mint unbacked tokens.
The Wormhole bridge exploit illustrates this danger vividly: a vulnerability in smart contract logic enabled an attacker to mint 120,000 wrapped ETH without equivalent collateralization on Ethereum (source). Such incidents highlight why rigorous audits and formal verification are non-negotiable for any protocol bridging value between chains.
3. Weak or Incomplete On-Chain Event Verification
A robust bridge must ensure that every message it relays is anchored in genuine events from its source chain – typically by verifying block headers and cryptographic proofs directly on-chain. When this verification is weak or incomplete (for instance, relying solely on off-chain relayers), attackers may forge messages or replay old ones for double-spending attacks.
This vulnerability was at play during the Nomad Bridge incident, where faulty contract initialization allowed almost anyone to mimic valid transactions and drain $190 million from the protocol (source). Without comprehensive event validation mechanisms, even well-intentioned bridges become sitting ducks for determined adversaries.
4. Private Key or Admin Key Compromise
The security of blockchain bridges often hinges on the protection of privileged keys, whether they control bridge contracts, relayer networks, or administrative functions. If attackers succeed in stealing or socially engineering access to these keys, the consequences are immediate and devastating: direct asset theft, protocol upgrades to malicious code, or even permanent denial of service. This risk is amplified by the fact that some bridges still rely on multisig wallets with a limited number of signers or use centralized cloud storage for key management, making them attractive targets for phishing campaigns and advanced persistent threats.
History has shown that even a single compromised admin key can undermine an entire cross-chain protocol. The lesson is clear: bridges must employ hardware security modules (HSMs), distributed key generation (DKG), and frequent rotation policies to reduce the blast radius of a potential compromise.
5. Cross-Chain Replay Attacks
Replay attacks exploit insufficient message uniqueness across bridge protocols. When a valid cross-chain message can be replayed, either on the same bridge instance or across different chains, malicious actors can duplicate asset transfers, drain liquidity pools, or trigger unauthorized operations. The root cause often lies in poor nonce management or the reuse of message identifiers without proper scoping to specific chains and contracts.
For example, if a bridge does not bind each message to a unique transaction hash and chain ID, attackers may capture legitimate messages from one context and re-broadcast them in another, effectively double-spending assets or circumventing withdrawal limits. As cross-chain activity increases, so too does the sophistication of replay exploits, making strong anti-replay mechanisms essential for any modern interoperability solution.
Building Safer Cross-Chain Messaging: Practical Safeguards
Given these critical vulnerabilities, what steps can projects and users take to improve blockchain bridge security? Here are several best practices:
- Decentralize validator sets: Increase the number and diversity of validators/oracles involved in consensus to reduce single points of failure.
- Implement layered key management: Use multi-party computation (MPC), HSMs, and regular audits for all privileged keys.
- Enforce robust on-chain verification: Require cryptographic proofs anchored in source chain consensus before releasing assets.
- Avoid logic complexity where possible: Simpler smart contracts are easier to audit and less prone to subtle bugs.
- Add anti-replay protections: Bind every cross-chain message to unique nonces, transaction hashes, and chain IDs.
Staying Ahead with Real-Time Risk Scanning
The landscape of blockchain bridge security is evolving rapidly, and so too must our defenses. Proactive risk scanning tools now allow developers and users alike to monitor bridges for emerging threats in real time. These platforms analyze contract upgrades, validator behavior changes, unusual asset flows, and potential configuration errors before they escalate into full-blown incidents. By leveraging continuous monitoring alongside rigorous audits and formal verification techniques (source), cross-chain protocols can catch vulnerabilities early, often before attackers do.
Top 5 Security Vulnerabilities in Blockchain Bridges
-

Compromised Validator or Oracle Manipulation: Attackers gain control over a majority of bridge validators or manipulate oracles to approve fraudulent cross-chain transactions, enabling unauthorized asset transfers. This centralization risk was exploited in the Ronin Bridge hack, resulting in a $625 million loss.
-

Smart Contract Exploits and Logic Flaws: Vulnerabilities in bridge smart contracts—such as unchecked external calls, reentrancy, or improper event validation—allow attackers to drain bridge funds or mint unbacked assets. The Wormhole Bridge exploit in 2022 is a notable example, where a smart contract flaw led to a $325 million theft.
-

Weak or Incomplete On-Chain Event Verification: Insufficient verification of source chain events (like block headers or proofs) enables attackers to forge or replay messages, resulting in double-spending or asset theft. This vulnerability has been highlighted in multiple bridge incidents and remains a fundamental challenge.
-
Private Key or Admin Key Compromise: Attackers obtain privileged keys controlling bridge contracts or relayers, leading to direct asset theft or protocol manipulation. Poor key management practices have led to significant losses across the industry.
-
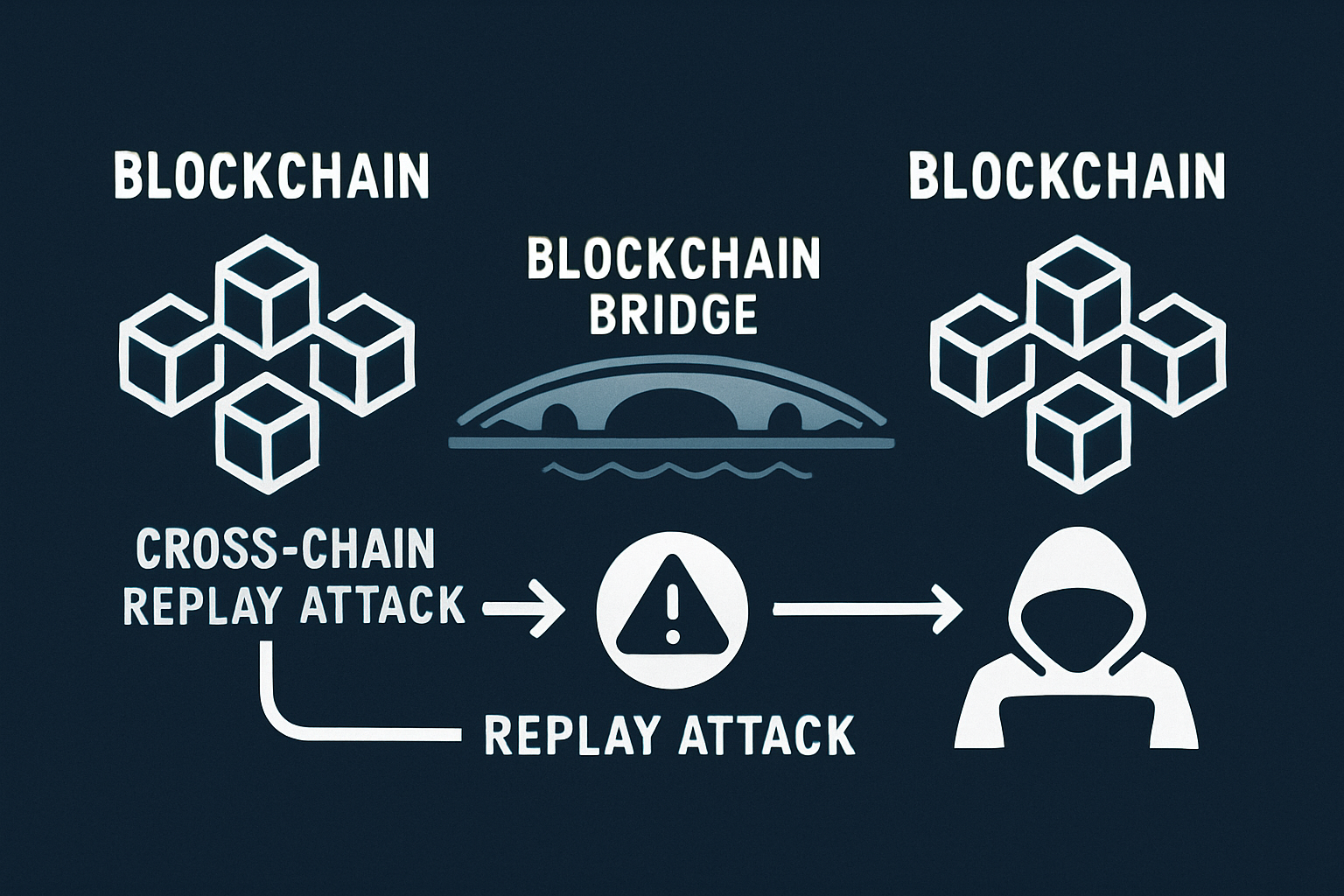
Cross-Chain Replay Attacks: Malicious actors replay valid messages on different chains or bridge instances, exploiting insufficient message uniqueness and nonce management to duplicate transactions or drain funds. Robust message uniqueness and nonce tracking are essential to mitigate this risk.
The future of decentralized finance depends on secure interoperability. By understanding these attack vectors, and adopting technology and governance that address them head-on, the community can build bridges that support innovation without sacrificing safety. As always in crypto: vigilance is not optional; it’s fundamental.






