
Cross-chain messaging protocols are the connective tissue of decentralized finance, powering asset transfers and data exchange between disparate blockchains. However, this critical infrastructure is also a prime target for sophisticated exploits. With recent attacks draining millions in digital assets from high-profile bridges, the need for precise vulnerability detection and real-time risk scanning has never been more urgent.
Understanding the Attack Surface: Where Cross-Chain Messaging Fails
Cross-chain vulnerabilities often stem from the complex interplay between smart contracts, relayers, and oracles. Bridges rely on these components to validate and relay messages or transactions across chains. If any piece of this puzzle is compromised, whether by flawed contract logic, manipulated oracle data, or unchecked relayer activity, the consequences can be catastrophic. Recent research underscores that attackers frequently exploit semantic inconsistencies in access controls or forge cross-chain messages to bypass verification checks (source).
SmartAxe Framework: Automated Detection of Cross-Chain Vulnerabilities
The SmartAxe framework represents a leap forward in automated vulnerability detection for cross-chain messaging protocols. By employing fine-grained static analysis and constructing detailed control-flow and data-flow graphs across bridge contracts, SmartAxe pinpoints subtle cross-chain contract vulnerabilities (CCVs) that traditional tools often miss.
In rigorous evaluations, SmartAxe achieved 84.95% precision and 89.77% recall, identifying 232 new CCVs impacting digital assets valued at approximately $1.88 million. These figures demonstrate not only the prevalence of exploitable flaws but also the necessity for advanced analytics in safeguarding protocol integrity (source). For developers and auditors aiming to stay ahead of emerging threats, integrating SmartAxe into continuous security workflows is now considered best practice.
Robust State Verification and Continuous Monitoring: Defending Against Relayer/Oracle Attacks
No matter how advanced your vulnerability scanner is, it must be paired with robust operational defenses. Two pillars stand out:
Top Tools & Practices for Cross-Chain Security
-

SmartAxe Framework for Automated Cross-Chain Vulnerability Detection: SmartAxe employs advanced static analysis to uncover cross-chain vulnerabilities in bridge smart contracts. It models access controls and builds cross-chain control/data-flow graphs, achieving 84.95% precision and 89.77% recall in real-world tests—identifying 232 new vulnerabilities affecting assets worth $1.88 million.
-
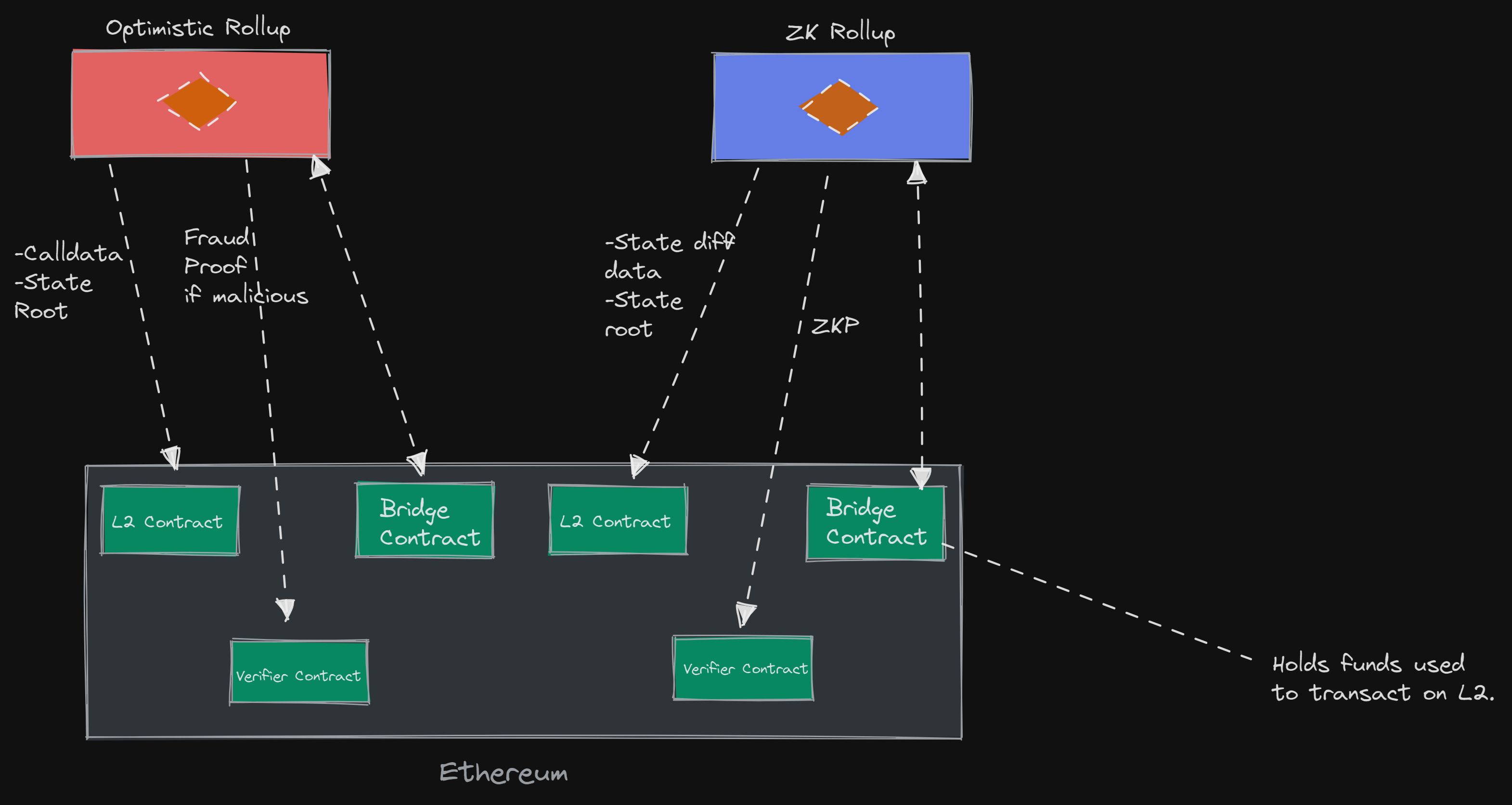
Implement Robust State Verification and Continuous Monitoring of Relayer/Oracle Activity: Enforce strict state verification (e.g., Merkle proof checks) to prevent forged cross-chain messages. Continuously monitor relayer/oracle behaviors using real-time analytics and alerting systems to detect anomalies and respond promptly to suspicious activity, reducing the risk of large-scale exploits.
State verification involves cryptographically validating every message passed between chains, often via Merkle proofs, to ensure that only authentic transactions are executed on the destination chain (source). This process thwarts attempts to inject forged data or replay old transactions, both common tactics in bridge exploits.
Continuous monitoring of relayer/oracle activity is equally critical. Real-time risk scanners can flag suspicious deviations from expected behavior, such as unexpected spikes in transaction volume or inconsistent oracle reports, enabling rapid response before attackers drain funds or disrupt protocol operations.
The Data-Driven Case for Proactive Security Measures
The numbers speak for themselves: as bridges secure ever-larger sums and underpin an expanding multi-chain ecosystem, attackers have more incentive than ever to probe for weaknesses. Automated frameworks like SmartAxe combined with vigilant state verification and monitoring form a comprehensive defense strategy that adapts as new threats emerge.
Security is not a static achievement but an ongoing process. As cross-chain messaging protocols evolve, so do the tools and tactics of adversaries. The SmartAxe framework’s capacity to discover previously unknown vulnerabilities, 232 new CCVs affecting $1.88 million in assets, highlights the scale and urgency of the challenge. Yet, even the most advanced detection engine cannot guarantee safety unless paired with robust operational practices.
Implementing robust state verification ensures that every cross-chain message is cryptographically validated before execution. This method, often leveraging Merkle proofs, is the gold standard for preventing forged messages from slipping through (source). But verification alone is insufficient if relayer or oracle activity goes unchecked. Attackers frequently target these components to manipulate data or bypass controls, making continuous monitoring non-negotiable for any serious DeFi protocol.
Real-time risk scanners that monitor relayer/oracle activity provide actionable intelligence for threat mitigation. By establishing baselines for normal behavior and flagging anomalies, such as sudden spikes in transaction volume or inconsistent oracle responses, protocol teams can respond to threats before they escalate into catastrophic losses.
Integrating Tools and Best Practices: A Blueprint for Cross-Chain Security
The synergy between automated frameworks like SmartAxe and continuous operational defenses forms a resilient security posture. Developers should:
Integration Checklist: SmartAxe & State Verification
-
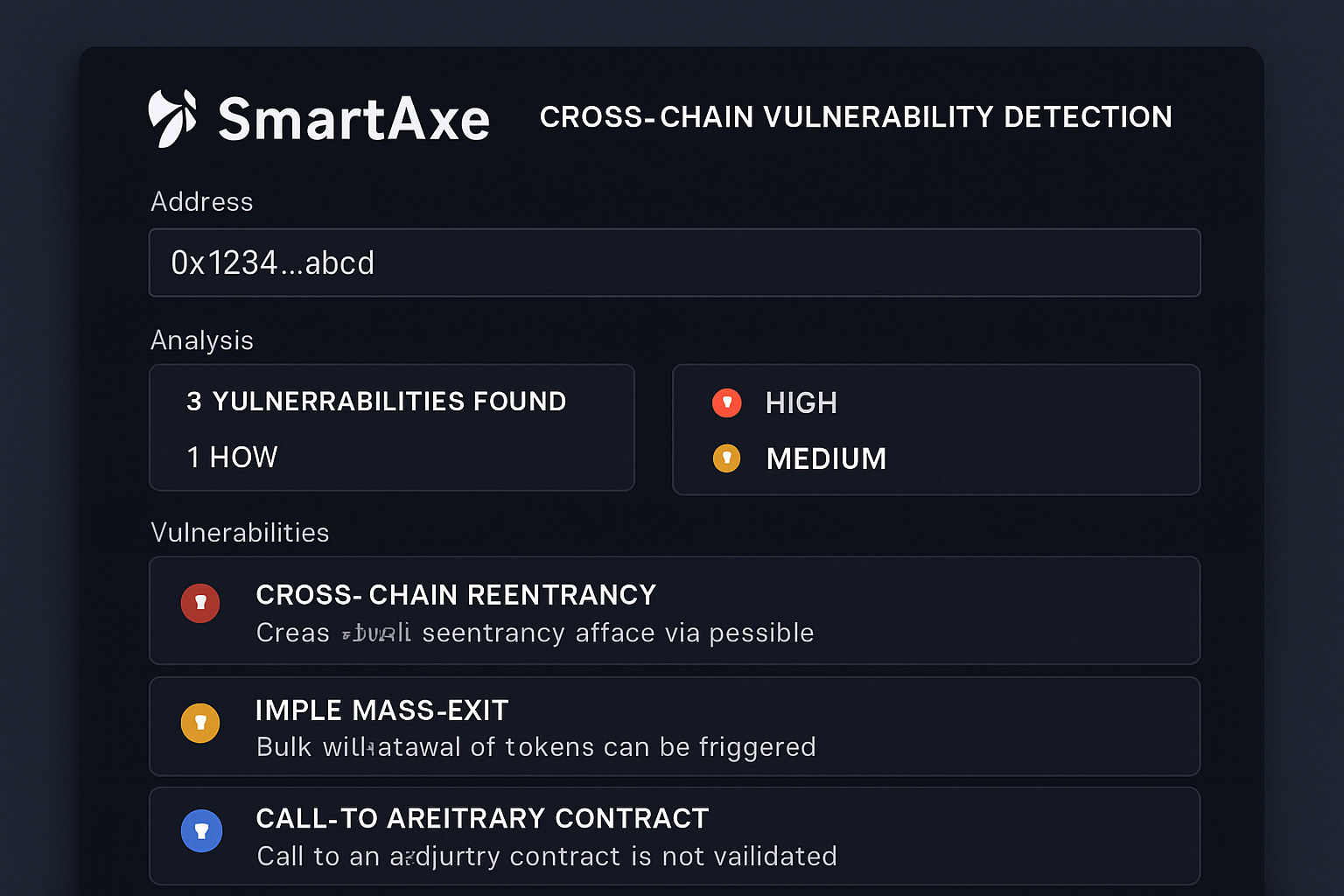
SmartAxe Framework for Automated Cross-Chain Vulnerability Detection: Integrate SmartAxe into your development pipeline to perform fine-grained static analysis of bridge smart contracts. SmartAxe models access control and constructs cross-chain control-flow and data-flow graphs, enabling early detection of semantic inconsistencies and vulnerabilities. In recent evaluations, SmartAxe identified 232 new cross-chain vulnerabilities affecting assets worth approximately $1.88 million, achieving 84.95% precision and 89.77% recall.
-
Implement Robust State Verification and Continuous Monitoring of Relayer/Oracle Activity: Establish rigorous state verification mechanisms—such as validating Merkle proofs from source chains—to prevent forged cross-chain messages. Continuously monitor relayer and oracle activity for anomalies, leveraging decentralized oracle networks and real-time alerting systems to detect and respond to suspicious behaviors. This approach is vital for maintaining the integrity and security of cross-chain messaging protocols.
This approach not only detects vulnerabilities early but also reduces false positives by correlating code-level findings with live operational data. It’s a data-driven feedback loop: static analysis uncovers hidden flaws, while real-time monitoring validates fixes and exposes emergent risks.
The future of blockchain bridge security lies at this intersection of automation and vigilance. As more value flows across chains, proactive adoption of these strategies will be the difference between resilient protocols and headline-grabbing exploits.






