
Cross-chain bridges are the lifelines of blockchain interoperability, enabling assets and data to flow seamlessly between otherwise isolated networks. But with great power comes great risk: over $2.8 billion has been siphoned from DeFi bridges in recent years, representing nearly half of all DeFi hacks. Why do these critical protocols remain such tempting targets? The answer lies in a mix of complex smart contracts, high-value honeypots, and, crucially, a lack of robust, real-time security infrastructure.
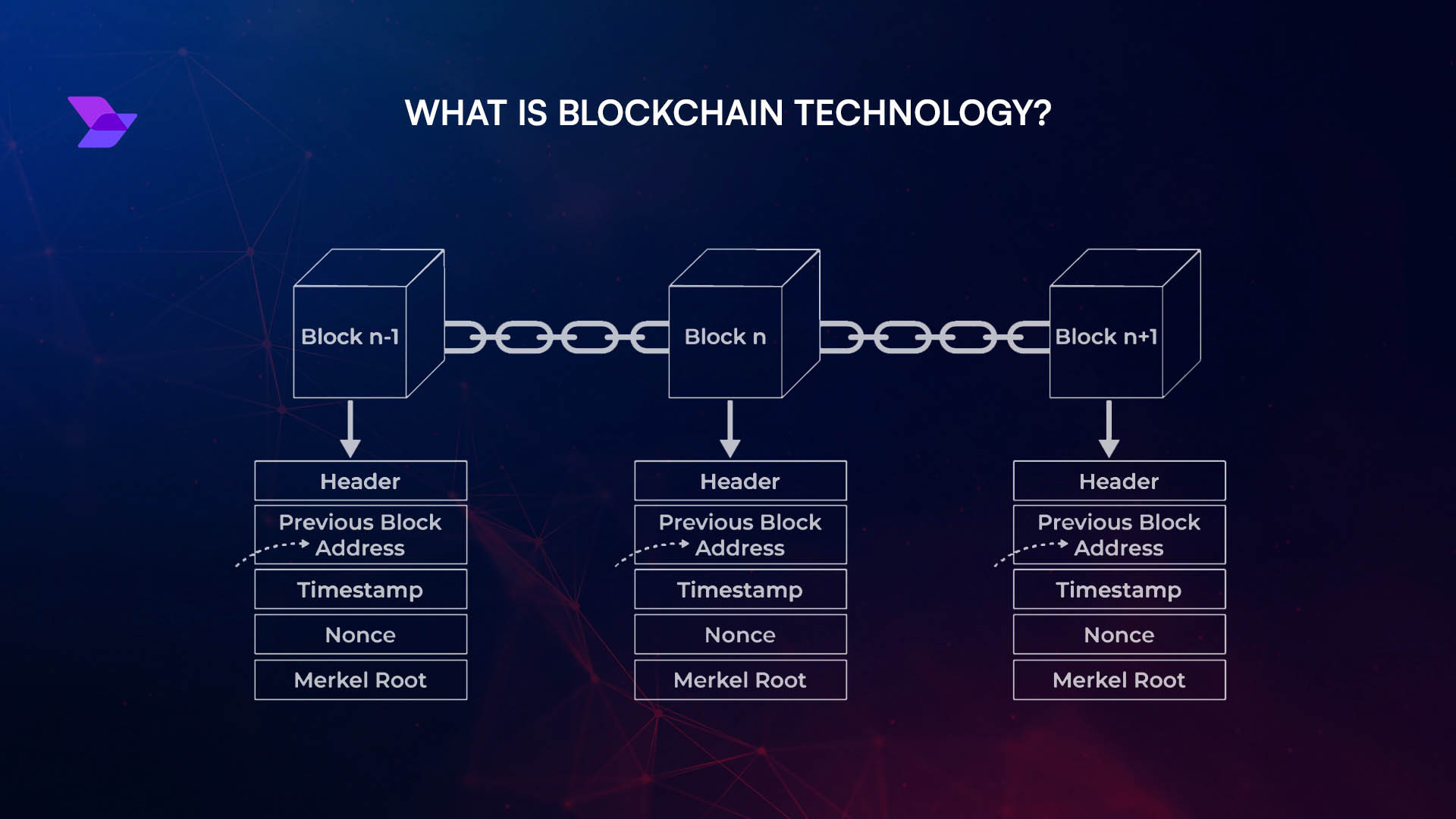
Why Real-Time Bridge Monitoring Is Non-Negotiable
Let’s get straight to the point: real-time bridge monitoring is no longer a luxury but an absolute necessity for cross-chain bridge security. Without active surveillance, suspicious activity can slip through the cracks, sometimes for days. The infamous Ronin Bridge exploit in March 2022 is a case in point: attackers drained hundreds of millions while the breach went undetected for nearly a week. Imagine the difference if automated systems had flagged the anomaly within minutes.
Modern monitoring tools continuously analyze transaction flows across bridges, utilizing anomaly detection algorithms to spot unusual withdrawals, sudden spikes in volume, or out-of-pattern address interactions. These systems can automatically pause or throttle suspicious transfers before they escalate into full-blown exploits.
The goal is simple: catch red flags as they happen, not after funds have vanished.
The Power of Decentralized Validator Networks
If real-time monitoring is your alarm system, then decentralized validators are the reinforced locks on your doors. Many early bridges relied on small groups of trusted parties (or even single multisig wallets) to validate cross-chain transactions, a setup rife with single points of failure and tempting targets for attackers.
Today’s best-in-class protocols distribute validation duties across diverse networks of independent actors. By requiring consensus among multiple validators, often backed by collateral that can be slashed for misbehavior, bridges dramatically reduce risks from collusion or compromise. Transparent validator selection processes and on-chain governance further strengthen this model by making it harder for bad actors to slip through unnoticed.
Top Benefits of Decentralized Validator Networks for Bridge Security
-
Elimination of Single Points of Failure: Decentralized validator networks distribute transaction verification across multiple independent parties, drastically reducing the risk of a single compromised entity causing a catastrophic breach. This approach was notably implemented by Orbit Bridge through its multi-signature authentication system.
-

Enhanced Resistance to Collusion and Attacks: By requiring consensus among diverse validators, decentralized networks make it far more difficult for attackers to collude or manipulate transaction approvals. Chainlink CCIP and Axelar are leading examples using robust, decentralized validator sets.
-
Transparent and Accountable Operations: Decentralized validator selection and on-chain governance, as seen in Axelar and Wormhole, allow communities to monitor validator behavior and enforce accountability, increasing trust and transparency.
-
Incentivized Honest Behavior via Staking: Validators are often required to stake collateral that can be slashed for malicious actions, aligning their incentives with network security. Chainlink and Wormhole utilize staking and slashing mechanisms to promote honest participation.
-

Rapid Detection and Response to Threats: Decentralized validator networks can integrate real-time monitoring tools, such as Hacken Extractor, to collectively detect and react to anomalies or suspicious activity, minimizing the window for potential exploits.
Anatomy of a Modern Cross-Chain Attack, and How New Defenses Stack Up
Let’s break down what typically goes wrong when a bridge gets hacked:
- A vulnerability (like a buggy contract or compromised validator key) is exploited
- Large sums are withdrawn or minted illicitly
- Lack of real-time detection allows attackers ample time to cover their tracks
- The bridge operator discovers the hack only after users report missing funds
This cycle repeats because many bridges still lack both advanced monitoring and robust validator decentralization. However, recent case studies show that integrating these two elements can break the chain:
- Anomaly detection systems instantly flag abnormal withdrawals or transaction patterns
- Automated rate limiting and pausing mechanisms halt suspicious activity before more damage occurs (Chainlink Education Hub)
- Diverse validator sets with slashing incentives deter collusion and internal compromise (Chainlink Education Hub)
- Transparent governance protocols make it easier to audit and upgrade security practices over time
These layered defenses are already making a measurable impact. Protocols that combine automated, real-time bridge monitoring with decentralized validator networks have seen faster incident response times and lower rates of catastrophic loss. The numbers speak for themselves: while bridges without these safeguards continue to suffer multi-million dollar exploits, those with robust monitoring and diverse validator sets are far less likely to make headlines for the wrong reasons.
But the arms race isn’t over. Attackers constantly probe for new weaknesses, from social engineering validator operators to exploiting obscure smart contract logic. That’s why leading teams are doubling down on adaptive security, rolling out machine learning models to spot never-before-seen anomalies, and expanding validator pools to further dilute risk.
Emerging Best Practices for Cross-Chain Risk Mitigation
For developers and DeFi users alike, there’s a growing checklist of must-haves when evaluating or building cross-chain bridges:
Top Best Practices for Cross-Chain Bridge Security
-
Implement Real-Time Monitoring Systems: Deploy active transaction monitoring tools, such as Hacken Extractor or Chainlink Monitoring Solutions, to detect and respond to suspicious activities instantly. These platforms help spot anomalies like large, unexpected withdrawals or unusual transaction patterns, enabling rapid intervention.
-
Adopt Decentralized Validator Architectures: Use decentralized validator sets, as seen in Across Protocol and Orbit Bridge, to distribute transaction approval among multiple independent parties. This reduces single points of failure and mitigates the risk of validator collusion or compromise.
-
Enforce Rate Limiting and Withdrawal Caps: Set daily and per-transaction withdrawal limits, similar to the approach used by Wormhole, to slow down potential exploit attempts and limit the impact of successful attacks. Automated rate limiting can buy critical time for incident response teams.
-
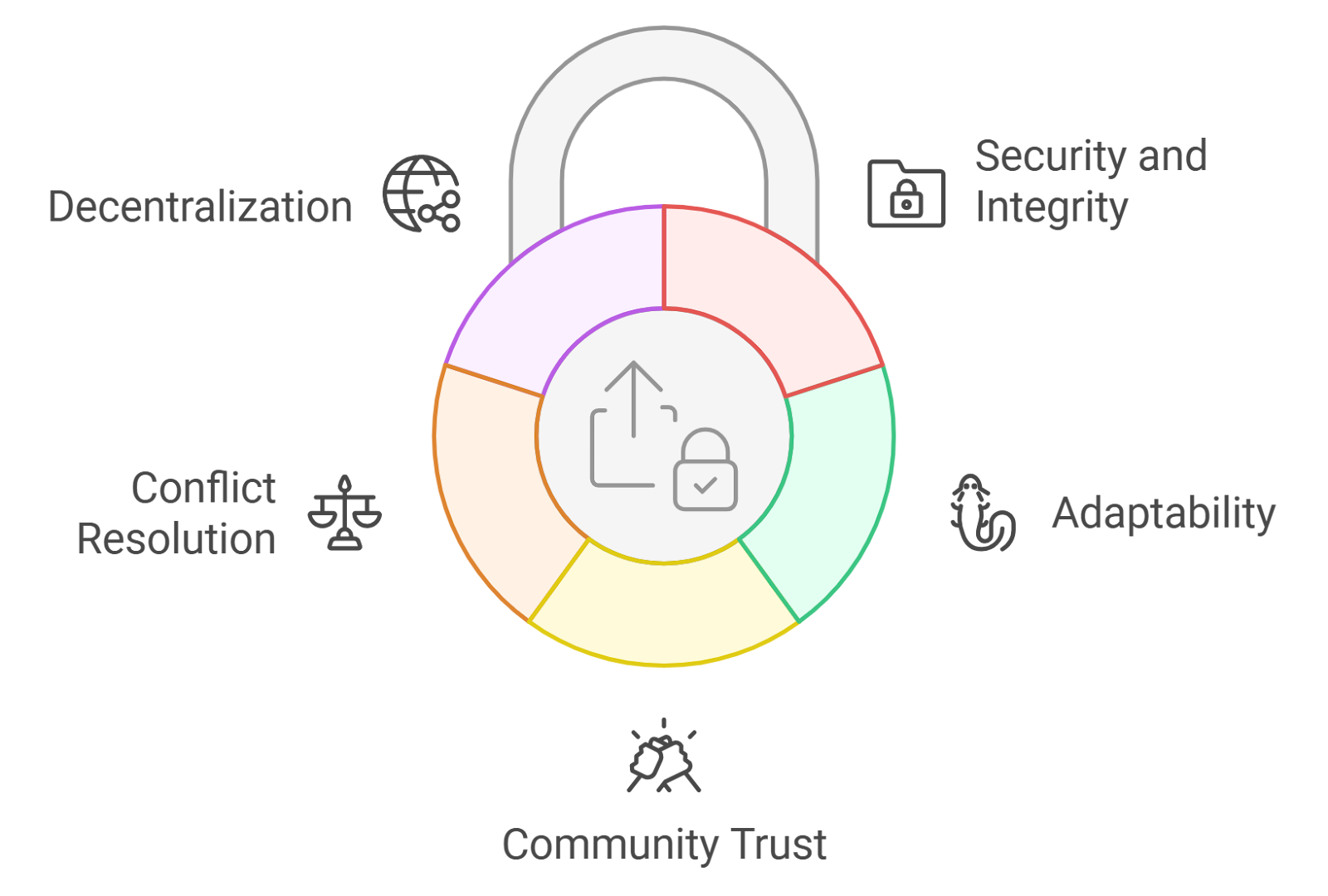
Ensure Transparent and On-Chain Governance: Implement transparent governance frameworks, as practiced by Synapse Protocol, where validator selection, protocol upgrades, and emergency actions are managed via on-chain proposals and community voting. This transparency builds trust and accountability among bridge users.
-

Require Validator Staking and Slashing Mechanisms: Mandate that validators stake collateral, which can be slashed for malicious or negligent behavior. Chainlink and Across Protocol both utilize staking and slashing to incentivize honest participation and deter attacks.
Another crucial step is ongoing stress testing. Simulated attack drills, sometimes called “red teaming”: help teams identify blind spots before real attackers do. And as more bridges adopt open-source codebases and public bug bounty programs, the community itself becomes an additional layer of defense.
The future of cross-chain bridge security relies on proactive collaboration between builders, auditors, white-hat hackers, and users.
What’s Next? Smarter Bridges in a Multi-Chain World
The next generation of cross-chain infrastructure will be defined by its ability to react in real time and adapt under pressure. Expect smarter anomaly detection powered by AI, more transparent on-chain governance systems, and validator networks that span multiple geographies and jurisdictions. These enhancements won’t just reduce risk, they’ll build trust in the entire DeFi ecosystem.
As interoperability grows more complex and valuable assets flow across chains every second, the stakes have never been higher. But with vigilant monitoring and truly decentralized security models in place, we can turn volatility into opportunity, rather than vulnerability.







