Cross-chain bridges are the lifeblood of blockchain interoperability, letting users and assets flow between networks like Ethereum, Solana, and BNB Chain. But with great power comes great risk: in the past two years alone, cross-chain bridge hacks have accounted for over $2.5 billion in losses, according to Cointelegraph. Why do these protocols keep landing in the hacker crosshairs? The answer lies in a series of technical vulnerabilities unique to bridging infrastructure, each one a potential billion-dollar ATM for attackers.

The Anatomy of Cross-Chain Bridge Risk
If you’ve spent any time in DeFi, you know bridge exploits are more than just headlines, they’re existential threats to entire ecosystems. Let’s break down the seven most critical vulnerabilities plaguing cross-chain bridges today, drawing on real-world exploits and current market research.
7 Key Cross-Chain Bridge Vulnerabilities
-

Compromised or Poorly Managed Validator/Relayer Keys: Attackers often target validator or relayer keys, as seen in the Ronin Bridge hack, where compromised private keys led to a $600 million theft. Robust key management is critical for bridge security.
-

Smart Contract Logic Flaws and Unaudited Code: Vulnerabilities in smart contract code, such as the bug exploited in the Wormhole Bridge exploit, can allow attackers to mint or steal assets. Regular audits and code reviews are essential.
-

Centralized Control and Single Point of Failure in Bridge Governance: Bridges with centralized governance or a small set of controlling parties are at higher risk. If these entities are compromised, the entire bridge can be attacked, undermining user trust and security.
-

Unsafe or Unverified Cross-Chain Message Passing: Insecure message validation between chains can enable attackers to forge or replay messages, leading to unauthorized asset transfers. Rigorous verification mechanisms are a must.
-
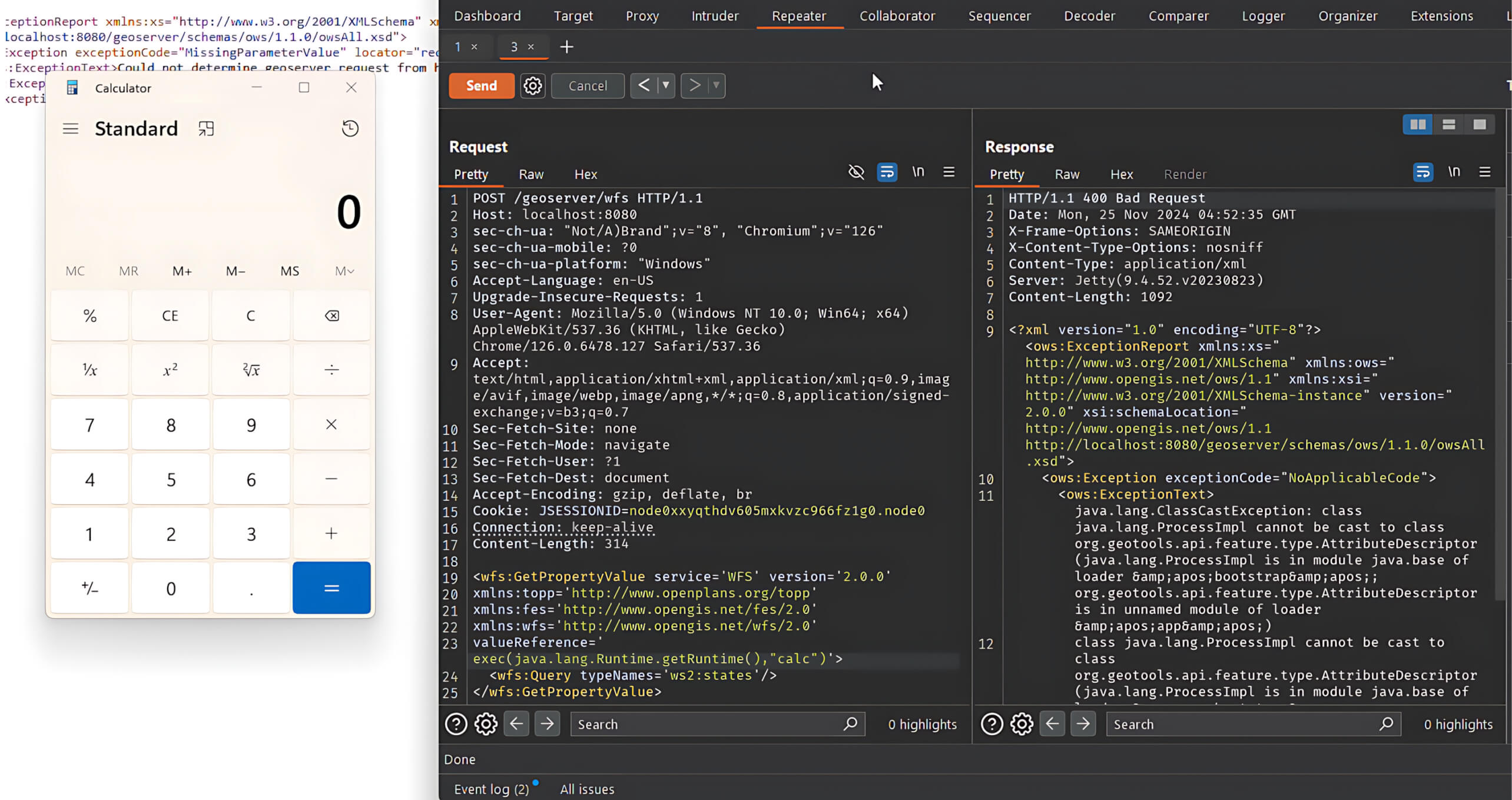
Flawed Upgradability Mechanisms Allowing Malicious Code Injection: Bridges with unsafe upgrade processes can be exploited by attackers to inject malicious code, potentially taking control of bridge assets or operations.
-

Inadequate Replay Protection Across Chains: Without proper replay protection, valid messages or transactions can be maliciously repeated on other chains, draining funds or causing double-spend scenarios.
-

Insufficient Monitoring and Incident Response for Real-Time Exploits: A lack of real-time monitoring and slow incident response can allow attackers to maximize damage before detection, as seen in several high-profile bridge exploits.
1. Compromised or Poorly Managed Validator/Relayer Keys
This is the Achilles’ heel of many bridges. Validator or relayer nodes sign off on transfers between chains; if their private keys are leaked or mismanaged, attackers gain god-mode access. The Ronin Bridge hack ($600 million lost) was a textbook case: attackers compromised validator keys and siphoned funds without resistance. Robust key management, using hardware security modules (HSMs), multisig schemes, and distributed validator sets, is now non-negotiable for any serious protocol.
2. Smart Contract Logic Flaws and Unaudited Code
Smart contract bugs are silent killers. In February 2022, Wormhole lost $326 million due to a flaw in its signature verification logic, no code review, no safety net. Many bridges rush updates or launch unaudited code to keep up with market demand, but this opens doors for reentrancy attacks, improper access controls, and logic errors that hackers can exploit instantly. Regular audits by reputable firms are essential, but even then, vigilance is key as new exploits emerge daily.
3. Centralized Control and Single Point of Failure in Bridge Governance
The promise of decentralization falls flat if a handful of admins can pause or upgrade your bridge, or worse, if governance is controlled by one entity or multisig wallet. Attackers target these choke points; once breached, they can drain funds at will or push malicious upgrades unnoticed. Bridges must distribute control among diverse stakeholders and avoid single points of failure wherever possible.
4. Unsafe or Unverified Cross-Chain Message Passing
The magic behind bridging is message passing between chains, but if messages aren’t properly validated (think replay attacks or spoofed messages), attackers can mint fake tokens or trigger unauthorized withdrawals across networks. This attack vector often flies under the radar during audits but has been exploited repeatedly in high-profile hacks.
If you want to go deeper into why these specific vectors matter, and how they’ve been exploited historically, check out our deep dive: Why Cross-Chain Bridges Get Hacked: Common Attack Vectors and How to Mitigate Them.
5. Flawed Upgradability Mechanisms Allowing Malicious Code Injection
Upgradability is a double-edged sword for cross-chain bridges. While it enables protocols to patch bugs and adapt quickly, poorly designed upgrade mechanisms can open the door for catastrophic exploits. If an attacker or rogue admin can sneak in malicious code during an upgrade, they can instantly seize control of bridge assets. The Nomad Bridge attack ($190 million lost) highlighted the risks of hasty or insecure contract initialization and upgrades. Best practices now demand multi-step governance, time-locked upgrades, and public transparency to prevent stealthy code changes.
6. Inadequate Replay Protection Across Chains
Replay attacks occur when a valid transaction on one chain is maliciously repeated on another chain due to insufficient safeguards. Without robust replay protection, attackers can duplicate legitimate transfers or messages, draining funds or minting unbacked tokens across networks. This subtle but devastating vector is often overlooked in bridge design and has been implicated in several recent exploits. Protocols must implement unique transaction identifiers and strict message validation logic to lock this door tight.
7. Insufficient Monitoring and Incident Response for Real-Time Exploits
Time is money, especially when millions are at stake. Many bridges lack real-time monitoring tools or incident response plans, allowing attackers to drain funds over hours (or even days) before defenders react. The aftermath? Massive losses and shattered user trust. Modern mitigations include automated anomaly detection systems, 24/7 monitoring dashboards, and pre-planned emergency procedures that freeze bridge operations at the first sign of trouble.
Modern Mitigations: Building Resilient Cross-Chain Bridges
The DeFi community isn’t sitting still, bridge builders are deploying new layers of defense to counter these high-stakes threats:
Modern Mitigations for Key Cross-Chain Bridge Vulnerabilities
-

Compromised or Poorly Managed Validator/Relayer Keys: Adopt robust key management solutions like AWS CloudHSM or Fireblocks, and implement multi-signature schemes (e.g., Gnosis Safe) to secure validator and relayer keys, minimizing single points of compromise.
-
Smart Contract Logic Flaws and Unaudited Code: Mandate comprehensive, ongoing audits by top security firms like ConsenSys Diligence or Trail of Bits, and use automated formal verification tools such as MythX to catch vulnerabilities before deployment.
-
Centralized Control and Single Point of Failure in Bridge Governance: Transition to decentralized validator sets using protocols like Chainlink CCIP or Axelar Network, which distribute governance and validation power to reduce risk.
-
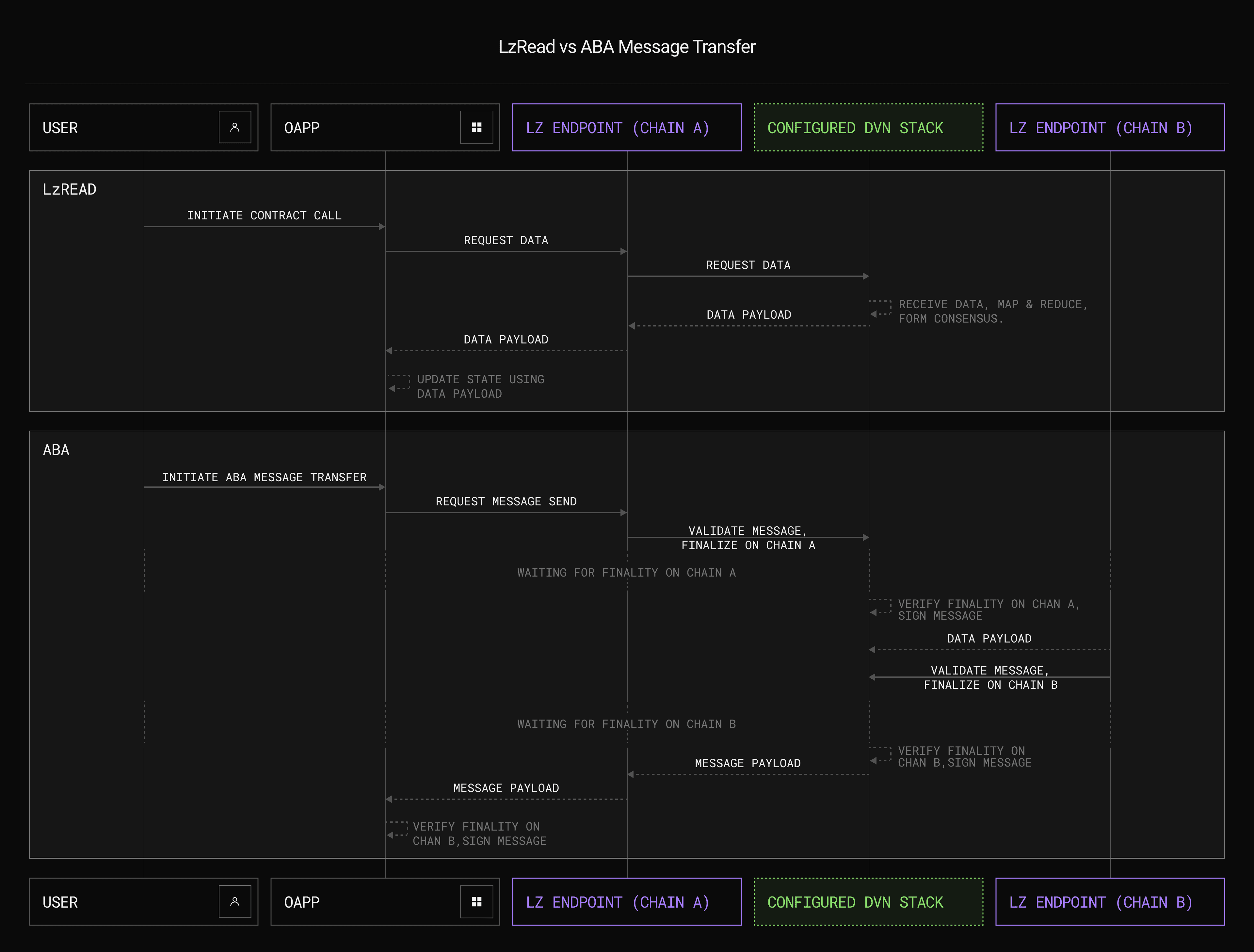
Unsafe or Unverified Cross-Chain Message Passing: Utilize proven message verification standards such as Wormhole’s Guardian Network or LayerZero Ultra Light Node, and enforce strict message authentication and validation on both source and destination chains.
-
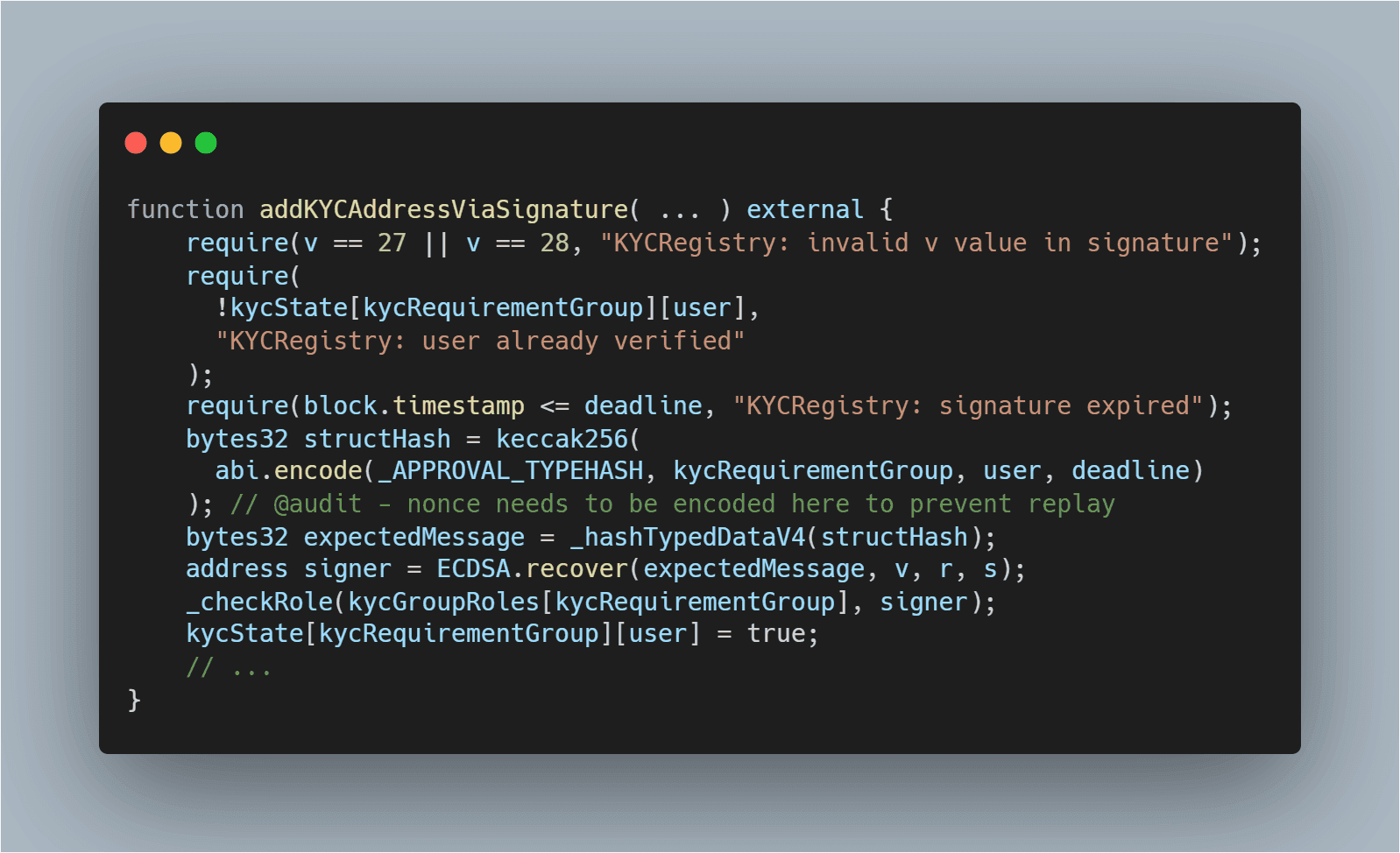
Inadequate Replay Protection Across Chains: Enforce robust replay protection standards such as EIP-1559 and unique nonces for cross-chain transactions, as implemented by bridges like Polygon Bridge and Celer cBridge.
-

Insufficient Monitoring and Incident Response for Real-Time Exploits: Deploy real-time monitoring and anomaly detection with services like CertiK Skynet or Forta Network, enabling rapid detection and automated response to suspicious bridge activity.
From decentralized validator networks that eliminate single points of failure, to continuous smart contract audits, hardware-backed key management, and real-time anomaly detection, the future of cross-chain bridge security is about layered defense and relentless vigilance.
If you’re serious about safeguarding your protocol, or just want to understand what’s under the hood, explore our comprehensive guide: Top Vulnerabilities in Blockchain Bridge and Cross-Chain Messaging. For hands-on risk scanning tools that keep you one step ahead, check out how our platform empowers teams: How to Use Cross-Chain Messaging Risk Scanners for DeFi Protocol Security.
The bottom line? Cross-chain bridges will always be high-value targets, but with transparent governance, robust engineering, proactive monitoring, and a healthy dose of skepticism around every update or message passed between chains, we can turn these billion-dollar ATMs into fortresses instead of honeypots.