In the rapidly evolving landscape of decentralized finance (DeFi), the need for robust security across blockchain bridges and cross-chain messaging protocols has never been more acute. As DeFi platforms increasingly leverage cross-chain interoperability to unlock new opportunities, they also expose themselves to a growing array of sophisticated threats. Cross-chain messaging risk scanners have emerged as indispensable tools for developers and security researchers aiming to safeguard assets, maintain protocol integrity, and build user trust.
Why Cross-Chain Messaging Risk Scanners Are Critical for DeFi Protocol Security
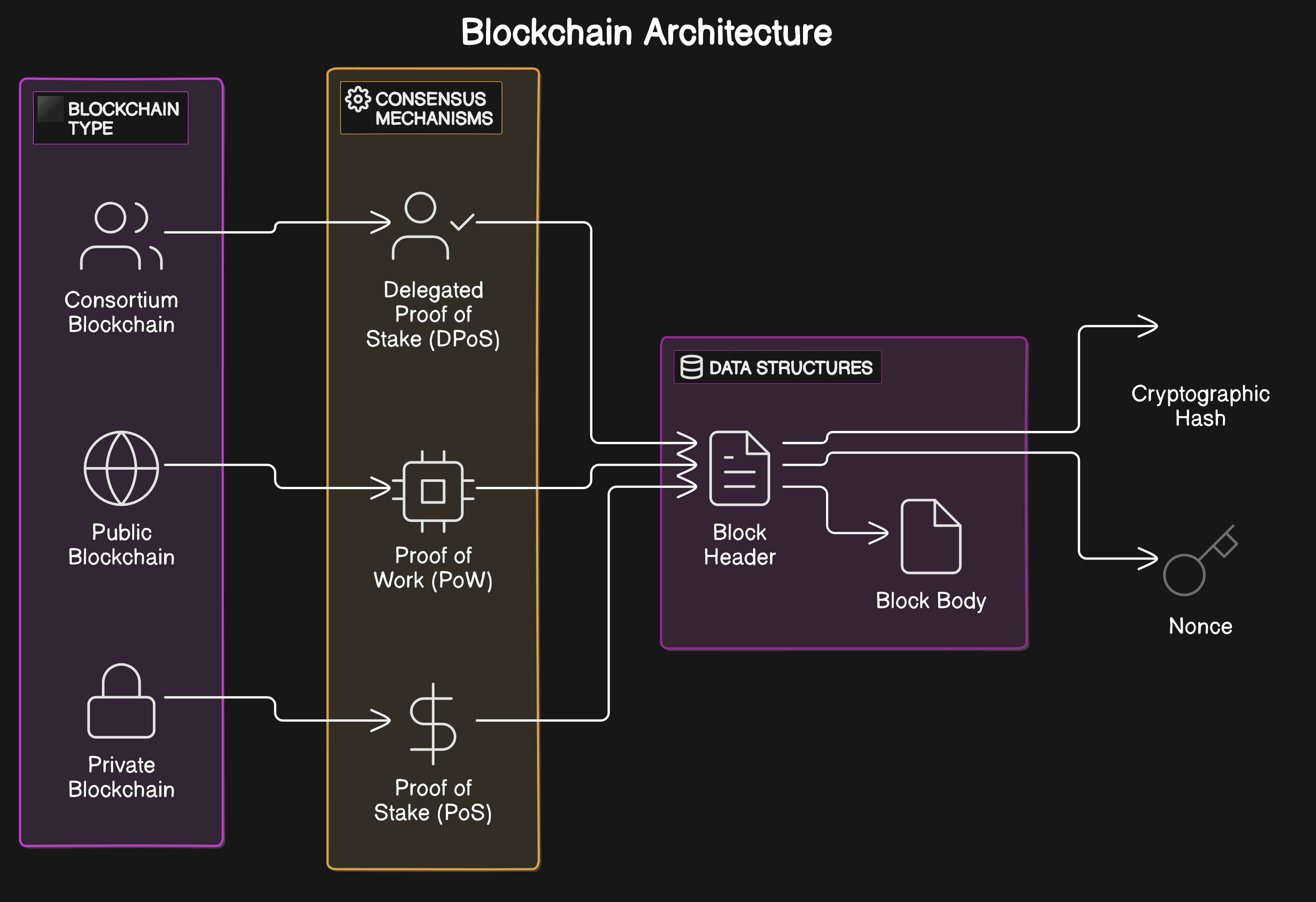
Cross-chain bridges are the connective tissue enabling seamless asset transfers and data sharing between blockchains like Ethereum, Binance Smart Chain, and Polygon. However, these bridges are prime targets for attackers. High-profile exploits such as the Ronin Bridge hack ($600 million lost) and Wormhole Bridge breach ($320 million lost) highlight just how devastating vulnerabilities in cross-chain infrastructure can be. Attackers often exploit weaknesses in signature verification or validator node security, resulting in catastrophic financial damage. (Cointelegraph, Blockchaindefenders.com)
Traditional smart contract audits are not sufficient when assets and data move across multiple chains. That’s where real-time cross-chain risk analysis comes in. By continuously scanning for anomalies, replay attacks, improper access controls, or unusual token flows, these scanners provide a proactive defense against emerging threats.
Key Features Powering Modern Cross-Chain Messaging Risk Scanners
Top 5 Must-Have Features in Cross-Chain Messaging Risk Scanners
-
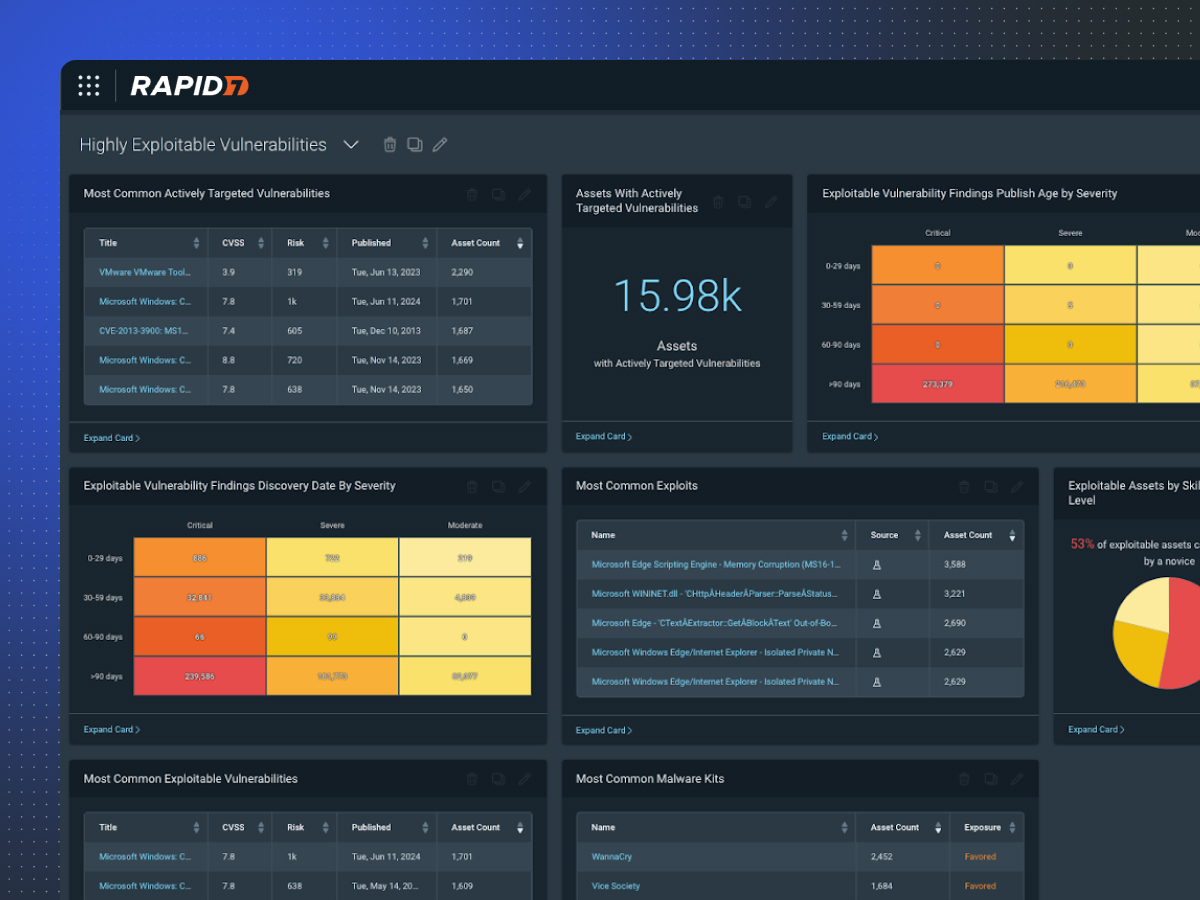
Comprehensive Vulnerability Scanning: Leading scanners like Cross-Chain Security Analyzer automatically analyze smart contracts across multiple blockchains (e.g., Ethereum, BNB Chain, Polygon) to detect vulnerabilities such as re-entrancy and access control flaws.
-

Real-Time Monitoring and Alerts: Tools such as Cross-Chain Security Analyzer provide continuous monitoring of cross-chain transactions, instantly flagging anomalies like abnormal token flows or duplicated transaction hashes for immediate response.
-
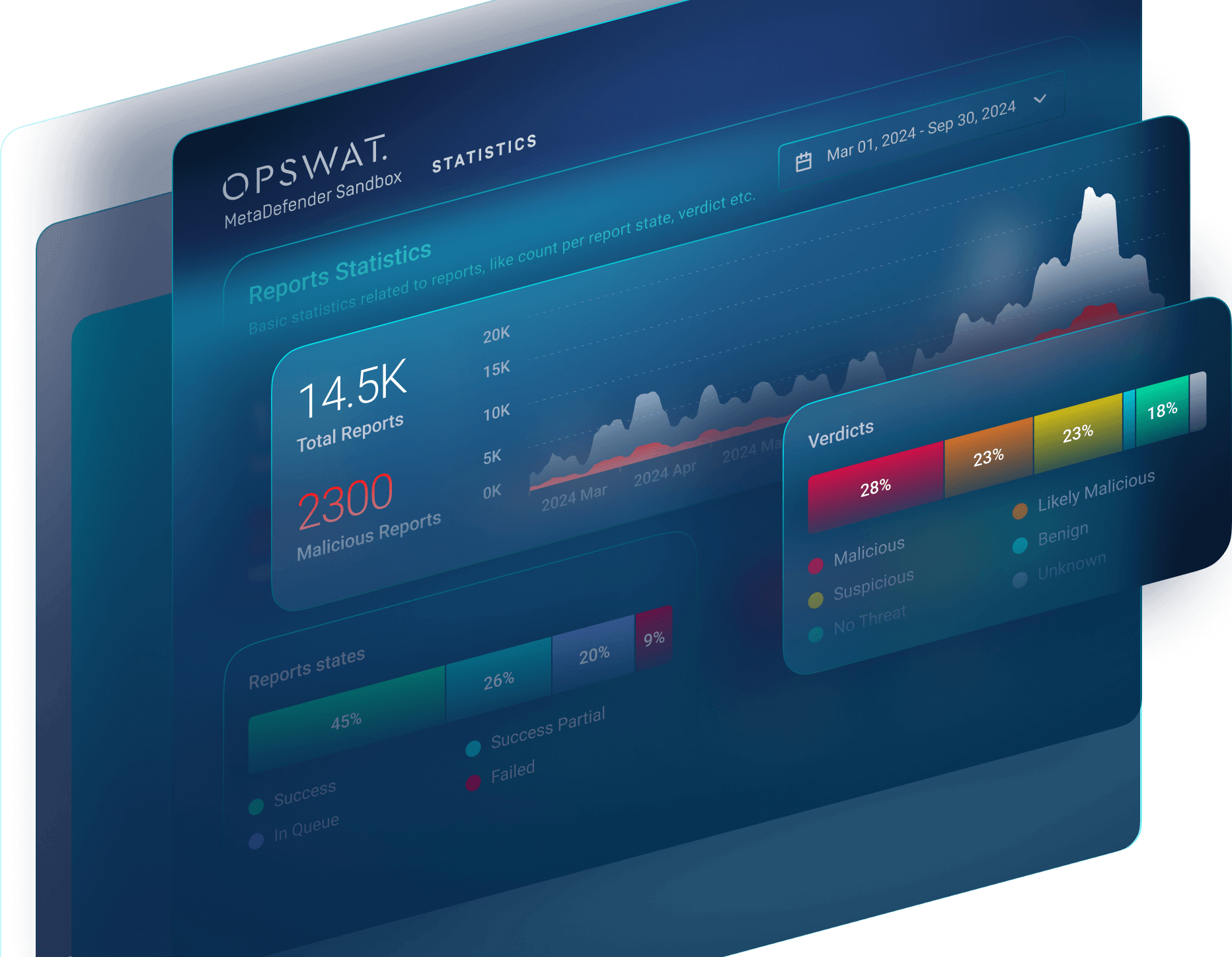
Replay Attack Detection: Advanced scanners compare transaction hashes and payloads across different chains to identify replay attacks, ensuring that malicious transaction duplication is quickly detected and mitigated.
-
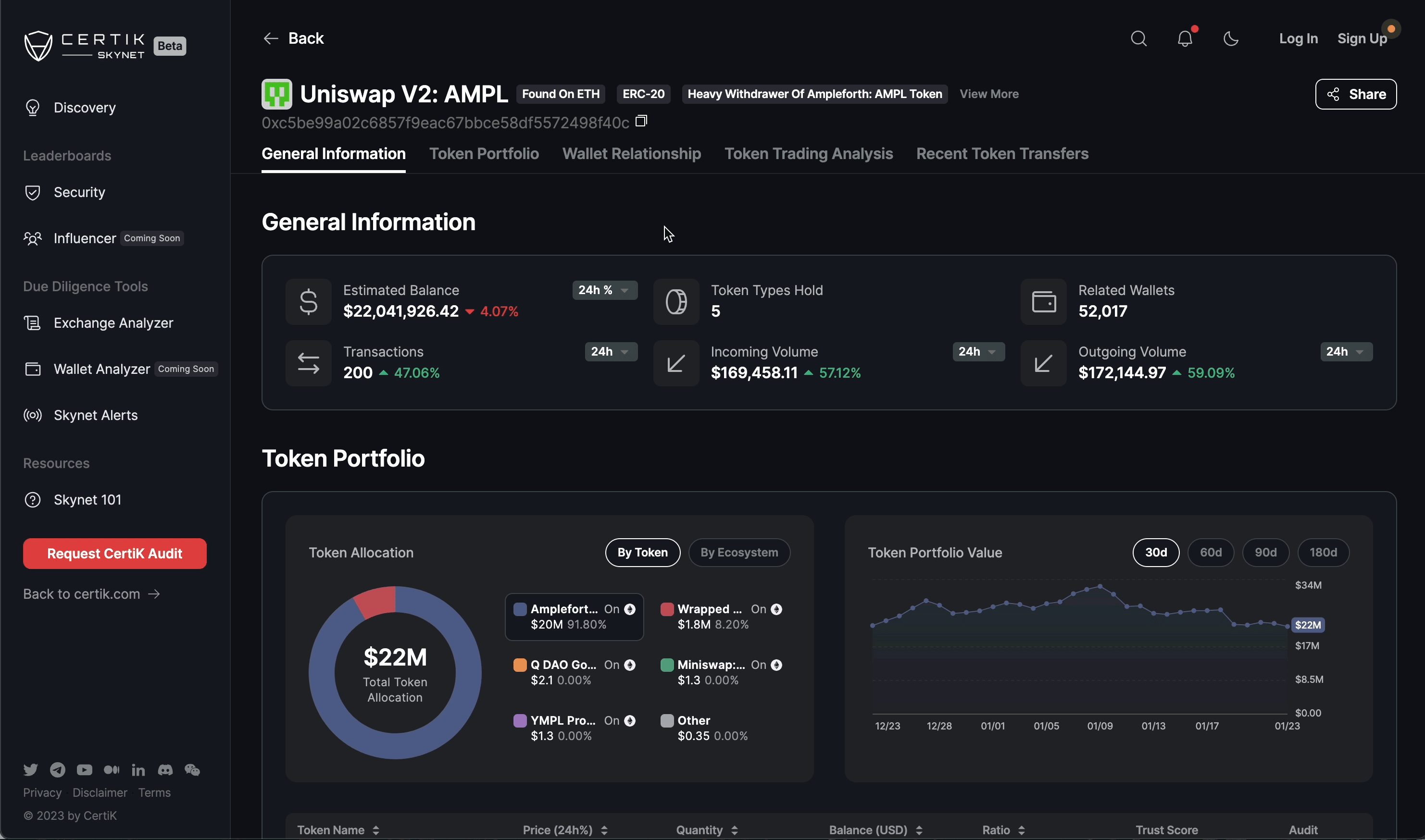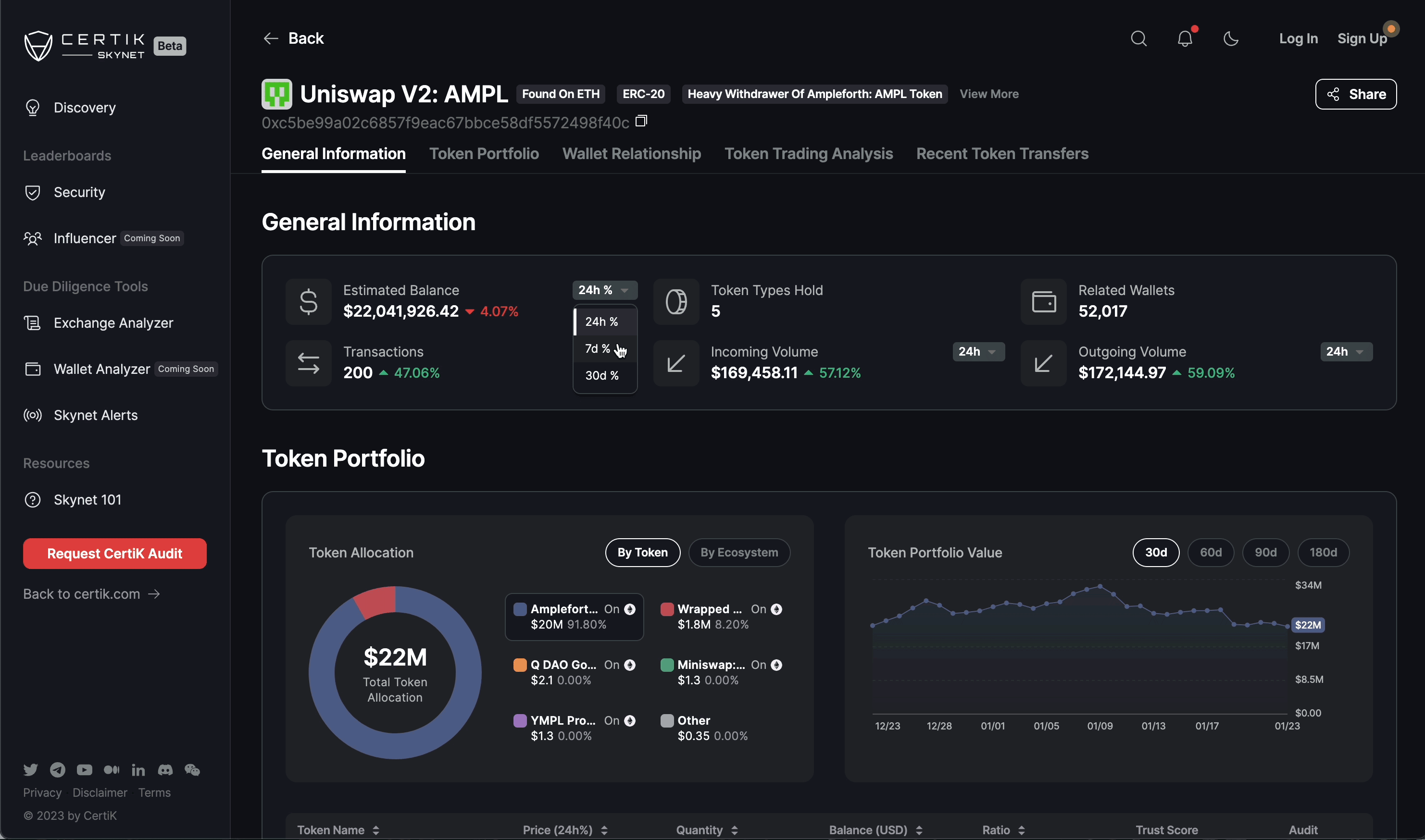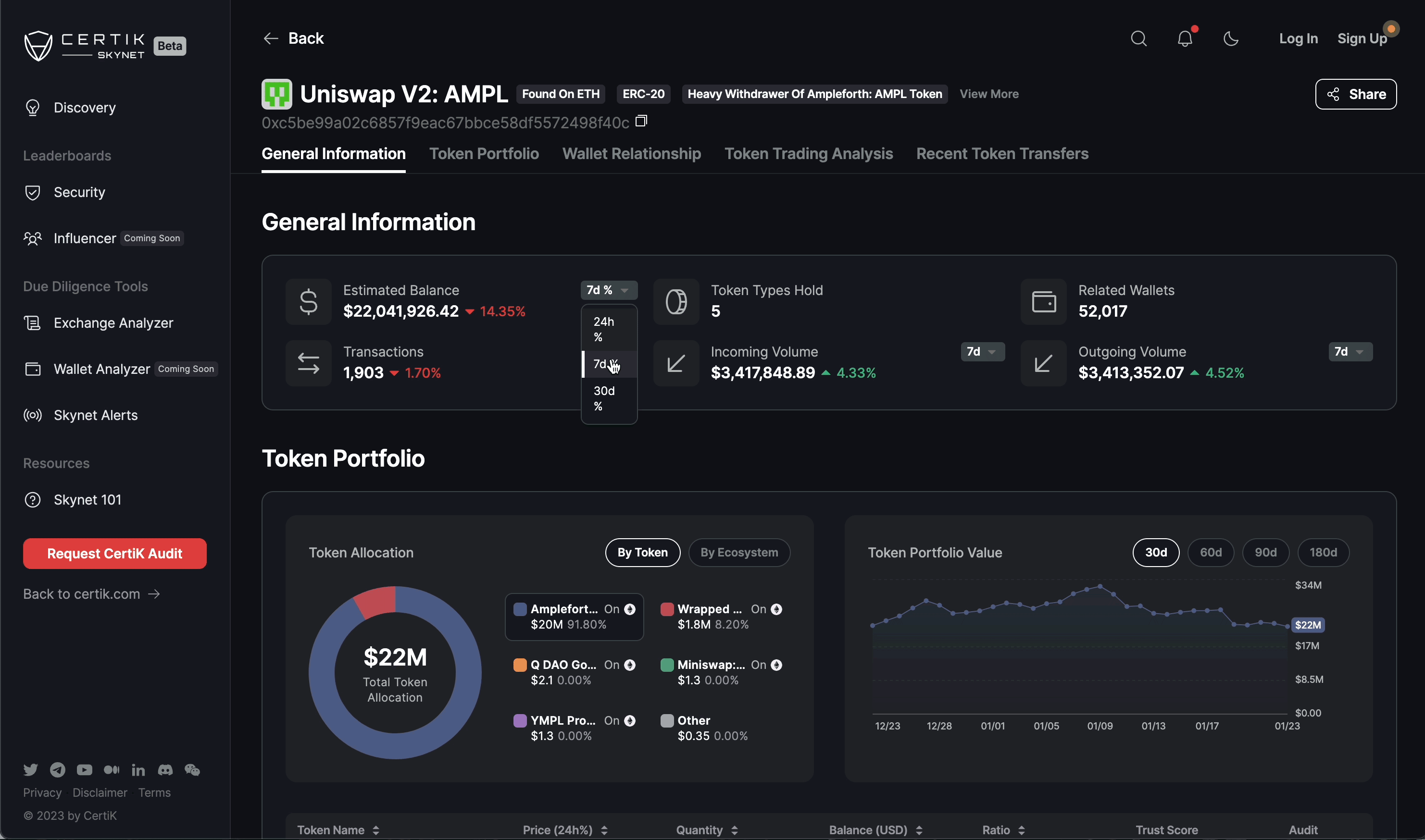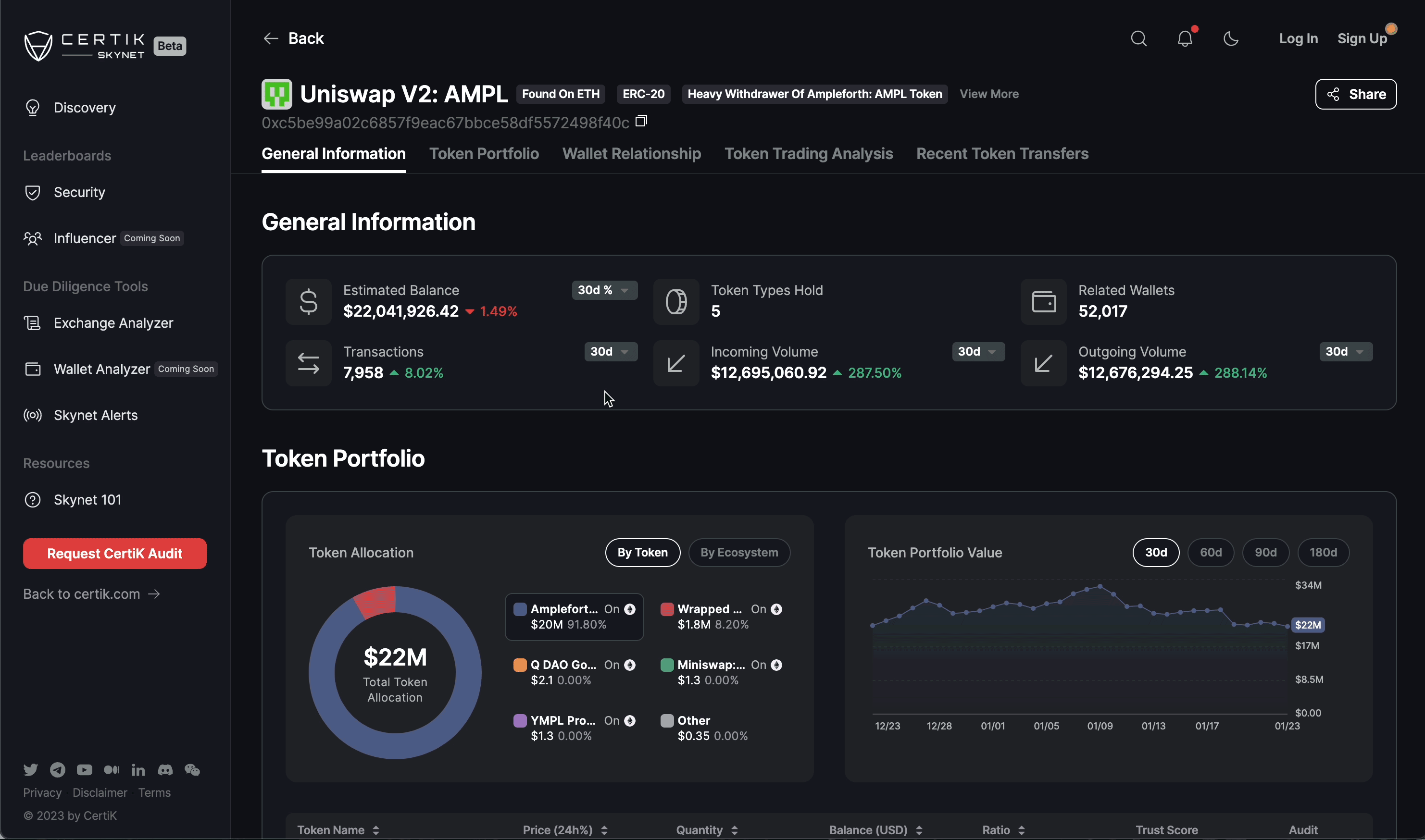
Risk Scoring System: Platforms assign dynamic risk scores to smart contracts and transactions using factors like transaction value, code complexity, and historical security incidents, helping teams prioritize remediation efforts.
-

Multi-Chain Integration Support: Top scanners support seamless integration with major blockchains (Ethereum, BNB Chain, Polygon, Avalanche, etc.), ensuring broad coverage and unified risk assessment across DeFi ecosystems.
The most effective risk scanners go far beyond basic vulnerability checks. Here’s what sets them apart:
- Comprehensive Vulnerability Scanning: Automated tools analyze smart contracts deployed across multiple blockchains to detect classic issues like re-entrancy bugs or faulty access controls.
- Real-Time Monitoring and Alerts: Continuous surveillance of cross-chain transactions enables instant detection of anomalies – from duplicated transaction hashes to suspiciously large token movements.
- Replay Attack Detection: By comparing payloads and hashes across chains, scanners can spot if a single transaction is maliciously replayed on different networks.
- Risk Scoring System: Assigning dynamic risk scores based on transaction value, contract history, and known attack vectors helps prioritize responses.
- Integration with Threat Intelligence Feeds: Keeping scanners updated with the latest exploit signatures ensures rapid identification of new vulnerabilities as they emerge.
This layered approach is essential given the scale and complexity of modern DeFi ecosystems. According to recent research (blockchaindefenders.com), continuous testing and monitoring are now considered best practices for any protocol relying on cross-chain infrastructure.
A Step-by-Step Approach: Implementing Risk Scanners in Your DeFi Workflow
The path to enhanced protocol security starts with strategic integration:
- Integrate Early: Add your chosen scanner during both development and deployment phases to catch vulnerabilities before launch.
- Tune Configuration: Customize monitoring rules for your specific bridges or protocols – whether you’re using Relay Protocol or building custom solutions (relay.link).
- Pursue Continuous Monitoring: Regularly review alerts and reports; prompt action can prevent minor issues from escalating into multimillion-dollar exploits.
- Permanently Update Threat Models: Ensure your tools ingest fresh threat intelligence so you’re protected against novel attack vectors targeting multi-chain systems.
This process doesn’t end at deployment – it’s an ongoing cycle that keeps your protocol resilient even as attackers evolve their methods.
Beyond the technical integration, fostering a culture of security within your team is just as important. Developers, auditors, and protocol operators must stay vigilant for emerging attack patterns and ensure their cross-chain messaging risk scanners are not only operational but also fully leveraged. Regular training sessions and post-mortem reviews of past incidents can dramatically improve your response times and overall protocol resilience.
Best Practices for Maximizing DeFi Protocol Security
- Verify State Transitions: Always validate Merkle proofs and cross-chain message authenticity before accepting any asset transfers. This step is critical to prevent forged messages from draining funds. (Webisoft)
- Implement Robust Authentication: Use multi-factor authentication for validator nodes and bridge operators to reduce the risk of key compromise or insider threats.
- Monitor for Phishing and Social Engineering: Attackers often target bridge users through deceptive interfaces or messages. Educate your community on how to spot suspicious activity. (relay.link)
- Continuous Testing and Auditing: Don’t rely on a single audit; schedule recurring reviews using both automated scanners and manual analysis to catch new vulnerabilities.
- Engage with Threat Intelligence Networks: Participate in cross-chain security forums and subscribe to exploit signature feeds so your scanners can detect the latest threats.
The data shows that protocols employing these best practices experience significantly fewer high-impact breaches. For example, platforms that regularly update their scanner’s threat models have seen a measurable reduction in false positives while catching genuine exploits faster than those relying solely on static audits.
The Future: Automated Cross-Chain Risk Assessment at Scale
The next wave of innovation centers on automation and predictive analytics. Advanced scanners now incorporate machine learning models that analyze transaction patterns across multiple blockchains, flagging anomalies before they escalate into full-blown attacks. These systems are evolving to provide not just detection but also actionable recommendations – such as automated pausing of vulnerable bridges or real-time patch deployment.
This is especially crucial as DeFi protocols grow more interconnected, amplifying both opportunity and systemic risk. As highlighted by recent research (startupdefense.io), the safest bridges are those that continuously test their infrastructure under adversarial conditions, leveraging both human expertise and automated tools for layered defense.
Top Attack Vectors Targeting Blockchain Bridges in 2025
-

Compromised Validator Nodes: Attackers gain control of a majority of bridge validators, enabling them to approve fraudulent cross-chain transactions. This method was infamously used in the Ronin Bridge hack, resulting in over $600 million in losses.
-

Signature Verification Vulnerabilities: Exploiting flaws in the cryptographic signature process allows attackers to forge messages and drain assets. The Wormhole Bridge exploit is a prime example, leading to approximately $320 million in losses.
-

Replay Attacks: Malicious actors reuse valid cross-chain messages or transaction hashes on different blockchains to duplicate asset transfers. Modern risk scanners now compare payloads and hashes across chains to detect and prevent these attacks.
-

Smart Contract Vulnerabilities: Bugs such as re-entrancy, improper access controls, or unchecked external calls in bridge contracts can be exploited to siphon funds. Tools like the Cross-Chain Security Analyzer help identify these issues across multiple chains.
-

Phishing and Social Engineering: Attackers trick users or administrators into revealing private keys or approving malicious transactions, often through fake bridge interfaces or deceptive messages. Security best practices and user education remain critical defenses.
If you’re building or maintaining a DeFi protocol today, integrating a modern cross-chain messaging risk scanner is no longer optional – it’s an operational necessity. By combining comprehensive vulnerability scanning, real-time monitoring, replay attack detection, dynamic risk scoring, and up-to-date threat intelligence feeds, you dramatically reduce your exposure to catastrophic losses while setting new standards for transparency and user confidence in the ecosystem.