
In the rapidly evolving world of blockchain interoperability, security is paramount. As more value flows across chains, the risks associated with cross-chain messaging have become painfully clear: high-profile bridge exploits and protocol hacks have cost users billions. But there’s a new paradigm changing the game provides proof-based settlement. By leveraging cryptographic proofs instead of trusted intermediaries, proof-based settlement is transforming how blockchains communicate, making cross-chain messaging both safer and more efficient.
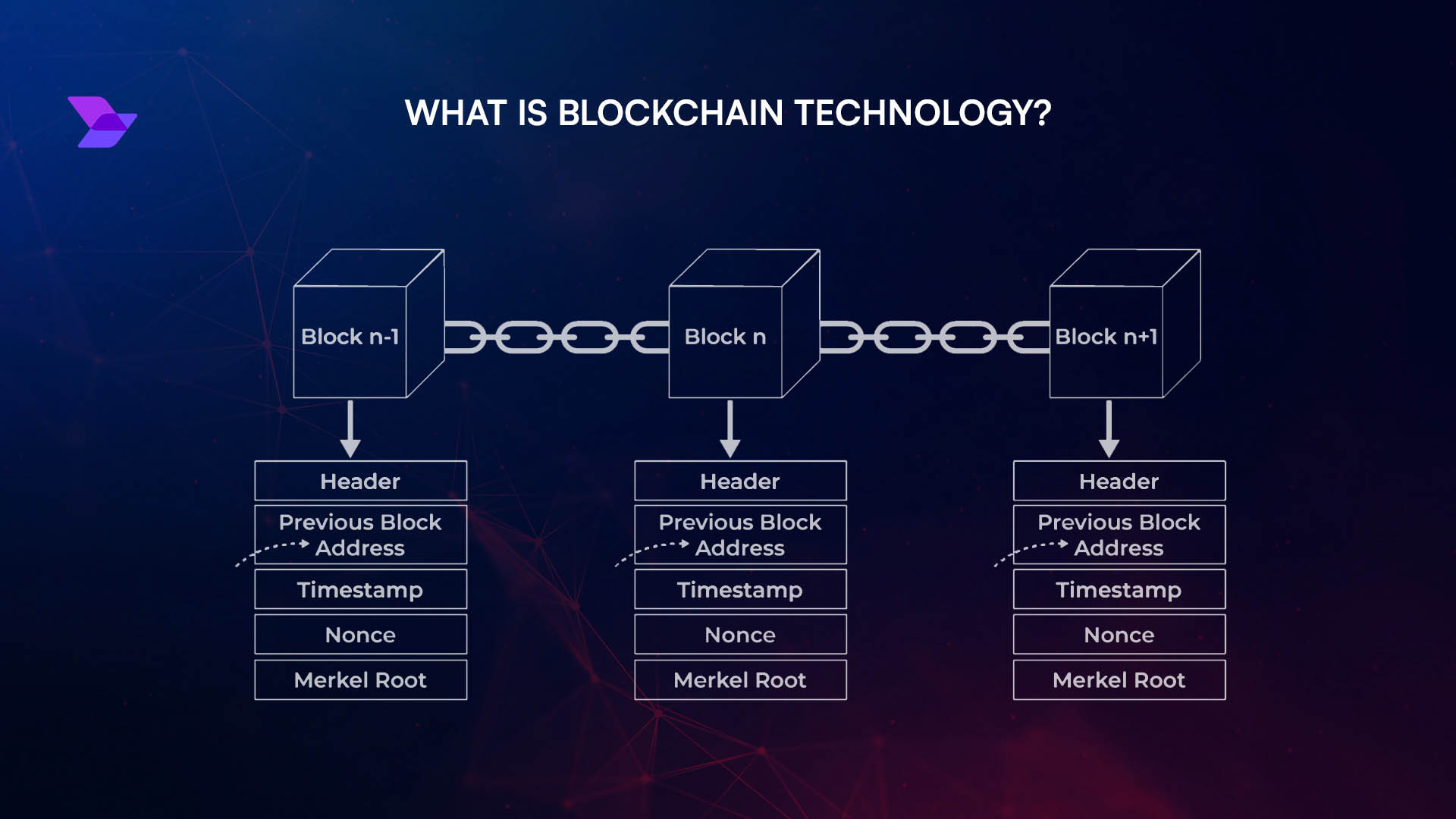
Why Proof-Based Settlement Matters for Cross-Chain Security
Traditional bridges and messaging protocols often rely on multisigs or third-party validators to verify messages between chains. While these systems can be fast, they introduce critical centralization points and attack surfaces. If a validator set is compromised, so is the bridge, and history has shown that attackers are quick to exploit these weaknesses.
Proof-based settlement flips this model on its head. Instead of trusting a group of external actors, one chain can verify another chain’s state using cryptographic proofs such as zero-knowledge proofs (ZKPs) or light clients. This approach removes the need for trust altogether: destination chains can independently check that a message from a source chain is authentic, final, and unaltered.
The Building Blocks: Recent Innovations in Proof-Based Settlement
The last year has seen major breakthroughs in this area. Let’s break down some of the most impactful developments:
Key Proof-Based Cross-Chain Projects Shaping Security
-
ERC-7965: This Ethereum standard introduces proof-based broadcast semantics for cross-chain messaging. It enables destination chains to independently verify messages using cryptographic proofs of the source chain’s state, eliminating the need for trusted intermediaries. Learn more
-
V-ZOR: V-ZOR leverages zero-knowledge proofs (ZKPs) and quantum-driven randomness to secure cross-chain communications. Each oracle packet includes a Halo 2 proof, and quantum entropy ensures unpredictable and secure reporter selection. Read the research
-

zkBridge: zkBridge offers trustless cross-chain bridging using succinct cryptographic proofs. It demonstrated practical performance between Cosmos and Ethereum, with fast proof generation and low on-chain verification costs. Explore zkBridge
-
Wormhole: Wormhole is a decentralized cross-chain messaging protocol powered by its Guardian Network. While it currently relies on trusted validators, upcoming upgrades aim to integrate zero-knowledge proofs for enhanced trustless verification. Wormhole overview
-

Rosen Bridge: Rosen Bridge uses a distributed network of watchers and guards to securely facilitate inter-chain settlements. Watchers monitor events, while guards verify and execute settlements, ensuring transparent and secure cross-chain payments. See how Rosen Bridge works
ERC-7965 introduces standardized semantics for broadcasting messages across chains. Instead of relying on off-chain relayers or trusted witnesses, messages are committed on source chains in verifiable ways, destination chains can then check these commitments using cryptographic proofs (see full EIP). This enables truly trustless cross-chain communication.
V-ZOR takes things even further by combining zero-knowledge proofs with quantum-grade randomness. Each oracle packet includes a Halo 2 proof to verify data aggregation integrity and uses verifiable quantum entropy for random selection of reporters, a clever way to prevent predictable committee attacks (read more here).
zkBridge, meanwhile, has demonstrated practical trustless bridging between Cosmos and Ethereum using succinct ZKPs. Proofs are generated in under 20 seconds and verified on-chain for less than 230,000 gas, a significant leap forward in both speed and cost (details here). And while Wormhole‘s current Guardian Network still relies on professional validators running full nodes across supported chains, their roadmap includes integrating ZKPs for even stronger trust assumptions.
Tackling Security Fragmentation with Unified Policy Frameworks
The proliferation of bridges has led to what some call security fragmentation: each protocol implements its own risk policies and verification logic. This patchwork makes it hard for users and developers to assess risk consistently across ecosystems, and creates opportunities for attackers to exploit overlooked gaps.
A unified policy framework built atop proof-based settlement could change all that. By standardizing how messages are verified (using cryptographic proofs), we can create an interoperable foundation where security guarantees are clear and consistent, no matter which chains or bridges you use.
Imagine a world where every cross-chain transaction is subject to the same rigorous, automated security checks, regardless of which protocol or bridge you choose. That’s the promise of a unified policy framework powered by proof-based settlement. Standardized verification logic means less room for human error, fewer blind spots for attackers, and a more predictable risk profile for everyone, from developers to institutional users.
Projects like ERC-7965 and the emerging xRWA framework are already paving the way here. By defining how cross-chain messages must be committed and proven on source chains, these standards make it easier to enforce shared security policies and automate risk scanning across disparate ecosystems. This isn’t just theory: with ERC-7965, smart contracts can programmatically reject any message that doesn’t meet cryptographic proof requirements, closing off entire classes of exploits before they even start.
Risk Mitigation in Practice: What Proof-Based Settlement Changes
The move to proof-based settlement fundamentally shifts how we think about cross-chain risk mitigation. Instead of auditing each bridge’s validator set or worrying about collusion among third parties, users and protocols can focus on the strength of the underlying cryptographic proofs. This dramatically reduces reliance on social trust, one of the weakest links in blockchain security.
For example: If an attacker tries to spoof a message from Ethereum to another chain but cannot generate a valid ZKP or light client proof, the destination chain will automatically reject the transaction. There’s no need for manual intervention or subjective judgment calls. The rules are clear, verifiable, and enforced by math, not by people.
This also has positive implications for compliance and regulatory clarity. With standardized proof requirements, it becomes much easier to demonstrate that your protocol adheres to best practices, whether you’re building a DeFi app or managing institutional flows across chains.
Challenges Ahead: Scaling Proofs and UX Tradeoffs
No technology is perfect out of the box. While proof-based settlement offers huge improvements in security and decentralization, there are still hurdles to overcome:
- Proof generation costs: Although advances like Halo 2 and succinct ZKPs have reduced overhead, generating complex proofs can still be resource-intensive, especially for high-frequency messaging protocols.
- User experience: Waiting 10, 20 seconds for a ZKP might be acceptable for large transactions but could frustrate users accustomed to near-instant bridge transfers.
- Evolving standards: As more protocols adopt proof-based models (and as quantum-resistant cryptography matures), developers must stay nimble to integrate new standards without fragmenting UX further.
The Road Ahead: Toward Interoperable and Secure Blockchain Networks
The trajectory is clear: as bridges migrate from trust-minimized models toward fully trustless verification via proofs, we’ll see fewer catastrophic exploits and more robust interoperability between chains. The days when a single compromised validator could drain millions from a bridge may soon be behind us.
The next wave will likely feature even tighter integration between settlement layers and application logic, think intent-centric protocols where user actions are encoded as proofs themselves (ERC-7965, ERC7683). This not only boosts security but also unlocks new UX possibilities: composable DeFi across rollups, seamless NFT transfers between ecosystems, programmable privacy controls at every step.
If you’re building in this space, or just moving assets between chains, the message is clear: get familiar with proof-based settlement now. It’s quickly becoming table stakes for secure interoperability in Web3.






